If you were affected by the huge Dyn outage of 2016 or if you’ve heard about the massive IoT botnet that was taking down targets, you probably know that as more and more devices are being connected to the Internet, the potential for Distributed Denial-of-Service (DDoS) attacks is growing. With so many “invisible” devices on our networks that are vulnerable to being exploited to act as traffic generators for attacks of incredible size, it’s becoming quite difficult to figure out how to prevent these things from happening in the first place.
Traditional security measures aren’t as effective as we want them to be. Firewalls can only handle so much traffic before they buckle under the load of well-crafted DDoS attacks. It’s also becoming more insidious because attackers are using things like DNS requests to look like legitimate traffic to evade detection. This causes an impossible choice for security people in IT. Do we block the bad traffic, understanding that we might also block some legitimate requests as well? Or do we just let everything pass through to keep our users happy and take the risk that the next big botnet could take us down too?
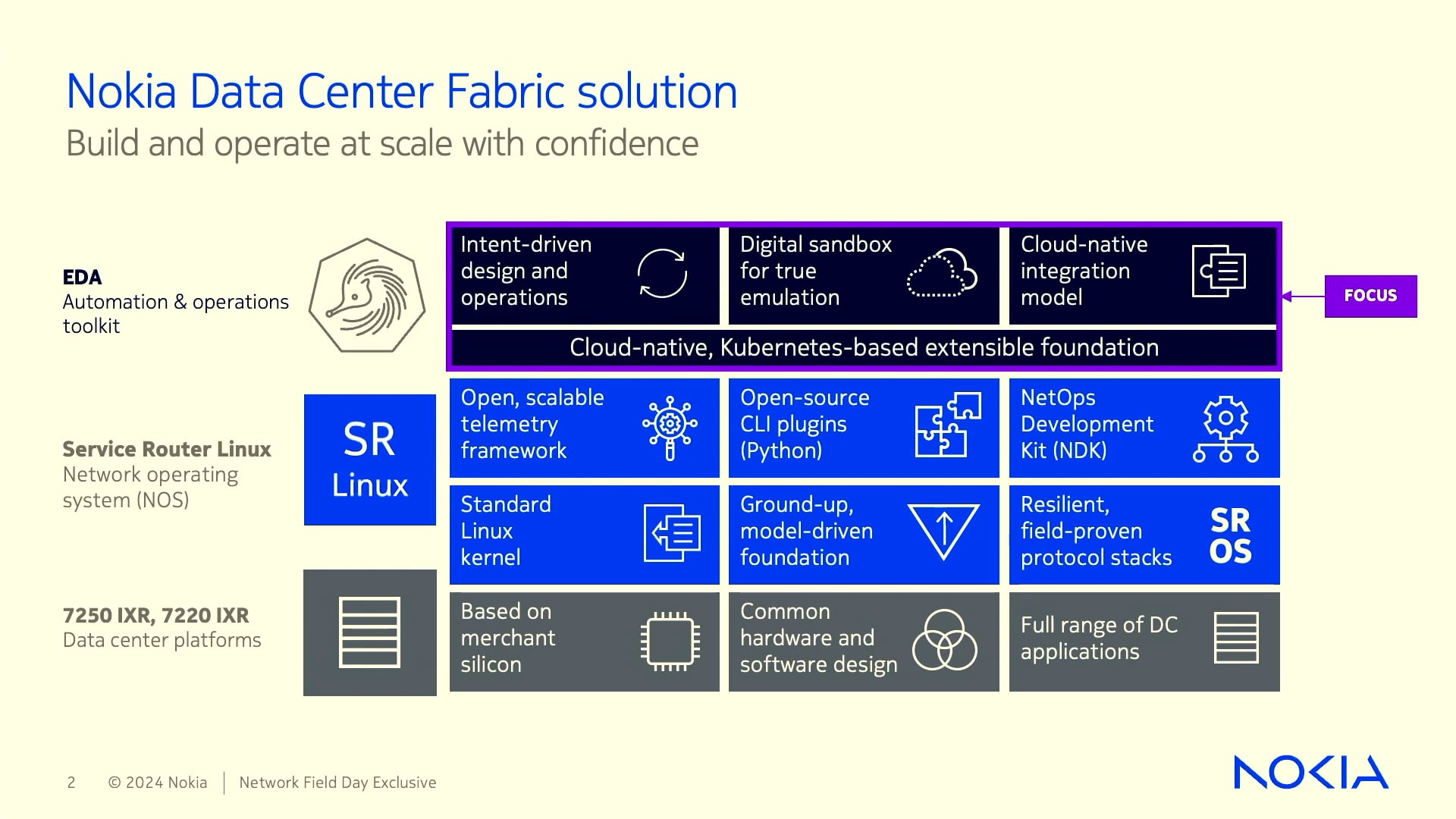
Nokia Deepfield DDoS Prevention
One of the big pieces of the puzzle can come from the network itself. Recently at Networking Field Day 20 we got a great presentation from Nokia. They talked a lot about things like peering security and network analytics. But they rounded out their presentation with a great overview of what they’re doing with DDoS mitigation. Take a look at this video:
Andrew Henkart and Philippe Bergeon do a great job of covering what makes the Nokia solution so unique when combating DDoS attacks.
Rather than looking at DDoS as a security threat, Nokia is trying to solve the problem in the network. That’s because no matter what security you have in place to prevent attacks at the front door the traffic still needs to be transported to your location somehow. But solving the problem in the transport layer, Nokia is effectively giving network engineers the chance to staunch the flow of bad actor traffic rather than just trying to drop it when it arrives at the front door. It’s not unlike channeling water away from a sea wall to prevent a wave from crashing against it.
Nokia is able to do this thanks to the combination of their Deepfield platform and the FP4 chip in their routing platform. Nokia can analyze traffic as it is arriving at the customer site and start to handle it. That’s because trying to stem the tide from the source is almost impossible. The reason why DDoS is so effective is because you can’t filter the traffic from the origin. There are too many IPs, too many autonomous systems (ASes), and far too many hosts to worry about. Instead, you need to be able to screen the traffic as it is inbound to the destination.
That may sound like having a firewall scrubbing your traffic, as it is in today’s world, but it’s something a bit more complicated. Nokia actually looks into the packet itself to find identifiers that would mark the traffic as DDoS-related. That means they can drop the packets before they ever land at the firewall. This is very similar to the difference between applying an access control list (ACL) inbound on an interface or outbound on an interface. One of those methods means the traffic must be processed before it’s dropped. Nokia is simply washing all this traffic through FP4 and using Deepfield to make determinations about it before it ever arrives.
The Future of Securing Traffic Flows
The endgame for Nokia is more than just scrubbing traffic at the router level though. By building out a network with Deepfield-enabled devices in the provider core, Nokia can eventually offer this service to a variety of customers, similar to the DDoS scrubbing systems that exist today. Except, rather than forcing all your traffic to transit a specific AS and add chokepoints in the path, you can have the devices doing the transport actively looking for this kind of traffic as it is happening.
The other huge boon in my mind is that Deepfield allows you to prevent new attacks before they are properly detected by the large scrubbing services. Because Nokia is looking directly at the packets instead of making assumptions about the source, they can see when a huge flood of traffic comes flying in from all over the place with similar characteristics. They can blocks the worst of the traffic through their detection systems and then alert you to know that something new is on the horizon. That’s a huge plus for providers that might not be able to react to the latest IoT exploits as fast as they want to.
Bringing It All Together
Nokia is doing something quite novel with DDoS mitigation. They’re figuring out how to stop it in the transport layer instead of trying to stop it with another security appliance. This solution scales as well, with the potential for it to be built out and offered as a network service rather than just another box that gets installed in your transit path or another DDoS scrubbing AS that could cause path routing issues for your traffic. Nokia is building a platform that has the potential to nullify IoT DDoS attacks without needing to touch the devices themselves. And that’s a huge thing for the future of networking and security.