Quantum tech is slowly inching closer to becoming a reality. A global race has begun to harness the powers of quantum mechanics to build super-networks. The Quantum Internet, when it arrives, will make the World Wide Web look antiquated.
Quantum networks can transmit quantum data between distant machines through channels unassailable by hackers. But don’t hold your breath, because researchers are only testing the building blocks and working on prototypes.
Leading companies like AWS, Microsoft, Google, Cisco and IBM have skin in the game. During Cisco Live US 2024, Cisco unveiled some of its own in-house quantum technologies that are incubating in its newly opened Quantum Lab in Santa Monica.
Led by Cisco Outshift, a visionary team that is behind many of Cisco’s breakthrough innovations, Cisco’s quantum roadmap encompasses many a milestone. The near-term goal is to build a quantum switch based on quantum teleportation.
Quantum Networking 101
Let’s get some basic facts out of the way first. What is quantum internet? Simply put, it is a large, interconnected system of geographically dispersed quantum computers communicating via quantum links.
Is quantum network going to replace the classical network? The short answer is no. Quantum networks are not meant to replace conventional networks, and it will be many many years before the technology reaches that scale or maturity. However, its basic construct is analogous to that of today’s network.
This begs the question – why then build quantum networks? Several use cases have emerged in the quantum realm that require quantum networks to take off. Some examples being cryptography, distributed quantum computing, distributed sensing and quantum money.
Distributed quantum computing is going to be the most dominant use case in the near future, according to Tim Szigeti, distinguished technical marketing engineer for Outshift.
Quantum computers interconnected over vast geographic distances can realize huge benefits that today’s computers cannot come close to – unlimited processing power, fault-tolerant computation, and massive parallelism, and so on.
Distributed sensing is another use case. It has applications in the fields of astronomy and cosmology. Studies show that signals picked up by distributed sensors when merged over quantum networks provides shockingly high-precision results. The accuracy level significantly surpasses calculations done over classical networks.
“With a radio telescope array looking into deep space, the classical precision could be significantly improved by a factor of ± 1/N, “N” being the number of telescopes. So without touching the hardware itself, I can see deeper into space or farther back in time just by using a quantum network,” Szigeti explains.
Quantum-Proofing the PKI
But the most pressing and urgent use case, Szigeti says, is quantum key distribution (QKD). QKD and post-quantum cryptography are two of the proposed solutions to the Y2Q (Year to Quantum) problem. The Year to Quantum is still an unknown year, but as it approaches quietly, the current encryption schemes are at risk.
In a future where large-scale quantum computers enter the scene, the public-key cryptosystems currently in use face an existential threat. Quantum computers, infinitely smarter and faster at solving problems than conventional systems, can become the key to illegally decrypting cryptosystems.
“Your encryption is only as strong as your key exchange,” he cautions.
With approaches like “harvest now, decrypt later” where data is acquired and saved for later to read awaiting a possible decryption breakthrough, the public key infrastructure (PKI) can be broken in the blink of an eye with the quantum computer.
“Quantum computers are really fast, and they present a real and imminent threat to asymmetric key exchanges, particularly any type of public key infrastructure (PKI), all the Diffie-Hellmans, and elliptic curve cryptographies.”
The key to making PKI quantum-safe lies in the pages of quantum physics. Quantum physics is the study of behavior and characteristics of subatomic particles. Interestingly, this branch of physics defies all laws of classical physics.
“All the physics that we know apply to things that are larger than an atom. Once you get smaller to that scale, all rules just go out the window,” Szigeti states.
The reason for this is sub-atomic particles are unique. They have dualities whereby they exhibit behaviors and characteristics consistent with both particles and waves, a phenomenon not observed in larger objects.
“How can you be a particle and a wave at the same time is very difficult to express,” he says.
The technique of quantum teleportation capitalizes this. Quantum teleportation is nothing short of science fiction. But to be able understand it, you need to grasp a few fundamentals of quantum physics.
In quantum computing, the basic unit of information is quantum bit or qubit. Qubit can be made from electrons, photons or trapped ions.
The way it is different from a binary bit is that while a binary bit can only represent one of the two binary values, 0 and 1, a qubit, represents any proportion of these two values, in addition to the values themselves. In other words, probabilities of 0 and 1 simultaneously. This is called a superposition.
Superposition is key to manipulating qubits and achieving teleportation.
“Take for example a coin,” Szigeti says. “As it’s flipping in the air, at any given instant in time, it has a probability of resolving to heads or to tail. That probability is constantly changing until you finally take a reading and then it collapses that superposition to a single discrete value.”
These states of a qubit are highly delicate and easily disturbed. As long as a qubit is unobserved, it remains in superposition of probabilities. The instant it is read or measured, it collapses into one of the basis states.
Qubits are transmitted between quantum computers using the principle of quantum entanglement. The theory of entanglement states that two quantum particles can be intimately linked such that any change in the state of one is instantaneously reflected in the other, even when separated across billions of lightyears of space.
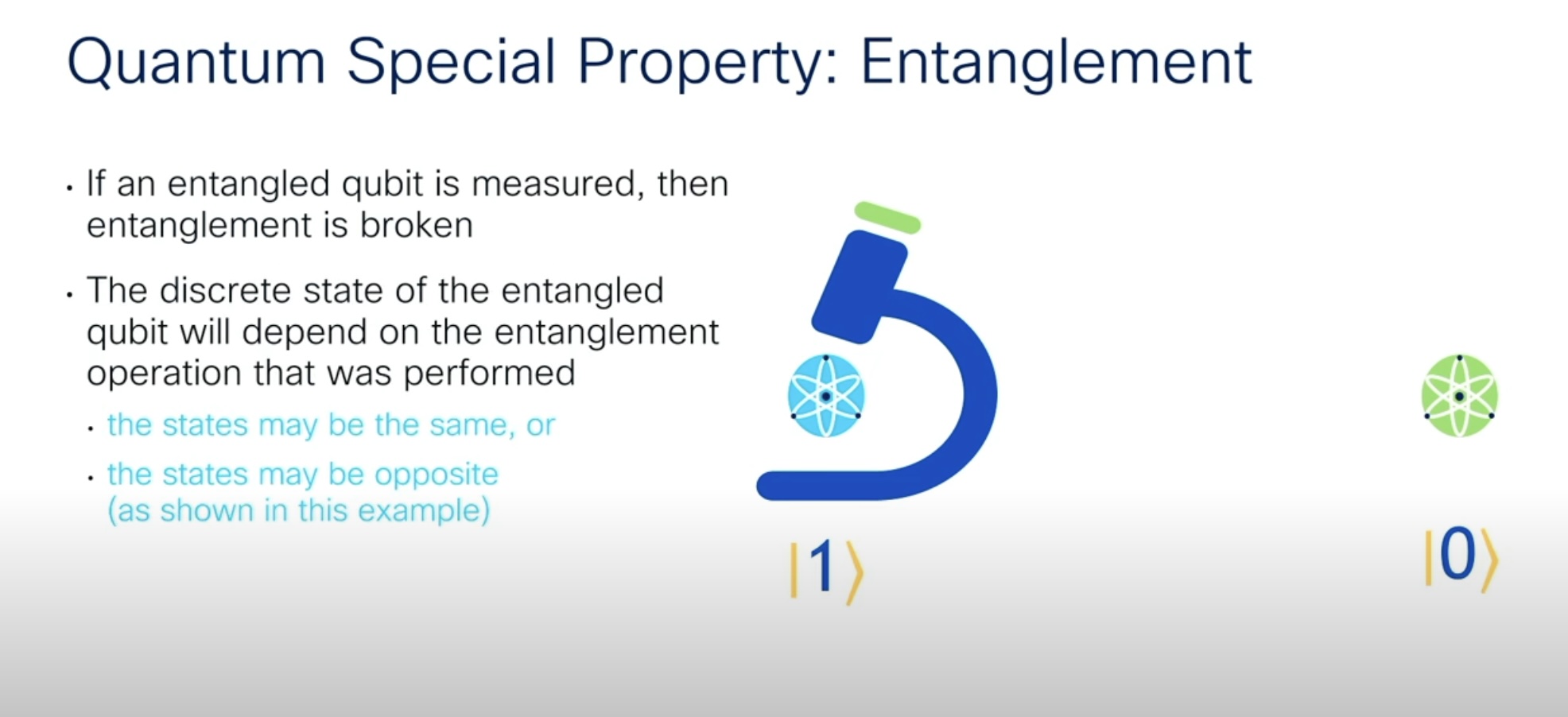
Leveraging this, a qubit can be manipulated to be entangled with another across vast distances with no physical medium in between. Entangled, their states are related, meaning measuring the state of one particle will tell you the state of the other.
Two or more qubits can be entangled in this way. The highest recorded number of entangled qubits in a quantum computer is 54.
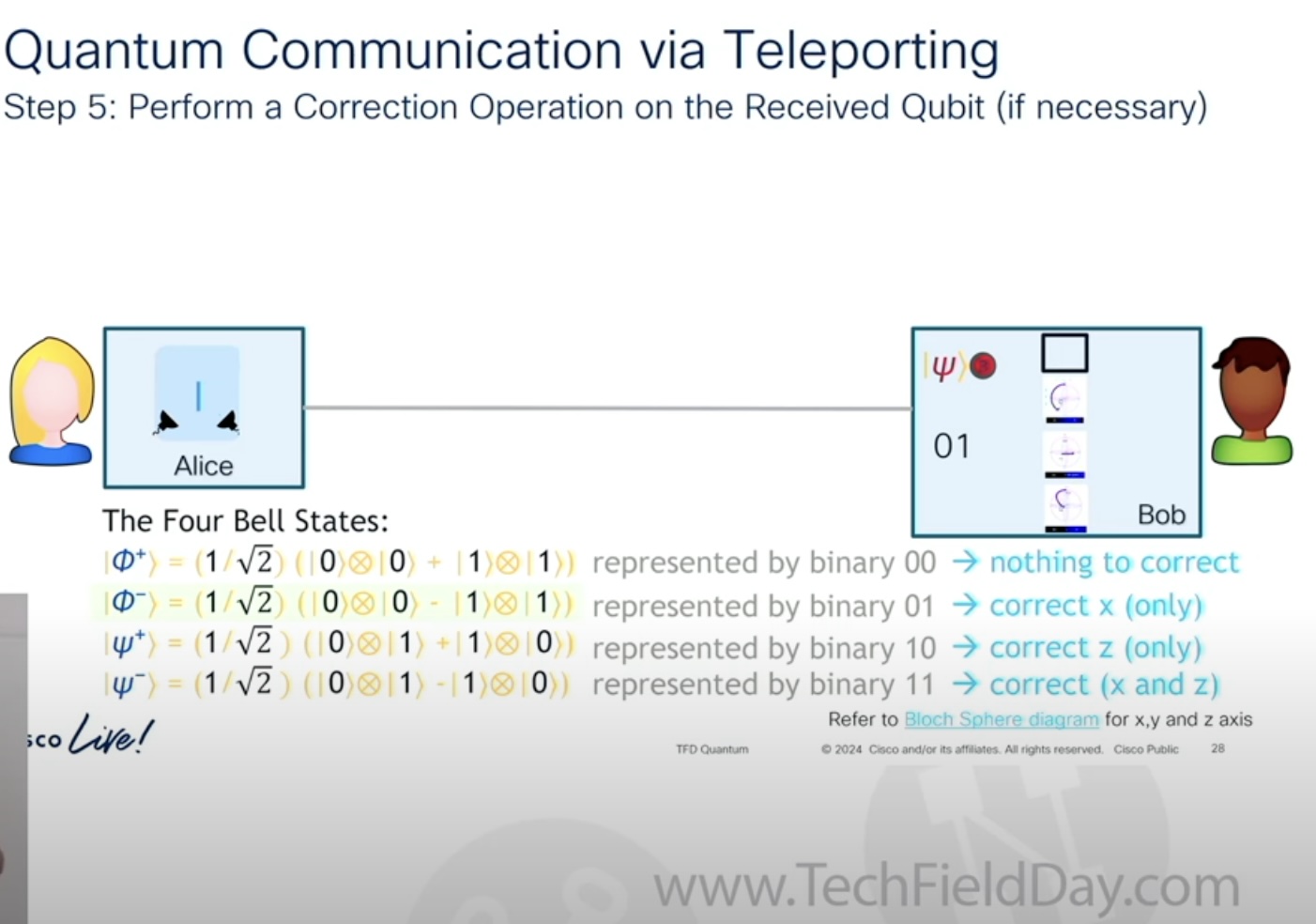
Depending on how two qubits are entangled, they will represent one of the four Bell’s states – equal or opposite basis states.
This has its advantages. “Qubits can represent multiple values at the same time – 0 and 1,” he explains. “So, essentially, you’re actually sending much larger amounts of data with far fewer qubits than you would with regular bits. For instance, if you had one qubit to transfer, you’re transferring to the equivalent of two binary values for computation.”
A third phenomenon that makes faithful transfer of quantum states possible, and is especially beneficial in networking and communication, is no-cloning.
It is scientifically impossible to clone a qubit. “Mathematically, it can be proven that it’s impossible to clone information that’s encoded in a quantum state. The simple descriptive proof is that you can’t copy something without first reading it, and if we take an instantaneous reading, we can’t copy and then eavesdrop and propagate.”
Quantum Key Distribution leverages this property. Information encoded in one qubit cannot be copied or duplicated because of the volatility of the states. If the state of a qubit is intercepted or changed, it will lose its superposition and because of entanglement, the information will be instantly transmitted to the other end.
If you are still with me, here is how these phenomena open doors for quantum teleportation. Imagine that you want to send over a secure message to a receiver at the other end of the line. In the first step, over a quantum network, you will entangle two qubits ensuring that the particles are fully correlated. Now send one over to the receiver while the other stays with you. Taking a reading of the state of the qubit at your end will create a shared key which can be used to encrypt the message you want to send via the usual channel. The receiver can then use the same key to decrypt and read the message.
Along the way, if a bad actor intercepts the qubit and gets the encryption key, the state of qubit will change to “read” instantly at the other end, indicating that the data has been snatched.
The Quantum Roadmap
A comprehensive quantum program fuels all of Cisco’s research works around quantum networking. “Our charter is to say what kind of business problems of tomorrow should we start tackling today so our customers have the solutions as they run into these,” Szigeti says.
“We have quantum research scientists as part of our group at Outshift and they are doing mathematical modelling and publishing groundbreaking research on top of that.”
Insofar, Cisco has two published papers under its belt. One explains the blueprint for designing an extended quantum network spanning millions of nodes, and the other provides a framework for designing a quantum network on top of an existing optical network infrastructure.
“You don’t require rip and replace mandate in order to support quantum in the near future,” says Szigeti. “You can maximize the utility of what’s already available, minimizing the hardware investments.”
To offer a more practical experience, Cisco has developed a Quantum Network Design Kit (QNDK) Simulator. The QNDK Simulator is a software program that reproduces aspects of quantum networking. You can play with the protocols, or try building and interconnecting quantum networks on it. Besides being a good place to practice, the simulator also helps gain a good sense of what to expect from quantum networks before investing in the hardware.
Extending quantum networks over large physical distances require quantum repeaters to prevent data loss. These devices will link quantum computers across sites that have not interacted in the past into a giant quantum network.
“If you lose something along the way, you can do a parity check and then you can restore that loss and keep propagating it without actually taking a reading of the logical value of the qubit. It’s a workaround.”
Cisco is working on a one-way quantum repeater prototype, Szigeti informs.
Another technology shaping out in Cisco’s Quantum lab is a hardware Quantum Random Number Generator (QRNG).
“Current digital algorithms are actually not random. They’re pseudo random that take a specific seed and perform some mathematical operations in order to produce a string of numbers but it’s not truly random.”
Cisco’s Quantum Random Number Generator guarantees true randomness. Harnessing quantum uncertainty, QRNG produces mathematically proven random number sets.
“Not only it is a purely random number generator, it also has verification capabilities using the same Bell’s inequality theorem to prove that every component is maintaining true randomness.”
Do not miss Tim Szigeti’s in-depth presentation on quantum networking from the Tech Field Day Extra at Cisco Live US 2024 at the Tech Field Day website.

