Tamper-evident technologies have existed for decades on food and drug packages. We see them every time we open a new bottle of over-the-counter pills, or crack the bond of that ring of plastic attached to the milk jug lid. They are there to assure us that the product inside has not been tampered with or altered. They are there to prove the integrity of the thing we bought.
Technological Integrity
Similarly, IT supply chains are important to ensure the integrity of the products we use inside our datacenters. This integrity is part of the CIA security triad (confidentiality, integrity, and availability) that can be used to secure data. Determining the integrity of the system should include verifying that the system is exactly what the manufacturer intended it to be, without manipulation.
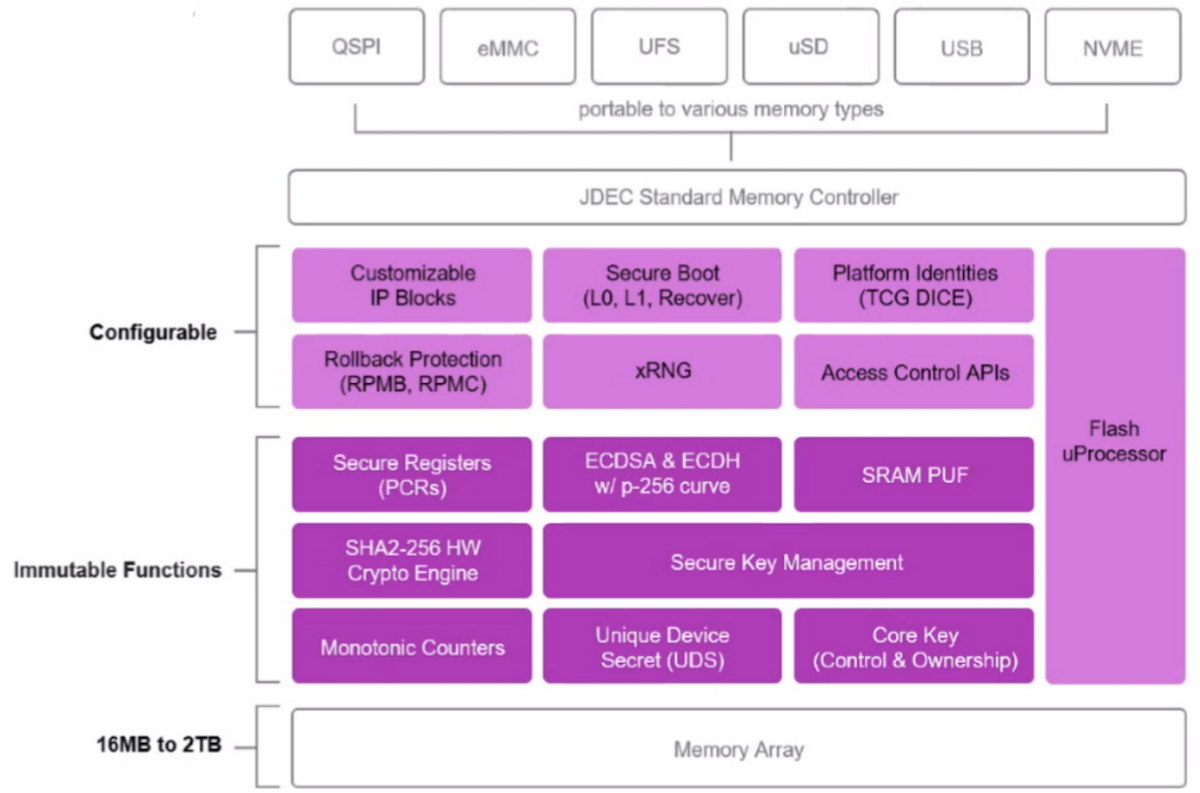
For items like Internet of Things (IoT) and Operational Technology (OT) devices, the integrity of the product is generally a combination of the hardware, OS, and applications, which rarely changes and is defined during manufacturing. Nonetheless, proving the integrity of these systems can be complex due to the variety of silicon, manufacturers, and ownership transfers that exist in the build and supply chain of these devices.
Verifying Integrity with Micron Authenta
This is the challenge that Micron’s Authenta platform was designed to solve. With this technology, integrity can be verified through a combination of technology embedded at the lowest level of the system and an external certificate that can be combined to provide verification of the system.
The first part of the solution is the Authenta Root of Trust. This is a secure element that is embedded into standard memory products. Each element that Micron manufactures has a digital key that can attest to the hardware configuration throughout the manufacturing process. Utilizing this key, the OEM can create a certificate that can ensure the storage on the device contains a known-good image and unaltered hardware configuration prior to booting.
Device integrity can also be validated while the device is booted and in use. Even more powerful, since the element is built into the data path of the system, it can actively block attempts to modify protected sections of storage.
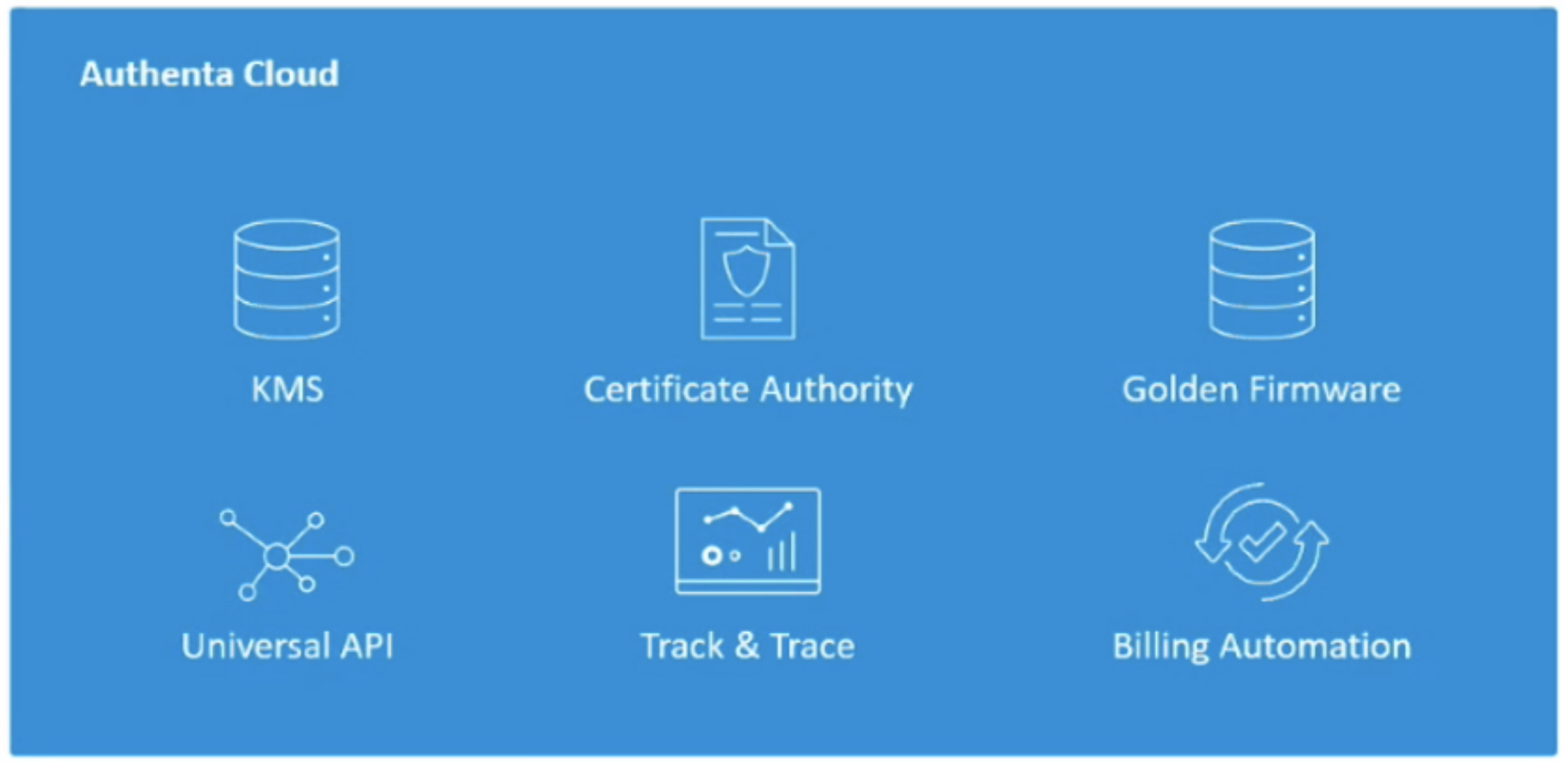
The second part of the solution is the Authenta Cloud. With Micron’s manufacturing capabilities, they can easily build trust in the silicon, but there still needs to be a secure and scalable way to share the keys and store the device certificates across the lifecycle of the device. For that, Micron created and operates a cloud service that provides a cloud-based key management system (KMS) and certificate authority. Utilizing this system, any trusted partner in the supply chain can validate that the device they’ve received has not been tampered with, and update the certificate that can be used to verify the system they manufacture.
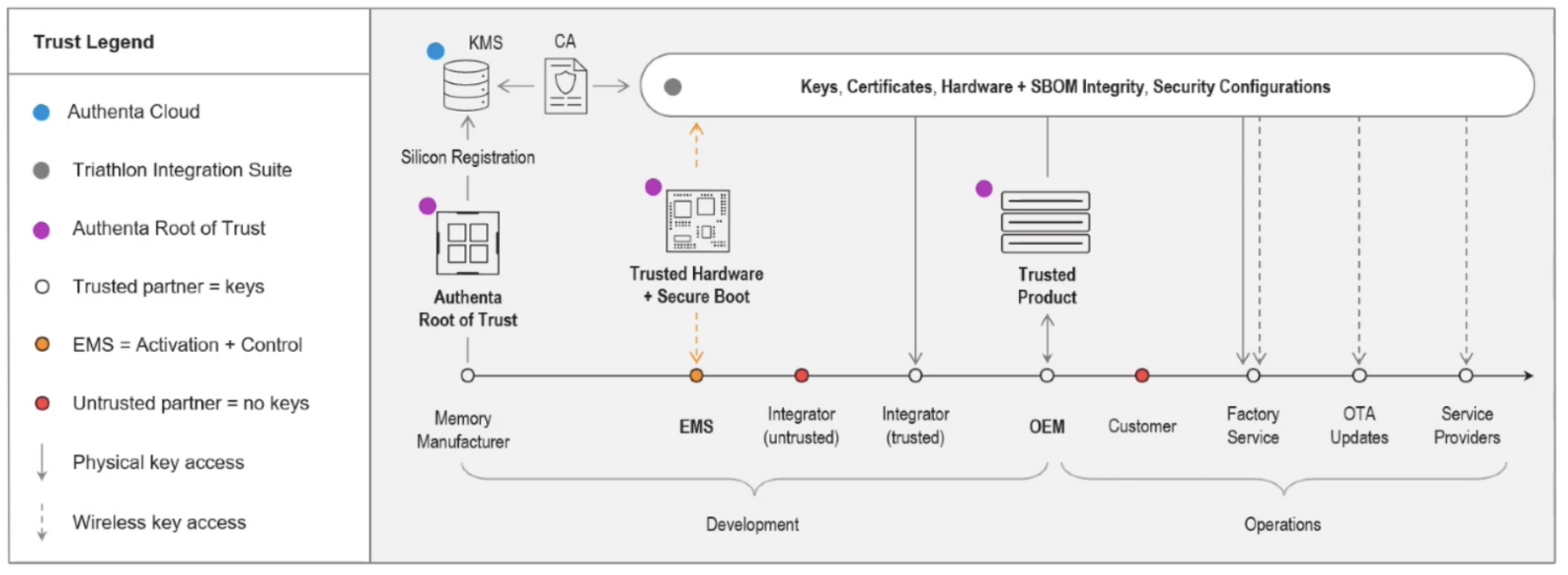
When creating the Authenta technology, Micron didn’t set out to force OEMs to use a specific system in order to participate. With heavy emphasis on APIs, the Authenta system can be utilized within the OEM’s existing manufacturing systems. This includes the ability for the key and certificate to be transferred through a closed, pre-existing, or non-cloud system. The most important element is that they are transferred independent of the device itself, thus creating a bifurcated supply chain that can be used to validate each other. With this model, both branches would need to be compromised in order to create an undetected supply chain attack.
More Than Just a Safety Seal
In the end, we can imagine a security camera or smart lightbulb that can be constantly checked for manipulation and verified to not contain any unintended hardware or software. With a “golden config” stored and checked in the cloud, OEMs could even deploy updates and new features over-the-air automatically. With Authenta running within the flash device, malicious writes can be completely prevented or overwritten with the golden config on the next boot.
This ability to provide automatic, silicon-level integrity can be an important element of a zero trust architecture. It provides zero trust in the device before it boots up, with Authenta providing the ability to verify it as a trustworthy configuration.
While it’s still important to spend time ensuring that users are buying from someone they trust, Authenta does allow them to know they are getting something with the integrity of the manufacturer. With Authenta, users can check that safety seal and know it’s exactly what the manufacturer intended it to be.

