Commvault Connections was full of amazing content covering many areas that organizations struggle with today. It hit on many of the hot topics in the industry like muti-cloud, Kubernetes and digital transformation. I want to take a closer look at one area in particular – ransomware.
At this point, we all know that it isn’t ‘if’ our organization is struck by a ransomware attack, but ‘when’. The statistics are staggering when it comes to cyber-attacks. Of the organizations that have been hit by ransomware, 25% has been forced to close, and only 4% of those who paid the ransom got back their data. If that isn’t harrowing enough, there’s a tremendous cost associated with ransomware for those who do stay in business.
Downtime costs $11,600 per minute for large enterprises, with the average data breach costing 4.25 million dollars. On average, 1.4 million dollars is the cost for rectifying a ransomware attack. These are costs no organization wants to incur. So the question is, how do they do that?
The time is now for organizations to put a strategy into place to beat ransomware.
Beating Ransomware with a Zero Loss Strategy
Considering only 4% of organizations who get hit by ransomware get their data back, we can do quite a bit better with some upfront planning. This is where a Zero Loss strategy comes into play.
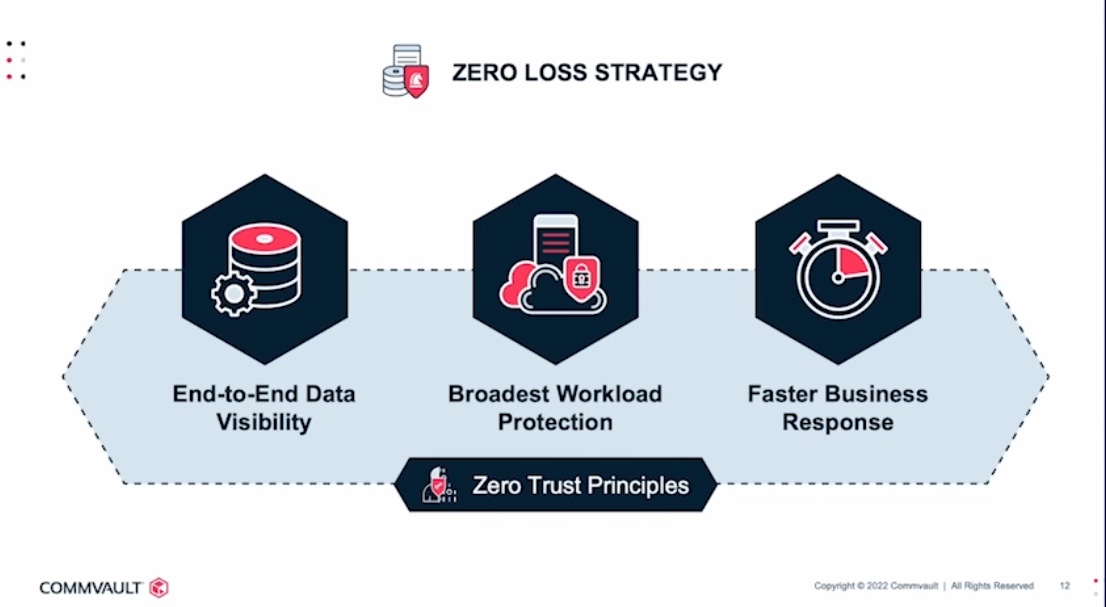
Above are 3 pillars of the zero loss strategy, which is built on Zero Trust principles. Let’s take a closer look at each one of them.
End-to-End Data Visibility
We need to understand quite a bit about our data to ensure we can recover it without loss. This is where Commvault’s centralized management console comes into play. It’s easy to monitor your data and ensure it’s protected across different types of data and across the Commvault product suite.
It’s also important to look at our data for signs of ransomware. We want to know when something has changed as quickly as possible, so we can begin to take actions and mitigate the damage caused by a malicious actor.
Broadest Workload Protection
No matter what your workload is, or where it is, Commvault is able to protect it. This is important because if we aren’t protecting our data now, we won’t be able to recover it later.
Commvault products natively integrate into your favorite cloud, not just to protect data, but also to restore it. We don’t know how exactly a ransomware attack will unfold, so it’s important to have multiple recovery options available.
Faster Business Response
I’m going to let you in on a secret. Traditionally the data protection industry has been built around protecting your data – it’s built around the ability to recover it. When we’re talking about a ransomware attack, we’re talking about large scale recovery scenarios, which means that automation is critical. Not only do we need to automate recover, but we need to keep an eye on things to make sure that we’re recovering healthy files, and our systems remain healthy during the process.
With Threatwise, Commvault’s cyber deception technology to help detect malicious actors faster. Once an attack is leveraged against a decoy, teams can immediately start the incident response process.
This means that we have unprecedented insight into the attack patterns of the threat actors so we can delay the attack, or stop it all together. This streamlines the response process, and reduces the impact of an attack.
All of this is built on top of key principles of zero trust for an added layer of security. Access control and integration with security response tools are a critical part of the strategy as well.
To learn more about Commvault’s strategy for protecting customers against ransomware, be sure to check out all of the great on-demand content from Commvault Connections.

