From being a phantom menace, ransomware attacks have escalated to a global scare within just a few short years. The typical nonsense left in the wake of cyberattacks has compounded to doom-and-gloom stories of illegal and unrestrained data harvesting. With alarming regularity, cyber cartels gain foothold in enterprise environments and set off shutdown attacks, disrupting and paralyzing organizations. At the heart of this crisis is a banal thing – identity.
Researchers have found that in the recording-breaking number of security breaches that have emerged over the past couple years, cybercriminals have exploited a simple opening – identity and remote access.
So we met with BeyondTrust, an identity security company that is rapidly expanding its footprint across the global cyber security market, and who recently announced a new solution, Identity Security Insights, in an effort to wrap our heads around this brewing storm. We sat down with Marc Maiffret, Chief Technology Officer, to get into the depths of identity and access management.
Beneath the Surface
In the pandemic, a bulk of businesses set up their workforces with remote access. This ensured continuity of operations through a trying time. Access to internal resources over public and private networks began in earnest. But things took a precarious turn soon after.
New tools and technologies were adapted over the course of the following years. Companies migrated to cloud, and digital transformation kicked off at a sweeping scale. From hundreds, the number of entities remotely accessing enterprise data swelled to millions. These, beside employees, are contractors, clients, vendors, business partners, et al.
The wholesale distribution of access privileges with no regard to security brought home a swarm of bad actors. Incidents of identity theft, social engineering and remote access exploits began to soar, and soon became the top entry points. The attackers had their hands on the skeleton key to unlocking all data vaults, identity and access. It’s quite easy to find a way in through internal process silos and cultural divisions when impersonating as a legitimate users, said Maiffret.
He called attention to non-human identities which are particularly easy to compromise. They don’t change passwords often enough, and log into servers at odd hours, he said.
Need of the Hour
The risks of the remote mode of work have become amply clear post-pandemic. What’s emerging from it is a growing consensus around redoubling identity security.
Passive defense strategies and perimeter securities are grossly insufficient to combat identity-based threats because here, the threats reside inside, said Maiffret. The key to keep cybercriminals out is to ensure that at all times, the right people who have the right credentials get access to the right information.
The market is bursting with a growing number of security solutions that promise to reverse the situation, and despite companies uplevelling their cybersecurity solutions frequently, they are left with a growing tools wish list and a stretched-thin security budget.
Cyber events remains all too common, and attackers’ success rate is on a high upward curve. What’s working in favor of the bad guys is the multiplicity of internal vulnerabilities like identity. Identity insecurity not only weakens the overall security posture, but also wears off the affectivity of existing security frameworks like zero-trust.
BeyondTrust Identity Security Insights
BeyondTrust’s Identity Security Platform prevents identities from being stolen or compromised. It combines privilege management and threat detection into a single solution, making it the only product of its kind. The platform’s zero-trust architecture eliminates troubles spots existing in the network that can be potentially converted into attack vectors thus making the environment safe from within.
BeyondTrust topped that with an intelligence layer – the Identity Security Insights solution. Securely connecting identities to resources is a complex process, especially in an environment where millions of users are constantly accessing and sharing critical information. Without comprehensive visibility of all human and machine identities, it is a zero-sum game.
BeyondTrust’s new solution provides users a single view into all types of identities, and their permissions and access rights across public and private cloud environments, and control over their use. This allows administrators to enforce security granularly by granting and denying permissions all from the platform’s single console.
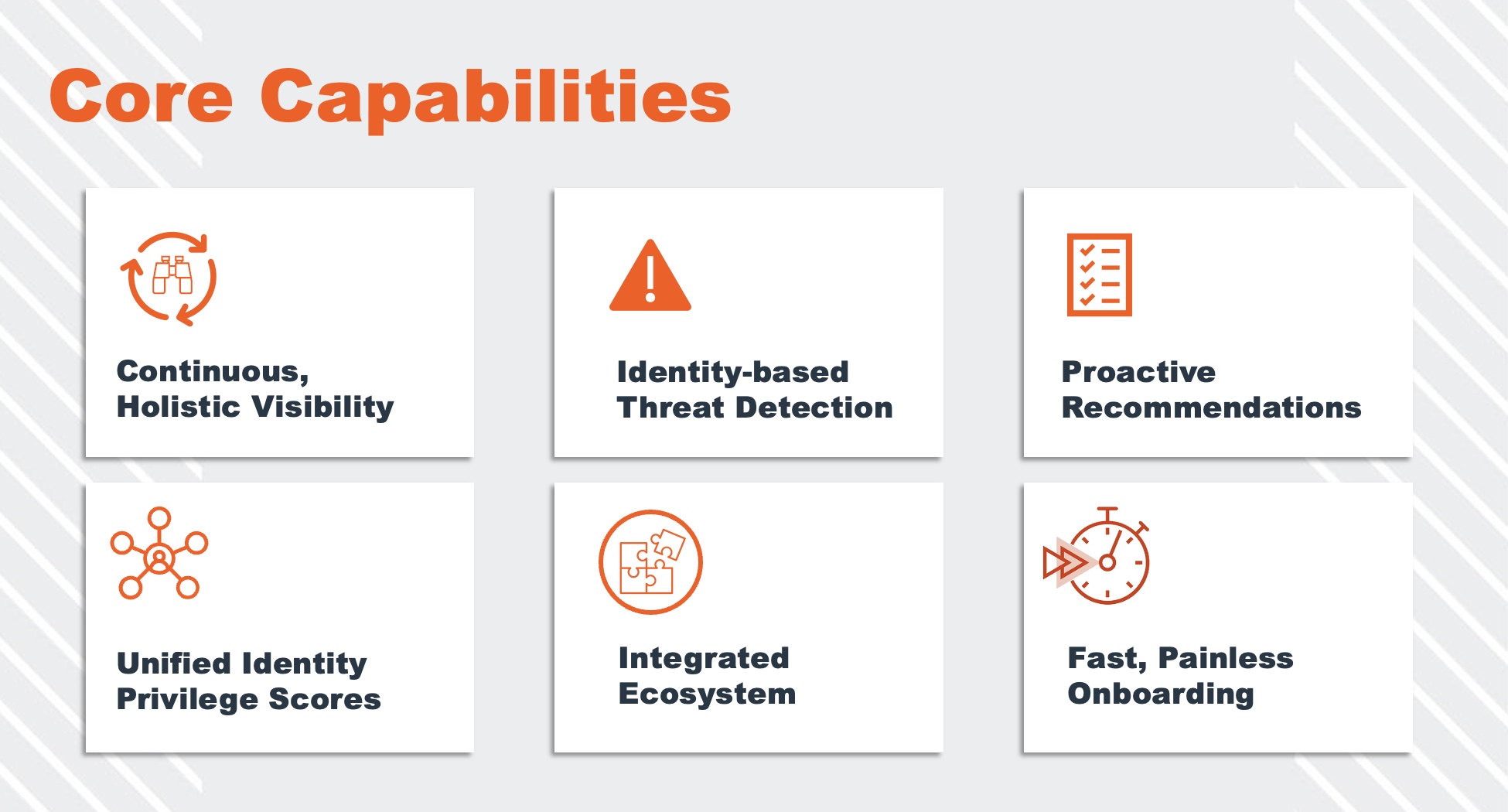
Included in the feature set is an identity-based threat detection capability. It works by spotting identity-based anomalies, and generating proactive recommendations for instant remediation. For example, if it discovers any over-privileged accounts or unmanaged admins in the network, it would immediately report to the relevant teams, prompting an immediate correction. A lot of organizations have employees that use personal emails for recovery. This solution sniffs those out, helping remove all weak spots.
Identity Security Insights streamlines the findings by performing a risk score analysis with machine learning which ranks alerts based on severity. Thus, IT teams not only have shared visibility of the threats and gaps, but also the ability to diffuse an organized response when required.
This deep visibility underpins all accesses happening in the environments, unlocking an oversight otherwise hard to achieve in heterogenous and distributed environments.
Deployment is fast and painless. Identity Security Insights can be up and running within 30 minutes,. It starts generating insights the very same day.
Wrapping Up
More than half of security breaches today are linked to identity issues stemming from low visibility. BeyondTrust Identity Security Insights dials up the clarity by giving IT teams visibility into all trouble spots around identity and access, and helping adopt a unified management posture. This is not just better cyber hygiene. It is enforcing the core tenet of zero-trust – a fully secure access model.
For more resource on this, check out BeyondTrust’s website. For more stories like this one, keep reading here at Gestalt IT.

