Firewalls are not the easiest things to manage in IT. Every time you configure a new rule you run the risk of invalidating an older rule or even the whole configuration. Trying to figure out which rules are used for which programs is an undertaking on the best of days and when nothing is properly documented it’s a task of epic proportions. Now, imagine trying to do that across dozens or even hundreds of devices in your enterprise. It’s enough to drive you mad.
Capirca and Aerleon
Recently, I had a chance to sit down and talk to Rob Ankeny and Jason Benterou at Invariant. They’re taking a great approach to solving the problems associated with firewall ACLs. It all started with a little project that Rob worked on at Google called Capirca. Note that’s not caprica because the project had a typo when it was created and they ran with it. Caprica helped Rob and the other firewall engineers at Google maintain ACLs from a normalized data source. Rob left Google and because of that the project stopped being maintained as well as having some questions around the ownership of Capirca.
Rob forked the project into Aerleon, using the name of another Battlestar Galactica planet this time. The project is designed to take data from a normalized set of inputs for policy and addressing and output a configuration for a firewall device. Aerleon works to build the ACLs from inputs and give you output that can be used in any supported device. They also modified the language to use YAML instead of the closed format of Capirca. That means you can feed Aerleon a YAML input and you’ll get a configuration that could work for Juniper, Cisco, and more. Without the need to adjust anything manually.
Enter Invariant
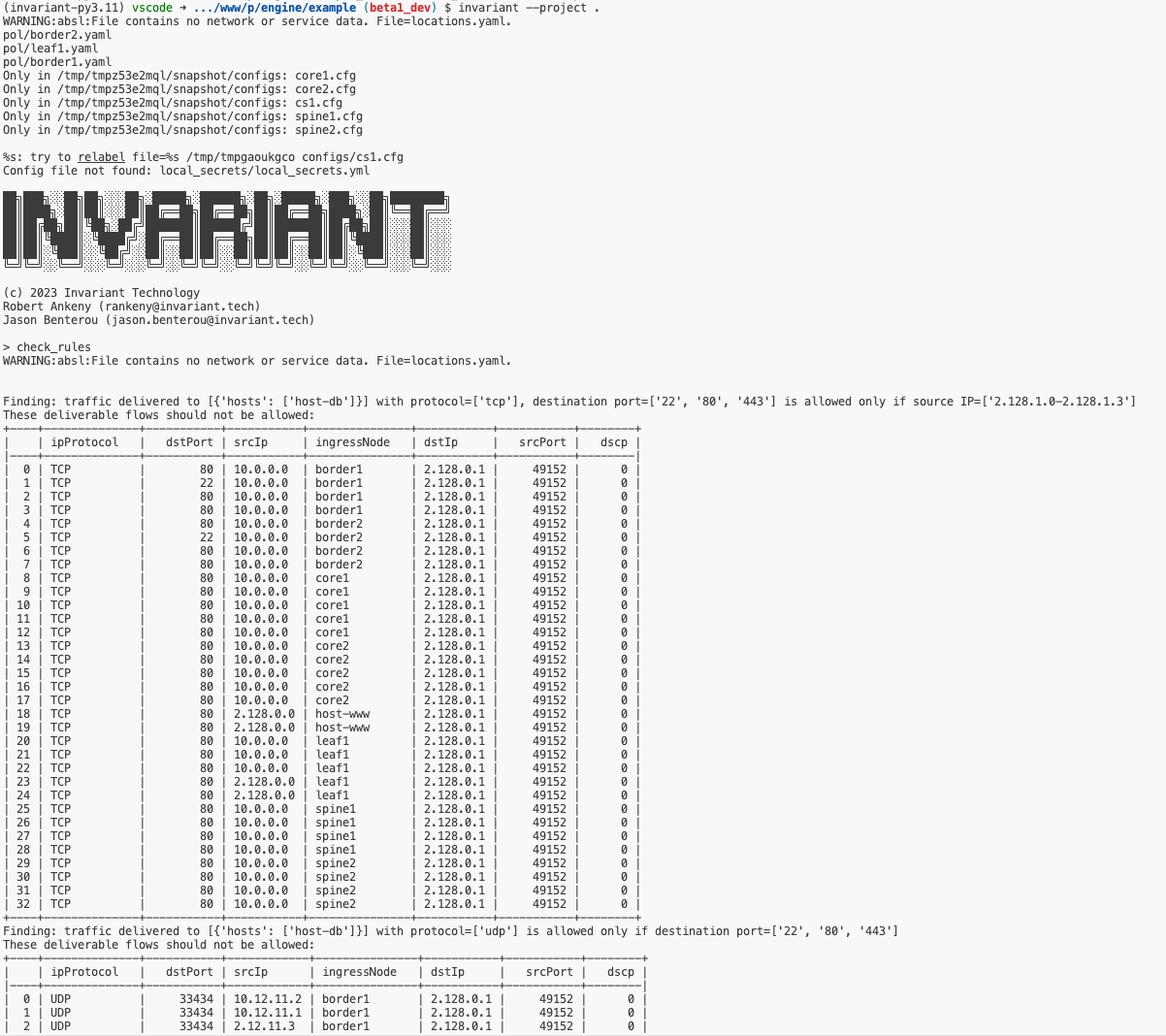
How do we get from Aerleon to Invariant? Well, that involves the introduction of Batfish. Batfish is a validation tool that allows you to take the output of a given configuration file and test it first to make sure it’s not going to break anything. Just as important as getting the ACL right is making sure that implementing it won’t cause other issues with other entries or even devices. Batfish could be a whole post in and of itself but it works closely with Aerleon to make it easy for engineers and operations people to ensure that firewall rules do what they’re supposed to do.
Invariant takes the ACL capabilities from Aerleon and uses Batfish to figure out what’s going to happen when you deploy them. It packages it up as a Software-as-a-Service (SaaS) offering that can interpret all manner of configuration files and give you the output that you can be sure works. It scales to more than just a single firewall. Instead of the need to feed the inputs per device, Invariant scales it out to encompass all the devices it can support.
Note that the process for getting Invariant to work on your files is still manual right now. You have to export the configuration and upload it to Invariant in the cloud to get the configuration files you want. It will not directly connect to a device to capture the configuration and Invariant won’t push the configuration back to those devices. Given that the solution is still in the beta testing phase I think this is a reasonable limitation have now. It’s also important to realize that creating the capability to scale Invariant to offer those kinds of services is going to take development time and resources, which Rob and Jason and their team are hoping to get by pricing Invariant appropriately for the market.
If you would like to sign up for the current beta of Invariant and test it out you can do so right here on their home page. Don’t forget to give them feedback about how things work and what can be improved to make this a useful service for engineers and operations teams everywhere!

