Industries that require high availability and integrity of data struggle to handle the demand without migrating, at least partially, to the cloud. This could be anything from backup and archival data to data handled daily by the users. Whilst the cloud addresses this concern for high availability, it isn’t the easiest to get security right.
Take healthcare for example – healthcare workers require continuous access to mass amounts of highly sensitive data with the confidence that it is accurate. This data is also, understandably, subject to high regulatory requirements. Is it possible to ensure that security and privacy needs are met with that level of sensitive data? RackTop shared their confidence to meet that demand, whilst also tackling the ever-changing security landscape with their solution BrickStor SP.
Consider a security incident in three phases: pre-incident, during the active incident, and post incident. Whilst each phase is crucial, the first phase – planning and understanding of your environment – is key. For any environment, we must plan for security incidents, because they will happen, but your work before can reduce the level of impact.
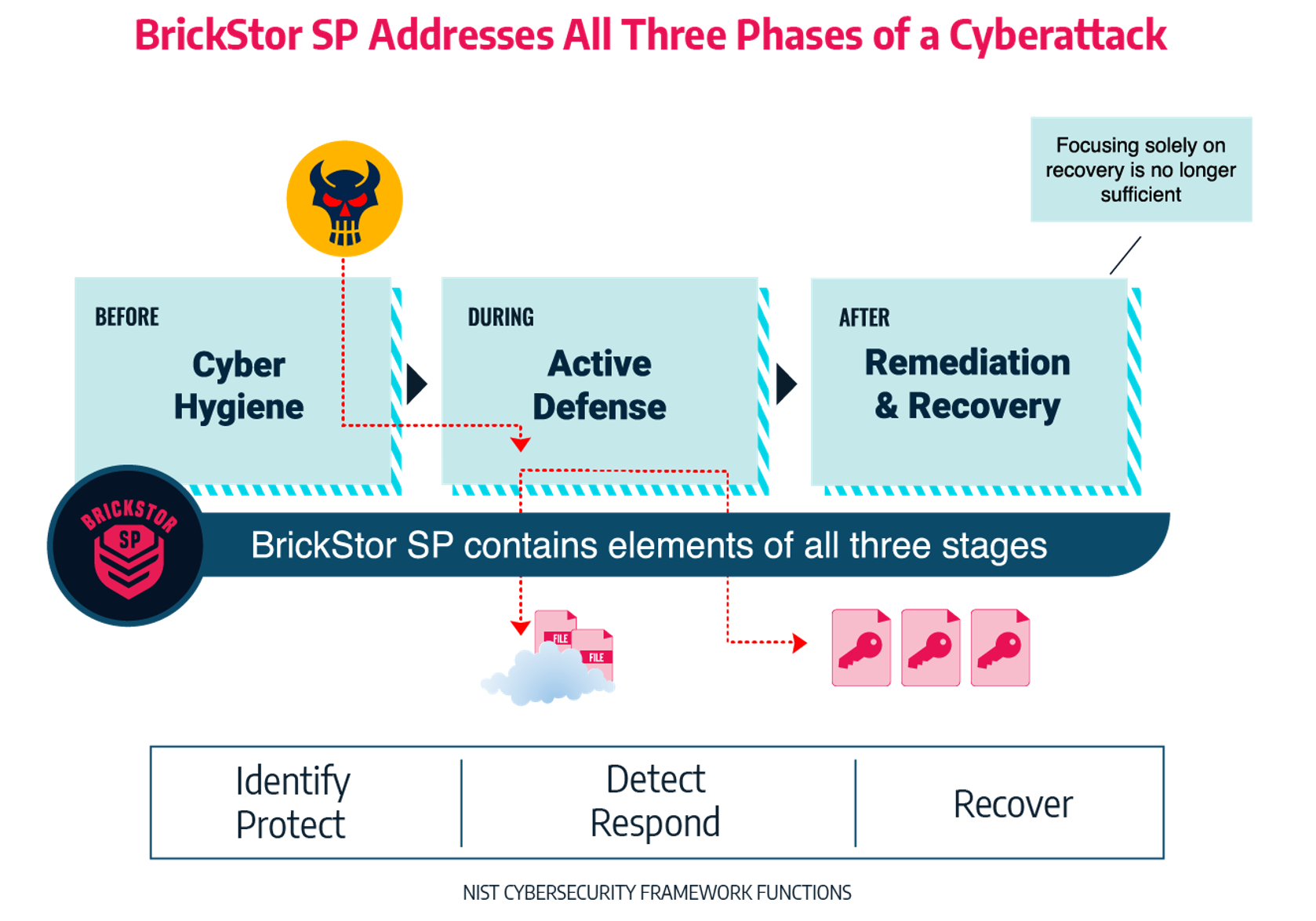
Firstly, let’s consider ransomware. Ransomware is an ever-growing and changing threat. BrickStor SP provides organisations assurance of security of their data, by making sure that data is stored with industry recognised encryption standards. Offsite data storage separates the data from the encryption keys, meaning even if a malicious actor gained access to this data, they could do nothing with it. Additionally, analysis in the GUI itself, alerts the system administrator when compliance settings vary from the expected.
Whilst auditing doesn’t sound as sexy, non-repudiation, that is the ability to prove what user had access to and what actions they took against the data in question, empowers the organisation to respond when something does happen.
Within BrickStor SP, User and Entity Behaviour Analysis (UEBA) and Security Orchestration Automation and Response (SOAR) are in place to identify what ‘normal’ looks like to your data. This baseline creates a way to support quick detection and response.
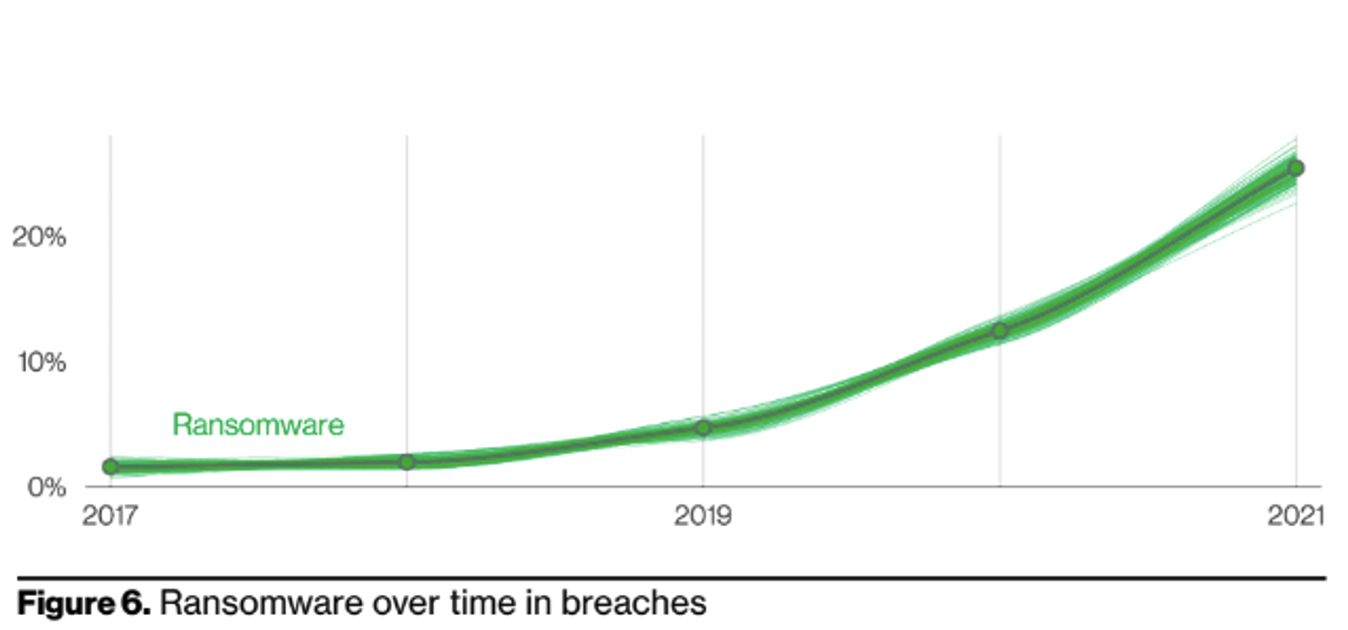
In our theoretical ransomware attack, the malicious actor was financially motivated, and gained unauthorised access via a phishing link to a user. As soon as they gained access to the network, they deployed ransomware.
BrickStor SP is evaluating each file transaction to assess if it aligns with the expected behaviors. If it appears that the transaction is attempting to encrypt the data, the tooling itself can block the file transaction, user and client IP. Meaning the organisation can respond and stop a ransomware attack almost instantly and recover any affected files in a just a few minutes
In a demo that RackTop showed Tech Field Day delegates at Security Field Day 7, the solution was able to block access to the data for the user who was attempting a ransomware attack, as soon as ransomware was detected. The other usersmaintained access through this attack, reducing business impact. In the demo, only 1 file was able to be encrypted before BrickStor SP stopped it. As noted in the video, RackTop stated that the longest an attack was able to progress was under 1 minute before being blocked. They also covered how BrickStor SP allows for an easy recovery from the immutable backup.
As BrickStor SP is built for auditing, our theoretical organisation was able to use the incident manager screen to review what machine and user account carried out the ransomware attack against the data. Through that, our theoretical responders found a Phishing email in that user’s mailbox which was the initial compromise, then realised that others had received the same email. Theoretical operations team were able to remove that threat from causing further incidents.
The Verizon Data Breach Investigations Report (VDBIR) 2022 notes “Error continues to be a dominant trend and is responsible for 13% of breaches. This finding is heavily influenced by misconfigured cloud storage.”
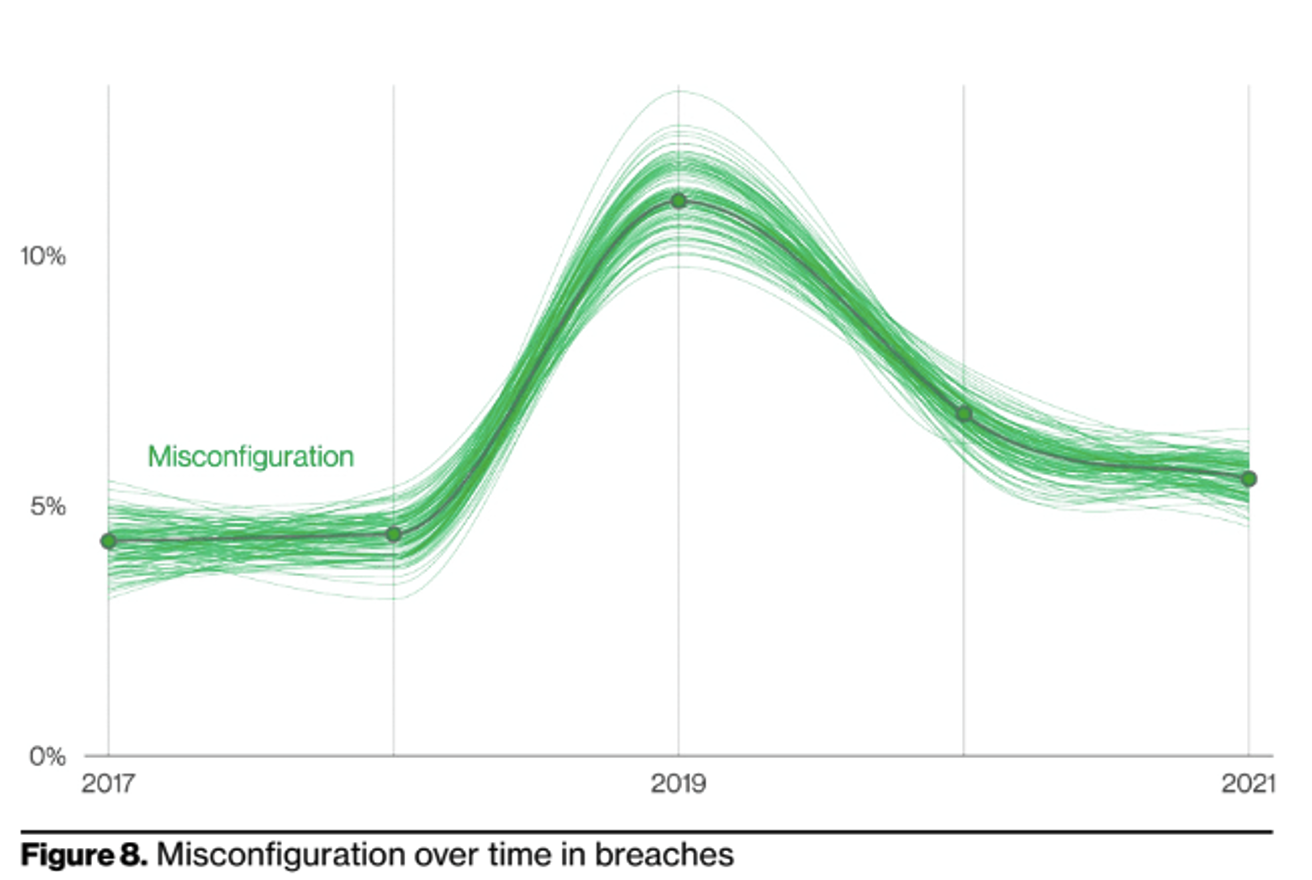
In the second use case we considered, the incident is caused by human error. One aspect that is extremely attractive to me from RackTop’s approach is the secure-by-default feature. This is ‘out of box’. The solution is configured to ensure security controls are turned on. We hear every day the ‘skills gap’ within information security, and whilst I have a slightly varied view on this, I do agree there simply aren’t enough security persons or time in the day to cover everything. As mentioned above, within the management portal, it will alert when typical compliance configurations are misaligned. The goal is to validate that it wasn’t changed accidently, as well as educate the administrator on potential impact.
With the UEBA, identification of ‘normal’ found that a subset of data was no longer accessed on a daily basis, allowing the administrator to migrate this to an archive, thus reducing the amount of data at risk. However, a misconfiguration of privileges was still present. Now that the data is only needed by a few users access controls could be changed to reduce risk. Through UEBA the theoretical operations team noticed unusual data access activity off hours and was able to detect a compromised user account, reset the password, and continue their investigation.
The term cyber hygiene has always sounded a bit funny to me. However, the concept is legitimate. I view it as the way you wash your hands before eating, you’re preparing your environment before an event takes place. This way, you know the baseline of clean, and can quickly detect when anything is outside of this. Housing data in the cloud can be a daunting task, but BrickStor SP at least has built their solution around security by design and by default, along with focusing on user experience. Combine that with an appropriate level of knowledge, support, and response capabilities, and you’ve set your organisation up for handling the next event with confidence.

