Not so long ago, perimeter-based security used to be the only form of security needed to guard corporate environments. That was until lateral movement became a common trend in cyberattacks. Bad actors slipped past security at the gate and freely gained command and control of the environment.
Breaking up the environment into secure zones with microsegmentation reduces the risk of unauthorized access, and curbs free movement of entities. Microsegmentation works by limiting access based on need, and provides granular protection by placing security at the inner perimeters.
“Every single cyber security standard has said to segment the network,” says Dana Yanch, director of TME, at Elisity. “It’s a great first place to start.”
But companies have had microsegmentation solutions for years without significant adoption. The projects are prone to failure, say CISOs.
In a survey, Forrester investigated the reason. They found that the primary cause microsegmentation projects get discarded or derailed is snowballing complexity.
“It’s such a massive project and there’s so much complexity in the deployment of some solution to solve those problems that it gets put on the back burner,” says Yanch.
Microsegmentation drops more tooling on the lap of operators than they traditionally had that they are now in charge of managing. The management overhead surges up staggeringly leading to a quick analysis paralysis.
Other leading causes microsegmentation projects are killed off prematurely are insufficient visibility of the environments leading to enforcement anxiety. Being deeply disruptive, the projects end up getting a lot of pushback from the staff.
Policy Management Made Easy
In the last quarter, Forrester named Elisity a “strong performer” in its evaluation report on microsegmentation solutions.
An identity-based microsegmentation platform, Elisity is a software-only product that is designed to make microsegmentation for LAN click-button easy. The platform works by discovering users, devices and applications on the network, and matching them to the right policy, before enforcing the policies on the infrastructure.
“The goal is to mitigate the risk as quickly as possible, as efficiently as possible without any disruption to the business,” Yanch says. “The long pole in the tent of deploying a solution is eliminated”.
The platform, Elisity says, is a zero-impact deployment. “We can deploy it without a single second of disruption, not one packet lost, not one outage; you don’t even need change windows.”
Elisity has helped many organizations on segmentation journey to stay on track and achieve the ends at minimum friction and effort.
One example is GSK, a leading pharmaceutical manufacturer with a very large and complex network. GSK’s attempt to do segmentation the traditional way had ended in a disaster with nearly no progress made in 3 years.
“GSK was stuck in an analysis paralysis mode. We came onboard and helped them visualize what’s going on in their network across both their IT and OT environments, and pull it together,” he says.
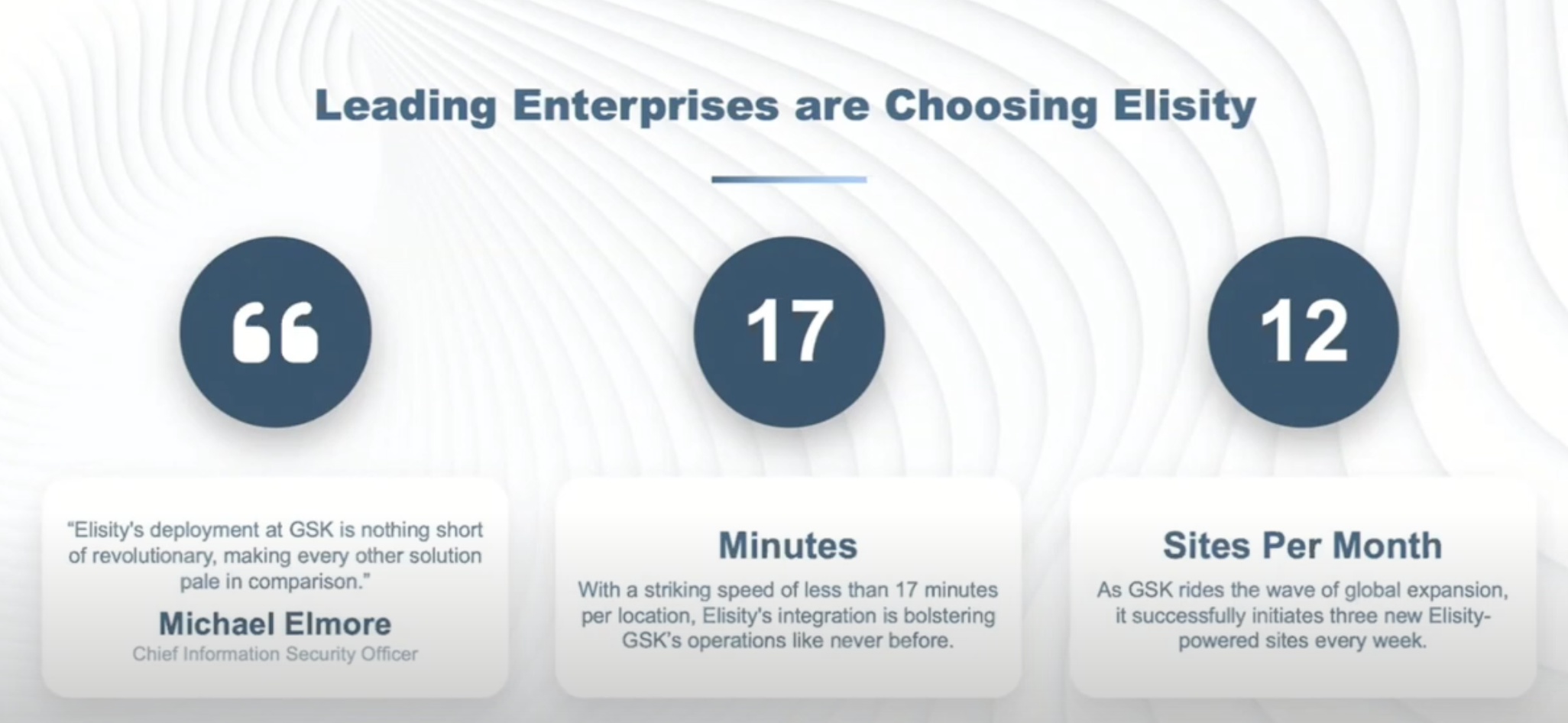
According to Yanch, GSK now deploys sites at 17 minutes a site, going at 12 sites a month.
Elisity is clear-eyed about “time to value”, and as a result has a very quick and short sales process. It takes half a day for the Proof of Concept, compensating for minor errors and issues, says Yanch. How?
“A lot of the complexity that we’re used to doing in Proof of Value or deploying a solution has been packaged up and delivered as a service in the cloud,” he explained.
At Networking Field Day in California, Yanch took the audience behind the scenes to give a sneak peak of the process flow.
A cloud-delivered interface that serves as the main UI allows administrators to integrate cloud and on-prem solutions with Elisity. Elisity aggregates all identity information from third-party devices like discovery engines, databases, and even spreadsheets that some customers use to this day to store device attributes, and pull that into “one simple view and an easily digestible platform.”
“We don’t just ingest; you can export everything that’s been ingested and processed outbound. We have a very robust API mechanism to export absolutely anything in our product.”
Elisity’s IdentityGraph is a critical component of the solution. It’s an asset engine that triangulates accuracy and serves as the source of truth.
“If you’re doing identity-based and context-based segmentation, the platform that you’re using better have the best view of absolutely everything on the network, whether it’s a user or device.”
That’s what IdentityGraph provides, “the full picture” that tells operators what devices are verified, and which are not, what needs remediation, and what needs to removal. The contextual information from IdentityGraph also guides policy group implementation at a later stage.
Assets, depending on the policies, are grouped under policy groups. When a new device is discovered, it is automatically matched to a group based on the pre-created criteria on the device, and the policy is enforced.
“When it comes to enforcing, everybody’s a little afraid. Nobody wants to accidentally shut down a manufacturing line, or cause an outage where the company loses money.”
Elisity aims to build confidence by transparently showing administrators exactly what policy is enforced, when they are ready to hit the button.
A built-in analytics and reporting plane within the Elisity platform offers insights and tells “what’s real, and what’s rogue” before feeding the data into the CMDB tool in use.
Yanch told that the platform continues with the same level of full-time equivalent (FTE) even when the network grows.
For more, be sure to watch Elisity’s presentations from the recent Networking Field Day event.

