It has come to light in the recent years that an early warning system would be most valuable to enterprises’ efforts to counter ransomware and improve cyber resilience. As security experts dig deeper into ransomware incidents, this seems to be a promising answer.
Early Indicators
The ransomware scourge is far from abetting. Attacks are more stealth, swift, and sophisticated than ever. The average dwell time has grown from 5 days to 9, and a majority of the exploits are seen employing double, even triple extortion techniques – a three-prong attack involving data exfiltration, encryption and ransom demands. The use of AI in ransomware attacks is just more bad news on top of it.
“That’s the nature of the threat, and it forces us to think – is recovery enough?” asked Steve Preston, VP of Security Services at Commvault, at the recent Security Field Day event. “The answer is no. If you’re committed to protecting data, not just recovering or backing up, you have to think about what’s your window of opportunity to reduce the blast radius,” he said.
According to experts, that window is during incubation. An attack chain is peppered with many early warning signs. If detected, these can help stop an attack in its tracks. The key is to catch the first symptoms when a swift remedy is still possible.
What’s Stopping Early Detection
So what’s stopping security teams from staying ahead? While acting timely and purposely is the rule of the game, there are many challenges of that. Consider this: A research released by Splunk shows that the latest ransomware encryption speed recorded is thousands of files per minute. In a lab environment, that number equals 18TB of data a day. Calculated over the standard dwell period, it adds up to hundreds of TB of data. Sometimes, that is the total data volume in an enterprise. Beating that speed is no small thing.
Preston explained that attackers have resorted to encrypting data at random, instead going serially and making a slow progression. The corollary is a maximum blast radius, and shorter time to ransom.
A type of stealth attack that is even harder to detect, and has come into greater focus, is LOLbins attack. It’s an attack technique where the offenders use native tools in the environment to execute an attack. No malicious code is installed; only the internal systems are exploited to carry this out. Attacker hide in the environment, living off the land, and eluding detection for weeks on end.
Standard monitoring and observability tools fail to detect this because of fileless malwares which are not identified as typical bad elements. “This is not bad behavior. They’re not introducing foreign files. They’re not exploiting vulnerabilities. In a lot of the cases, they’re just using your tools and getting nefarious outcomes,” said Preston.
Security teams especially the ones that are small and lightly staffed, are chronically prone to miss the early warning signs of an emerging attack. With already so much on their hands, this is happening across enterprises with alarming regularity.
Shifting data protection left mitigates a lot of the risks and opens up the possibility to neutralize an attack chain early in the process. The bonus is, it accelerates remediation and recovery, shrinking the blast radius to a minimum.
Deception Defense with Commvault Metallic ThreatWise
Several security companies have moved into the early detection and recovery space, but only a handful is able to offer enterprise features that ensure solid and reliable early detection, so far.
When it comes to data protection, Commvault is well-known for its stellar data security and active defense products that help manage risks and reduce cyber incidents. At the event, Preston demoed Metallic ThreatWise, an early warning security service that offers meticulous threat detection capabilities.
ThreatWise is a distinguished product for several reasons, key among them is its technology. ThreatWise is designed to detect ransomware at the earliest stages of the attackchain. For that, Commvault has designed a defense by deception technology, drawing from a battle-tested strategy which ThreatWise leverages to thresh signals from the noise.
Commvault borrowed this technology from the Israel Air Force where it has been used for over a decade to defend the Israeli air space against foreign military invasion. ThreatWise dispatches decoy assets in the environment that mimic regular assets. The job of these imitation assets is to lure attackers away from real resources, and get them to engage with the fake ones unsuspectingly. This slows down the attack, and gives the defending team time to act.
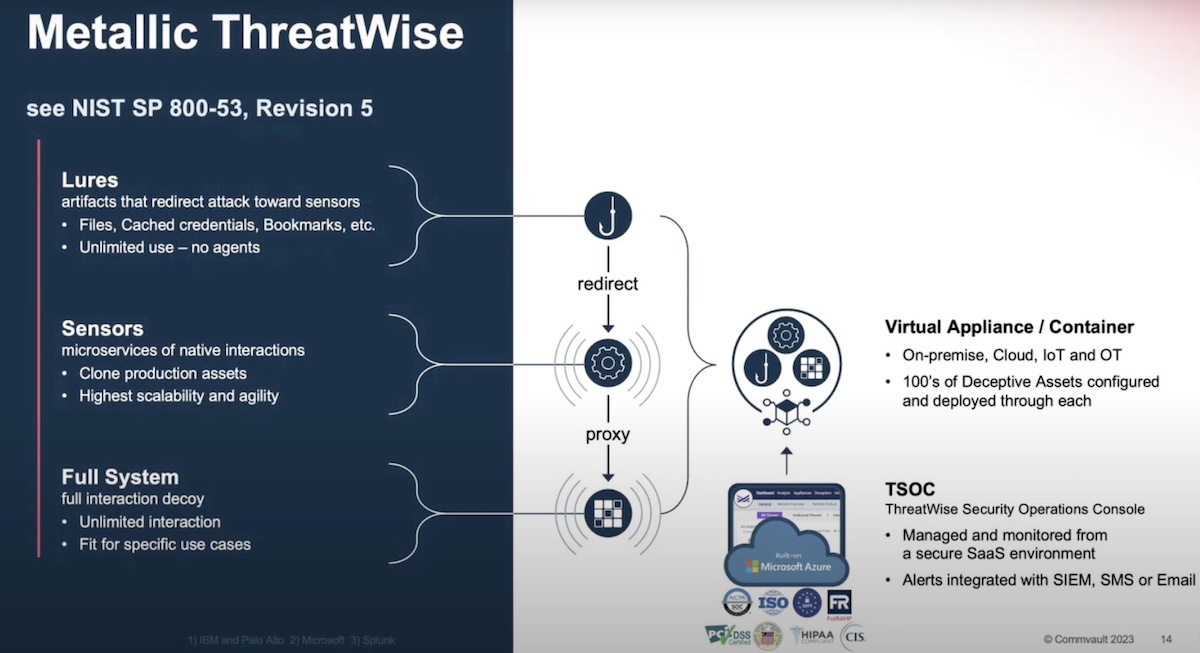
This technique is comparable to a honeypot which also uses manufactured attack targets to divert bad actors from critical assets. But where honeypots are expensive, risky even – because they require injecting vulnerability in the environment – and come with overheads of monitoring, ThreatWise bypasses all of that with a cost-efficient mechanism.
This is how it works: Users can buy ThreatWise threat sensors by the pack, and deploy them in the network. The sensors are lightweight, and invisible to authorized users and internal systems. They crawl the infrastructure, behaving like regular resources and blending in easily.
“The cool thing about it is that you’re not putting anything on endpoints. We can deploy in a hospital room, a lab, manufacturing floor. We have these things in copper mines, in renewable energy grids, in IT, retail, everywhere because they don’t touch anything,” explained Preston.
In the environment, the sensors traverse the path to critical resources, scanning for threats and “emulating a deep enough interaction to identify the attacker,” by essential attributes like their MAC addresses and IPs, and their activities and connections. The sensors can be scaled up in number to ensure a broader surface coverage when required.
With the data gathered from the environment, ThreatWise serves out real-time insights on all active and hidden threats – even the most stealth ones that bypasses standard monitoring tools – through a cloud-hosted management console delivered as a service.
The slim and lightweight architecture of ThreatWise minimizes infrastructure footprint, and reduces total cost of operation.
Wrapping Up
The digital landscape is submerged in threats, and attackers are gaining greater finesse every day. Quick action is integral to arresting and limiting their impact to the environment. But organizations still don’t have enough tools at their disposal to check attacks early, before they get out of hand. Metallic ThreatWise changes that. By surfacing threats accurately and early in the chain that other tools tend to overlook and underestimate, it gives enterprises the visibility to separate bad actors from legitimate users. The solution provides a forceful combination of insights and observability which quantifies to effective timely detection and broader protection. That is incentive enough to get ThreatWise before it’s too late.
For more, check out Commvault’s demo of Metallic ThreatWise from the recent Security Field Day event at the Tech Field Day website.

