With news of ransomware attacks forcing schools, hospitals and large corporations offline for days, organizations are anxiously counting days to their predicament. Anybody who has followed the chronicles of cyberattacks over the last few years know that it’s a matter of when, not if a company’s data is locked up in a ransomware prison. Making things worse is the uncertainty of whether its a ransomware incident on company systems, client systems, or those of the vendors that is going to bring a business down.
Traditionally, enterprises have used anti-virus and malware detection to protect against attacks, but the speed and methods of ransomware have evolved over the years. Legacy methods don’t recognize zero-day techniques, and are often slow to detect well-crafted cyber weapons.
All we know about these ransomware tactics, techniques, and procedures (TTPs) is that all parts of their systems have become faster, especially encryption. The fastest TTPs encrypt only a portion of the file, and use techniques other than standard AES stream ciphers, to ensure they can make the largest number of files unavailable the fastest. In recent tests, over 200,000 files could be encrypted in four and a half minutes.
Insider Threats, Both Malicious and Stupid
Some internal data breaches happen without malicious actors. Once, a co-worker who could not work with data in its system of record, started downloading and exporting it into spreadsheets where he created all kinds of amazing formulates, pivot tables, and linked tabs. These spreadsheets, stored on his local desktop, were not part of any regular backup system. If he wanted to work outside the office, he would copy these spreadsheets to a USB drive to take them home. He occasionally lost thumb drives and told no one. The only way the company found out he was doing this was because he kept asking for replacement USB drives.
At another client, a contractor stole hardware from the company due to sloppy asset management processes. To make matters worse, he was told that he could make much more money selling customer data from a national membership-based retailer to which most people had given sensitive data. Unfortunately, when he was caught, it wasn’t for the data, but by the local police, who raided his home for other thefts. No one at the company knew data had been copied.
RackTop Systems BrickStor SP
I recently attended a briefing session with RackTop Systems on their BrickStor Security Platform (SP) for unstructured data. In the session, they demoed running a live ransomware attack against a test system (YouTube link to a similar demo). They were able to shut down the malware, block access to the logged-in user who was the entry point for it, and restore the previous versions of the files, all within minutes. The only reason it took minutes, not seconds is that they wanted to show us the impact of the ransomware and the actions BrickStor SP took as it was doing its job.
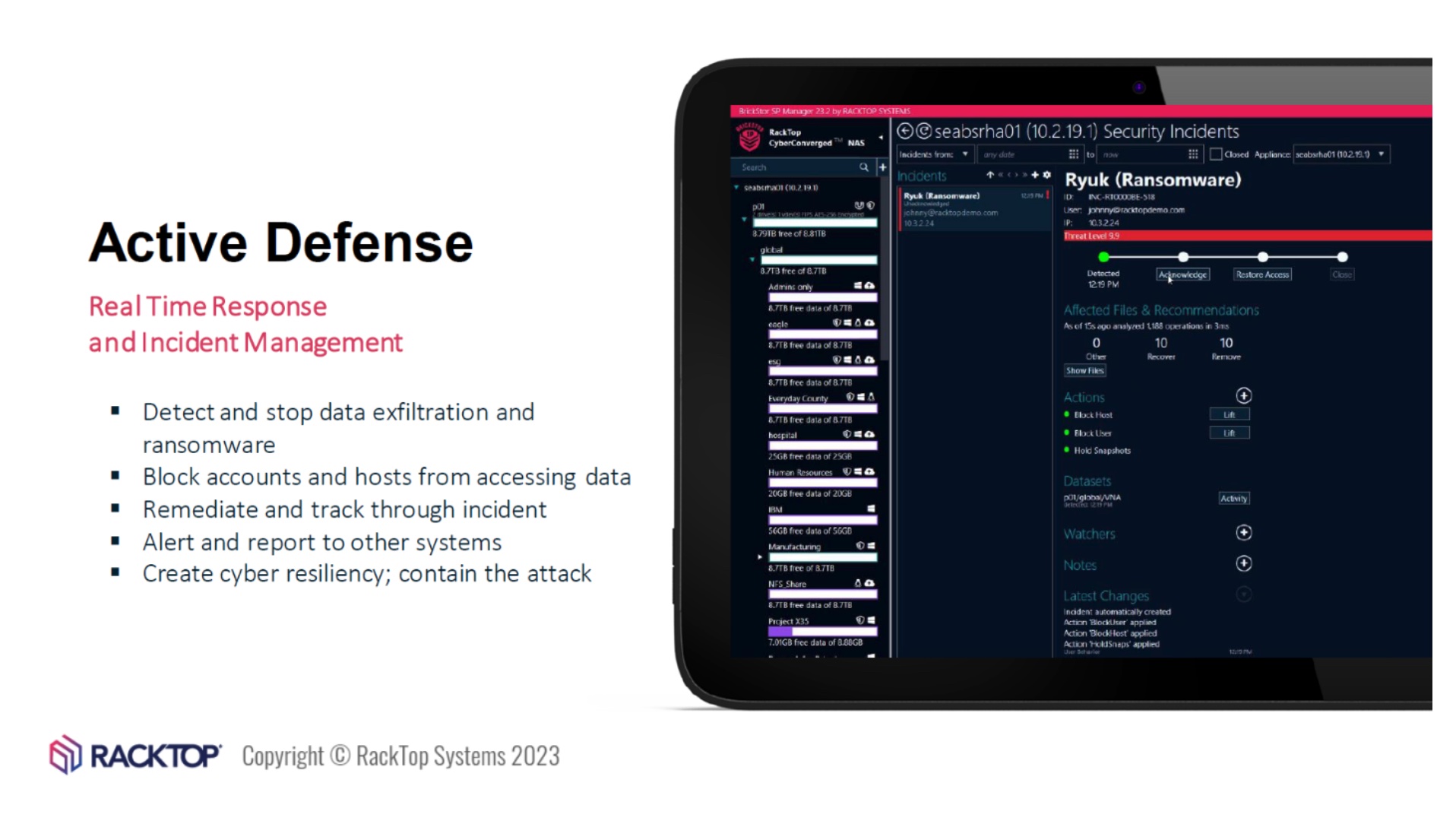
How did it do this? BrickStor SP evaluates user behavior, account permissions, file activity, and other metadata about the files and the user in real time. They call this approach the “Data-Centric Zero Trust Policy.”
The differentiator is the analysis of user behavior. Not just data about access permissions, BrickStor analyzes whether entities are accessing files they don’t normally access, the sort of actions they are taking, and if it’s normal.
It detects user behavior anomalies via User and Entity Behavior Analysis (UEBA). Once detected, the system can take over, stopping all access by that user that was the weak point. A security operator can review and approve the next steps because the attack has been eradicated via that vector.
Why Is Active Defense Important?
Traditional detection takes longer, and stopping access isn’t always automatic. Throw in the fact that “just restore” approaches can take days; the encryption needs to be stopped before petabytes of data are restored. There also has to be protection against the initial data exfiltration that comes with double extorsion approaches now being rolled into ransomware incidents.
Preventing Data Exfiltration
Circling back on the real-life stories from before, BrickStor SP can stop careless employees from downloading files or files at the volume they shouldn’t be downloading. Cherry on top, it monitors user behavior, stopping an insider from downloading files and putting them somewhere they should not be, including a USB drive, just because they like working on unsecured devices. It can also stop malicious insiders from exfiltrating large volumes of data. The key is that it isn’t doing this based on some set of general policies but on actions by a particular user and a specific file set.
Summing Up
This article touches only a few of the features that BrickStor SP offers in interest of time and space, but here’s what I think. The greatest merits of BrickStor SP are active, data-focused detection based on advanced analytical approaches to user behavior, speedy detection and lock-out that saves time and money for the resumption of normal operations, and integration with AD and LDAP. The product covers both insider and external threats, malicious and ill-thought-out actions, and most importantly combine storage and threat detection.
The only downside is that BrickStor SP protects unstructured data for SMB and NFS file shares only, These are drawbacks only to someone searching for solutions beyond storage. They only offer support for data classification from third-party solutions, but that is a common way to address data categorization and classification and most organizations already have solutions in this area.
If you’re shopping for a cyber storage system for unstructured data, take advantage of the virtual BrickStor SP free trial on their website.
Watch the RackTop BrickStor Showcase and more on the Tech Field Day website for more information.

