Intel Software Guard Extensions (SGX) provides a layer of cryptographic security that extends beyond traditional network and storage encryption. SGX, available on Intel Xeon processors, makes it safer for organizations to process their most sensitive information, including medical records, financial transactions, and encryption keys. How? By creating a secure enclave that protects data while it’s being used in memory.
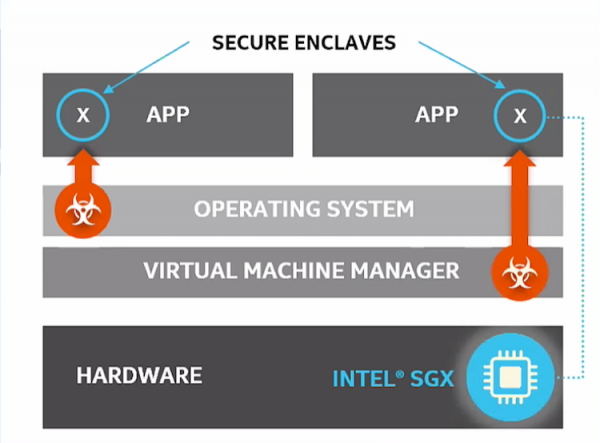
SGX works by instructing the Intel processor to carve out or allocate a portion of memory at boot time. This memory, which is isolated from any other process, is dedicated to an application and its data. Data in the enclave is encrypted to prevent snooping or exposure, even when being processed by an application. That means if the operating system or hypervisor is compromised, the application and data running in the enclave are secure. The upshot is that an organization’s most sensitive data can be operated on by an application while still being protected from malicious software or intruders.
Note that SGX only uses the memory specifically allocated to it–any memory not set aside for SGX will be available for other processes. SGX can create enclaves of up to 512Gbytes per socket.
The SGX capability can be used on-premises and in the cloud. In the cloud, both Microsoft Azure and IBM Cloud support the use of SGX.
Organizations already rely on network encryption to protect data being sent to the cloud, and encrypted storage to protect data at rest. SGX enables cryptographic protection while an application runs in the cloud. The secure enclave ensures a safe operating environment even if an organization is unsure about the OS, BIOS, or other elements of the compute stack.
Thus, applications or processes that might normally be restricted to the data center due to security concerns or regulatory requirements can now take advantage of cloud services and cloud scale while ensuring a high degree of trust and protection, even on compute nodes that the customer doesn’t own.
In addition to protecting data while it’s being processed in memory, SGX can also be used for attestation–that is, to verify that the compute environment is running known and trusted code and that all modules are up to date. This attestation can happen remotely, adding another layer of trust for organizations that are sharing data with partners or running applications in the cloud.
SGX – What Is It Good For?
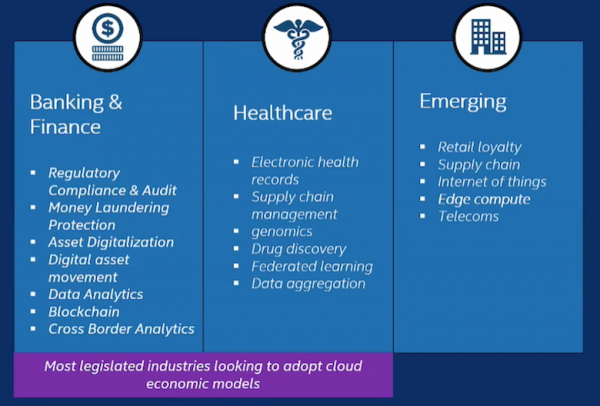
Intel’s SGX supports a variety of use cases. For example, hospitals or universities doing medical research can collect patient records within an SGX-enabled secure enclave and run those records through an AI or ML application to extract insights. At the same time, the enclave ensures patient identities are protected from exposure, whether malicious or inadvertent.
Banks and financial institutions can gather financial transactions or credit card data within a secure enclave and analyze them for fraud or misuse, while also meeting regulatory requirements to protect customers’ Personally Identifiable Information (PII).
One Intel customer uses SGX as a form of insurance against ransomware. Ransomware works by tricking an end-user into triggering malicious code that encrypts a company’s computer systems, rendering computers inoperable and business records unreadable. The attacker then demands a ransom from the victim in exchange for the decryption key.
To protect against ransomware attacks, this particular customer takes snapshots of its server operating systems and stores those snapshots in a secure enclave. If they fall prey to ransomware, they can simply restore the servers using the snapshots, which are protected from attack within the enclave.
Intel partners with independent software vendors to create applications and services that take advantage of SGX. For instance, a company called Fortanix has developed a Runtime Encryption Capsule (REC) that uses SGX. The REC creates a secure environment that can be used for applications such as a key management service.
Things To Note
Customers interested in SGX should note that applications need to be able to detect SGX at runtime, so an additional set of instructions will be required for an application to work with SGX. If you’ve written an application to work with SGX on previous versions of Xeon, Intel says that the application will still be supported across generations, including its latest Ice Lake release.
Customers should be aware of potential performance hits. Intel doesn’t provide specifications on the impact of SGX on CPU performance because it depends on the application and how it’s written. That said, any time data enters or exits the enclave, it’s encrypted or decrypted, so a small performance impact should be anticipated.
For more information on SGX, check out this Tech Field Day roundtable conversation with Scott Raynor, Security Application Engineer at Intel.