In just a few years, campus networks have undergone prolific transformation. The wave of IoT and edge has brought home an unprecedented number of devices and connections and just like that, the campus has become a teeming ecosystem of digital users. A change mostly for the better, it also has made security breaches more probable. Without so much as the slightest indication, a camera or a sensor sitting in the network can become an internal attack vector. That is the premise on which the Zero Trust Network Access (ZTNA) is based.
At the recent Networking Field Day event in Santa Clara, California, Pica8 showcased the Pica8 Network Platform that thwarts bad actors by building logical access boundaries around network assets with context-based ZTNA.
The Campus Needs a New Attack Surface Management Tactic
The attack surface is expanding with the sudden growth of connections. From the moment a user or device is hooked to the network, it can start to compromise assets and eventually exfiltrate data until someone notices. Hackers have successfully orchestrated lateral movements infecting resources without operators having a clue.
The new campus fabric needs inside-out protection. Traditional security models that worked yesterday won’t cut it when confronting new and evolved threat mechanisms. We’ve seen attacks unfolding from inside the network enough times to know that the threat is not just on the outside.
Secure Remote Access with ZTNA
The concept of Zero Trust Network Access was born to contain this reality. Based on the principle of “never trust, always verify”, it has proven to be the model of choice to protect digital environments from bad actors. Pica8 furthers this mission with its network automation solutions that verify every entity trying to gain access from inside the network or out, without trusting anyone by default.
Born in 2012, Pica8 emerged as the open networking alternative to Cisco and Juniper Networks. Its network platform is a single-license software solution that has a buy-once-use-forever model. The platform can be run anywhere using the same license, no restrictions on port-size or performance. An old license can be reused over and over for new devices. It requires no additional fees to upgrade, or install a patch.
Zero-Trust Networking with Pica8
At the recent Networking Field Day event, Pica8’s Technical Marketing Manager, Mani Subramanian gave an overview of the Pica8 network platform and explained how it helps build that Zero-Trust network.
Pica8 separates hardware from the software providing enterprises the tools required to create a Zero-Trust network. The Pica8 network platform has two halves- the AmpCon Automation Network Controller and the PicOS software switch. Pica8 calls AmpCon “the automation command center” of the enterprise network.
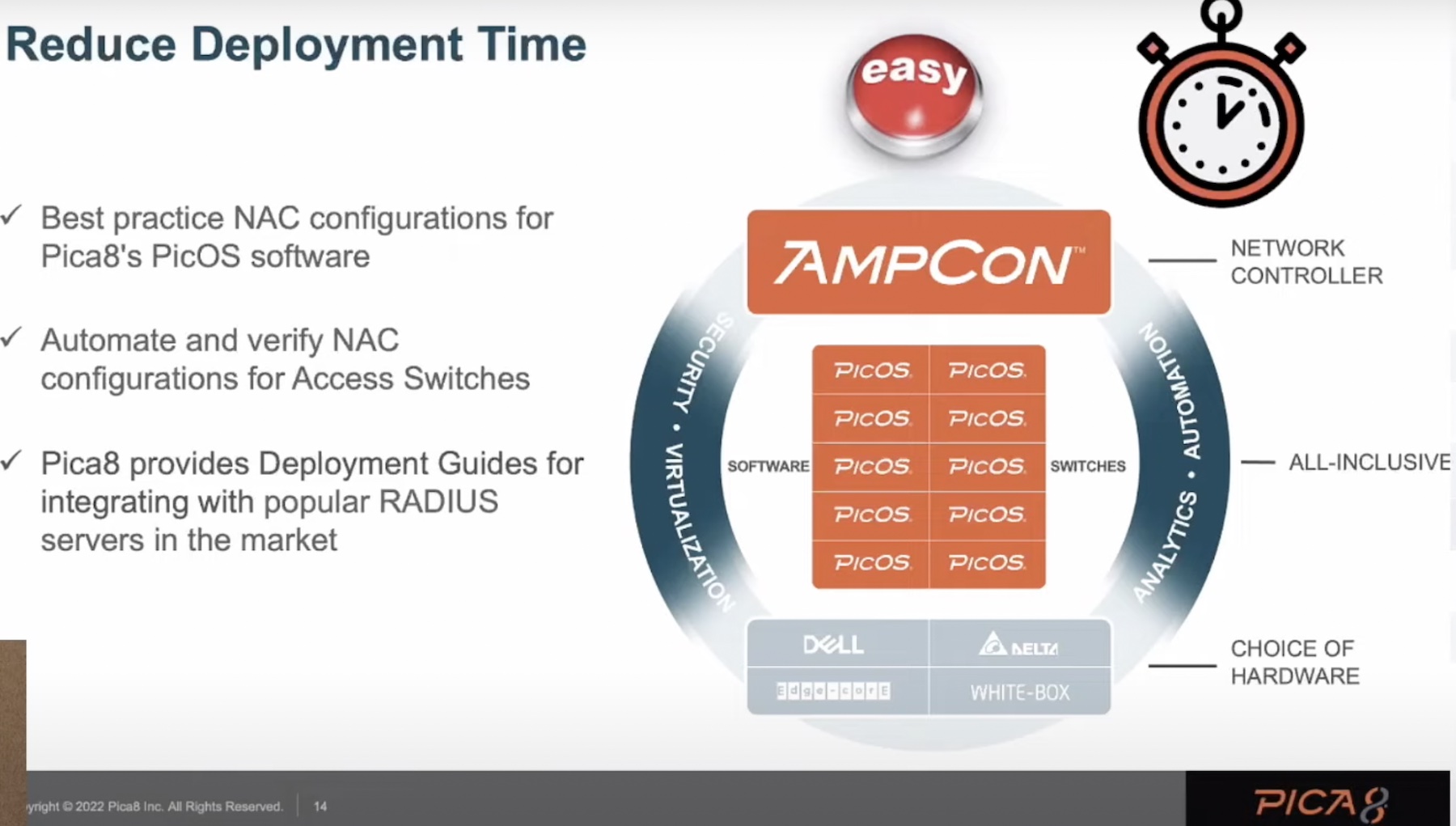
To cut down deployment times and to provide hands-off deployment of switches, Pica8 provides best practice NAC configurations and deployment guides. Its automation tool AmpCon provides push-button automation for full lifecycle management. With AmpCon, users can set backup and upgrades to autopilot during unmanned hours. Another important capability is DIY automation with which users can build custom workflows to easily automate work processes.
With the AmpCon controller, security and network policies can be clearly defined and fully automated. As part of provisioning, Pica8 secures bare metal switches beforehand with “least access” policies that limit users and devices to their respective sections of the network.
Pica8 delivers secure wired access by adopting different identity-based authentication policies separately for users, devices and multi-host, depending on whether it’s an employee, guest or contractor requesting access. Pica8 supports two policies- Dynamic VLAN and Dynamic or Downloadable ACL. The RADIUS server is centrally configured, with the policies applied to the port so that access is limited right from the beginning.
The PicOS Switch Software is a Networking OS (NOS) of open architecture. Its main function is to convert a disaggregated white box hardware into a networking switch. Pica8’s goal with the PicOS is to provide network virtualization for EVPN VXLAN across campus and datacenter fabrics.
With use cases spanning campus to data center, branch and edge, the Pica8 network platform can be deployed flexibly no matter the network. Pica8 also uses third-party NAC controllers from HPE and Cisco.
Wrapping Up
Pica8 network platform is a great tool to start building a bulletproof Zero Trust network. It helps create and clearly define Zero Trust access control policies that are critical to protecting network assets from malicious threats. With it, users can dynamically enforce polices, customize automation and fully leverage the benefits of software-defined networking.
To learn more about Pica8 network platform, be sure to check out the full presentation and other Pica8 demos from the recent Networking Field Day event.

