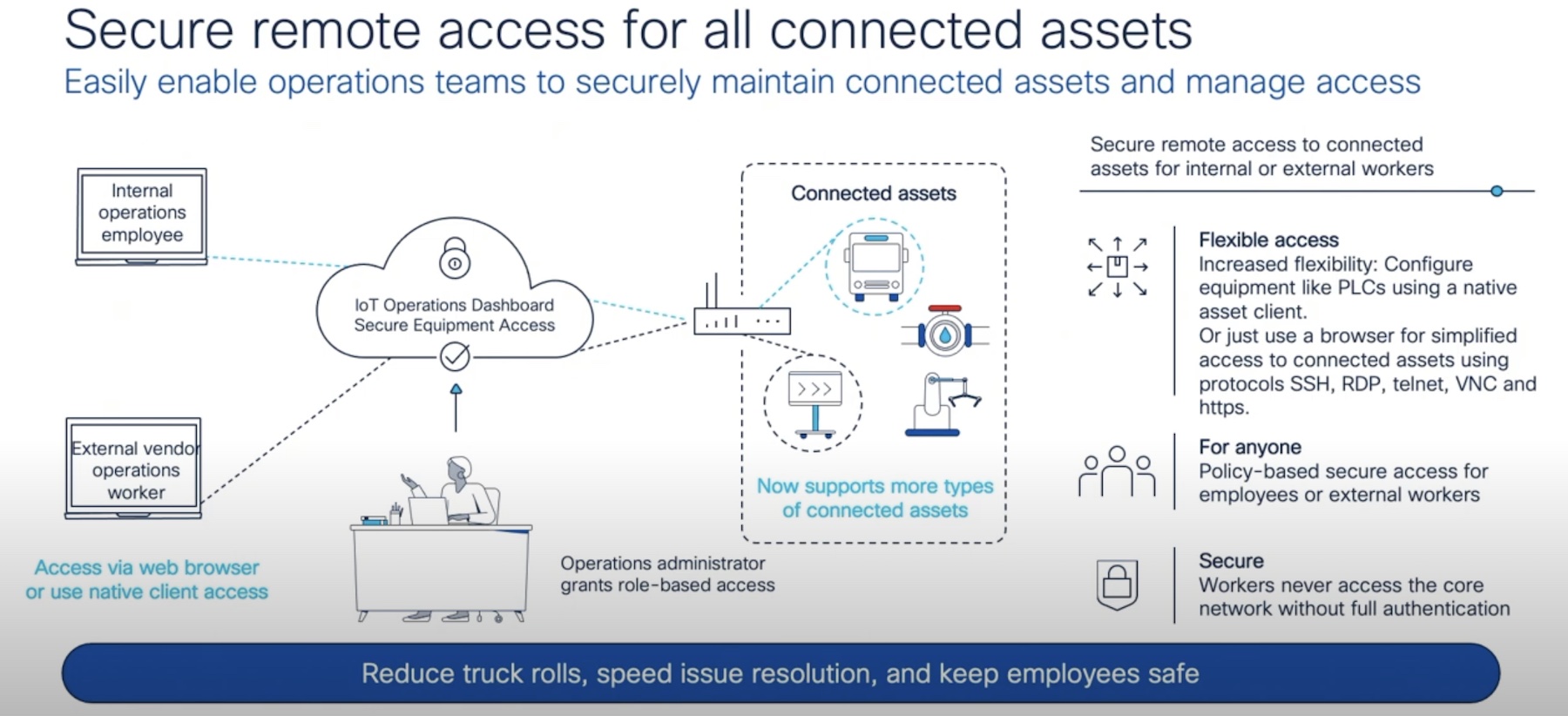
The best network security is the kind where devices are only admitted with proper trust credentials. If you know it’s a device you provisioned or that comes from a source you trust then you can set it up in advance and make it work in a secure manner. If it’s a device that has a trusted user you can also set up the network to have the user access a portal to provision the device themselves and take the burden off your IT department.
But what about those devices that don’t interact with users? The growing number of IoT endpoints in the network is making the provisioning process difficult under the best of circumstances. The more IoT devices you add the worse it gets. Do you trust these devices on your network? Do you trust the labor installing them with the credentials needed to get them on your network?
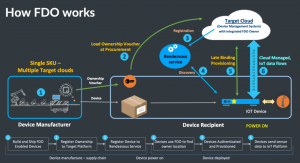
Bruno Wollmann was a part of Security Field Day recently and got a chance to see how Intel is handling this challenge. The FIDO Alliance is working to change the way that devices can quickly identify themselves to the network and gain access without intervention from administrators. Bruno has a great overview of the presentation including thoughts like this:
One of the most significant advantages FDO brings to ZTP is the late binding of device configuration and customization. In the traditional ZTP model, the manufacturer provides an SKU for each customer and multiple SKUs for a single customer in many situations. This forces the manufacturer in a build-to-order model where there can be no stock in the supply chain. Using FDO, manufacturers can build their devices and have them in the supply chain closer to their customers (i.e., at distributers and VARs) because configuration and customization occur when the device is provisioned.
Make sure you check out the entire post for his thoughts on FIDO, FDO, and Intel’s vision for IoT security here: Security Field Day 6 – FIDO Device Onboard (FDO)