Imagine for a moment, a consultant walking into your office one sunny afternoon. She’s a technical consultant, maybe a developer supporting a project. She requires full administrative access into a number of servers; others unprivileged will be fine. Whilst some require SSH, others require VNC or RDP. There are also a couple MySQL database connections, and Kubernetes access as well. All for a 6-month contract, after which you will need to off-board her from the infrastructure, reset any credentials she had access to, and validate.
Traditionally, this process required a lot of administrative overhead for Service Desk. Confirming the systems, she required access to creation of an account with the appropriate group, sharing of multiple credentials – many times this was via email – and constant back and forth for missed or forgotten permissions, and confusion on how to access another resource. The onboarding process was frustrating for all parties. Then, just as things started to be figured out, she was out the door and you had to begin resetting these credentials and onboarding a new resource. I remember those days well, both as the internal support and the hired external party – I don’t miss the frustration.
Keeper Security has introduced their Connection Manager, which resolves so many of the pain points above, but takes it a step further – incorporating passwordless and zero knowledge workflows, when paired with their Secrets Manager, and providing a fully auditable, fast, and secure connection to remote infrastructures.
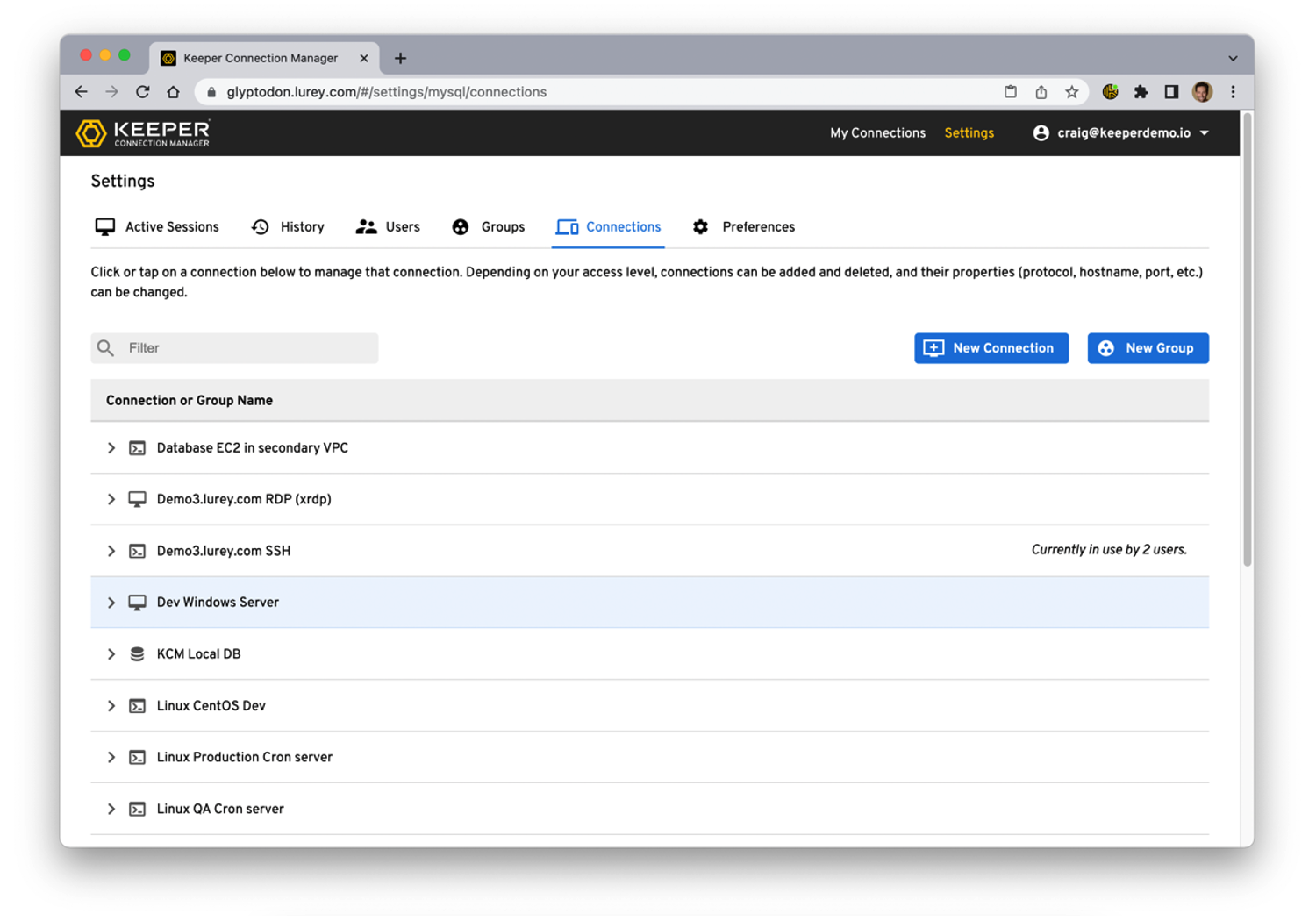
When listening to their demo, what stood out to me was the continuous alignment with requirements, usability, and embedded secure-by-design approach. The Connection Manager follows suite of their other products, zero trust zero knowledge, and after the installation of a gateway, users can connect to required connections through an intuitive web GUI. This agentless approach means it doesn’t matter what device the user needs, they can click and connect via a secure browser connection, and have near instant access to any required resources.
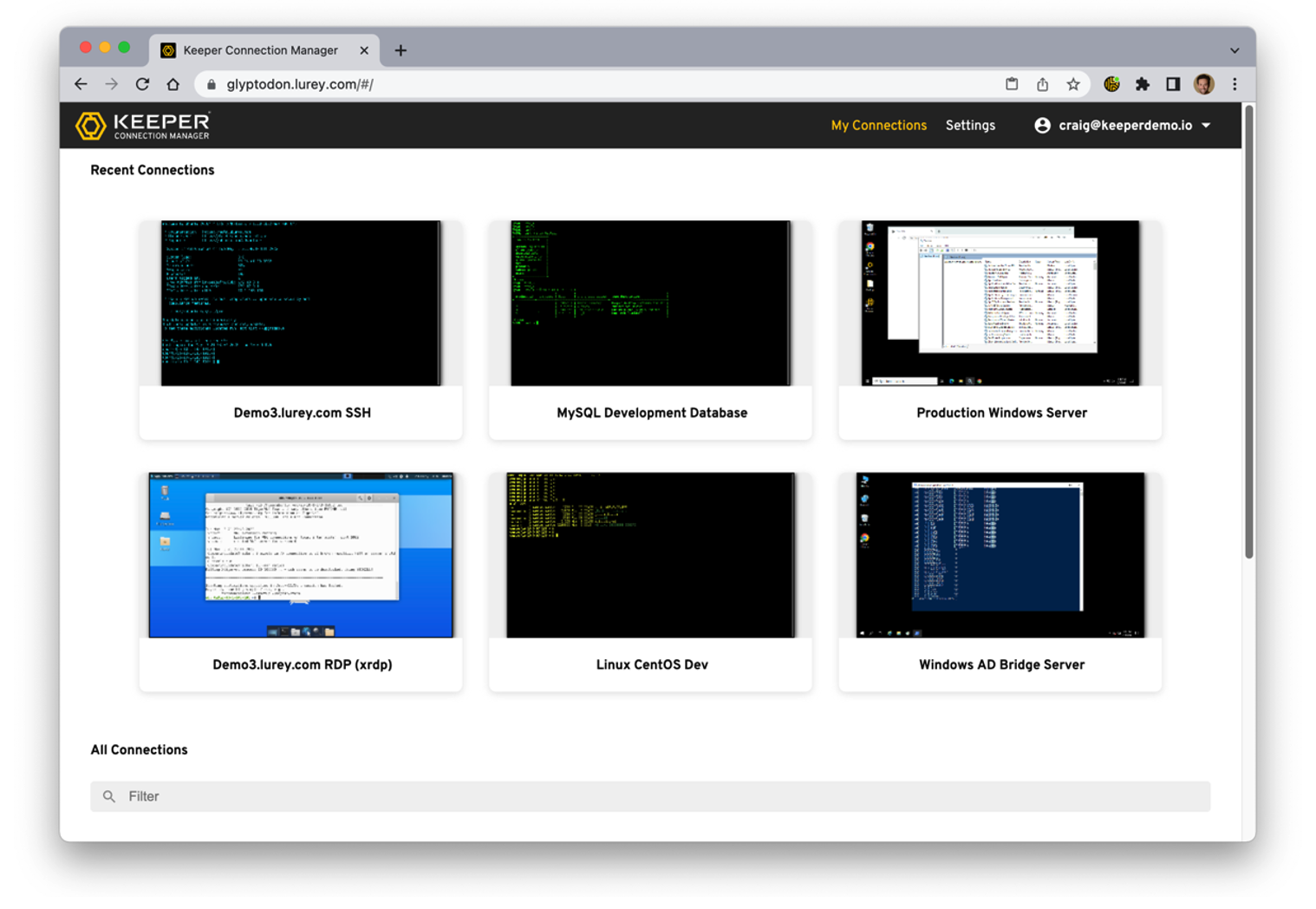
Consider your developers requiring access to multiple servers, some in isolation due to testing with a variety of OS versions. Again, with contracted resources, this requires providing access and sharing of credentials. What are we replacing with Connection Manager? A VPN into the environment, sharing credentials and password rotation*, and remote desktop applications. We’re removing time to connect, so the developer can be more productive – simple click to connect, and they even have the option to send the same command to multiple windows.
A use case I didn’t consider was sharing sessions, easily done via the Web GUI or by sharing a direct link to your session for an outside user – restricted to whilst you’re active.
From an internal support perspective, how do you manage the different users and access? The administrative portal view provides configuring users with role-based access – you can manually enter credentials or make use of tokens that link the hostname to credentials in your Secrets Manager; making it zero knowledge for the user and reducing it to one location for changing if rotation is needed. You can also set accounts to expire on a specific date. Using SSO connection, you can also tie into existing authentication. Meaning you can realistically remove user generated passwords, maintain your secure-by-design strategy, and create a passwordless remote infrastructure access.
Security by design and by default is hard, especially when it requires multiple steps and changed behaviours to implement. Taking this tooling, you’re decreasing steps, automating processes, and enhancing the user experience. That barrier to use is almost non-existent, and provides a brilliant experience to the users – which means long term use and reduction in shadow IT.