The latest stories of cyberattack on small startups to big airline carriers is a wakeup call for enterprises, who have so far shielded themselves from the truth about the ravages of cyber incidents.
News cover in great detail the far-reaching impacts of these exploits, painstakingly narrating the disruption, the revenue loss, and the stock dip, to underscore the urgency of effective cyber protection. Something, the media misses reporting though, is the measures that could have prevented the attacks in the first place.
A Trying Routine
Typically, in a cyberattack, hackers make entry by exploiting a common or hidden vulnerability. The job of the security team is to patch these vulnerabilities in the network and keep the infiltrators out.
A trivial task it may seem, except it’s not. A network can have anywhere between a few to hundreds of thousands of vulnerabilities. The bigger the network, the bigger the risks. There is a reason why security experts call it an attack surface, and the present-day attack surface is as broad as it is complex.
A standard way to approach this is to perform continuous vulnerability assessments where SecOps scans the network using a set of tools to identify the anomalies. In a separate step, they would remedy the defects, and reseal the perimeter.
A Worsening Problem
When it comes to physical sites, it is maddeningly hard to detect bad elements and vulnerabilities. Physical sites have observably multiplied in the recent years, stretching the boundaries of the network far and out. Wi-Fi network breaches have become more common than was previously believed possible, making regular site assessment an absolute priority.
This is worsened by the dispersed physical addresses of the sites. “You really have to think about sites as being more distributed. Ethernet has worked its way into everything – factories, in particular – and most businesses manage over fifty sites,” says James Kahkoska, CTO at NetAlly, a company that manufactures network testing and analysis tools, at the recent Security Field Day event.
NetAlly – Looking Back
A company rapidly making footprints in the networking niche, NetAlly, is set to reverse this. The name NetAlly may not ring a bell instantly to most readers because they don’t pop up on the top 10 or hottest-in-tech lists. But their legacy of innovation is as old as some the hottest players in the industry.
NetAlly operates on a small scale, and caters to a growing set of customers who run tens of physical sites and require easy-to-use tools that serve the dual purpose of network probing and vulnerability scanning.
Born in 1995, as Fluke Networks, NetAlly has been serving the networking space for nearly three decades now. During this time, the company has changed hands a few times, shrank to the size of a business unit to a bigger company, and reborn and branded as NetAlly in 2018.
A year later, NetAlly relaunched at Mobility Field Day, as it set out to gain momentum as a brand-new entity in the networking space. Now completing 5 years as an independent company, NetAlly is ready to diversify. Through the onset and adoption of new technologies like cloud and Wi-Fi 6E, NetAlly has mindfully curated its portfolio, rolling out new appliances to cater to the transitioning enterprise world. This has brought the company to a point where it is now straddling the lines of networking and security with a portfolio of purpose-built tools like CyberScope.
“We’re really starting to find our way of using the tools as analysis platforms, and working hard on unencumbered collaboration and being able to share information and achieve visibility,” said Kahkoska while showcasing CyberScope at the Security Field Day event.
But making inroads into cybersecurity isn’t an effortless enterprise. Security is a competitive domain, and as a new and buzzing enterprise, it is outgunned and outshined by the bigger and older players dominating the industry. But Kahkoska argues that NetAlly has one strong advantage – it is unique and does not fit cleanly into any of the market segments.
On one hand, this departure from convention has earned it little to no recognition from the likes of Gartner, on the other hand, it has given NetAlly an avenue to introduce a first of a kind cybersecurity tool to the customers.
The security industry, Kahkoska noted, is at the crossroads of old and new. Legacy systems are still pushing on, while a flurry of newfangled technologies has swept up the customers a giddying number of options. The corollary is a complexity problem that is stressing teams in unexpected ways.
There is growing evidence that technology sprawl is increasingly hurting visibility and causing unrelenting complexity. As more devices are onboarded to the network, it lends to the heterogeneity, making it a bewildering task for teams to be on top of things. An ongoing skill shortage further escalates this situation. It is time to bid farewell to old ways and embrace new ones.
A One-of-a-Kind Technology
CyberScope, is a tool that fits this picture perfectly, and is the reason NetAlly is pivoting to the security space, shifting from its own domain. “We started looking at all the features we had through an ITOps lens, and it’s amazing how much of our applications made sense for SecOps,” Kahkoska declared.
CyberScope is the “world’s first handheld cybersecurity tool”. Originally sold as a networking tool, CyberScope has a history of serving cybersecurity use cases for its users. Large vendors have used it to analyze the Wi-Fi range outside their offices for counter-surveillance purposes. Clients have also used other NetAlly tools to do sweeps and scans to discover and probe devices.
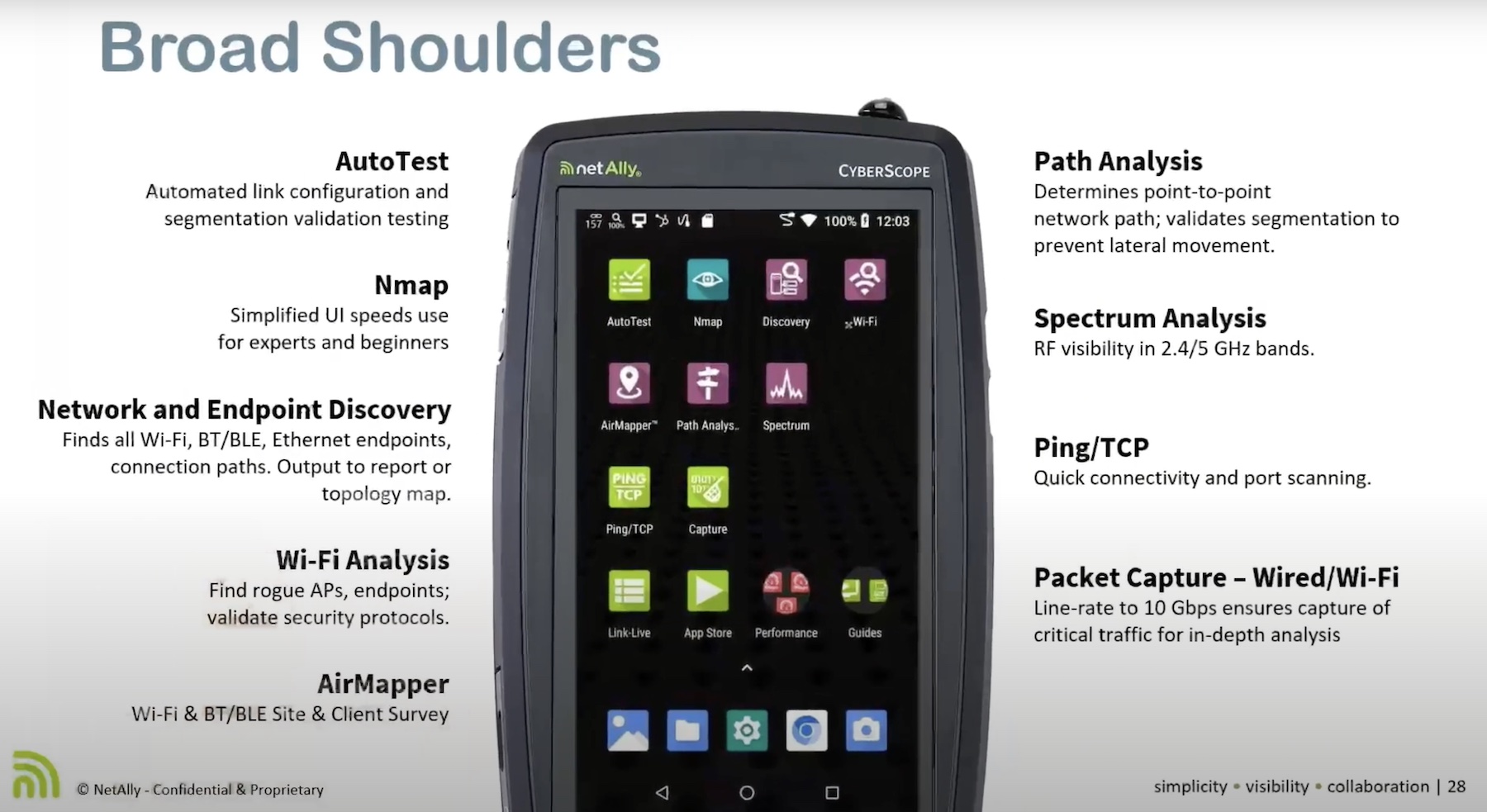
Now rechristened as a cybersecurity tool, CyberScope provides comprehensive risk assessment, analytics and reports of the site access layer. Here’s how it works: It actively probes and scans the network to discover endpoints and other components automatically, capturing the interplay between them. CyberScope can detect APs and clients across 96 channels, helping analyze the scope and quality of RF reach inside and outside the premise.
Once detected, CyberScope categorizes all devices into authorized, unauthorized, neighbor and unknown. CyberScope can probe into and verify network segmentations for both wired and wireless networks. Other features include path analysis, topology mapping and technology identification.
An outstanding aspect is the Nmap technology that is embedded in CyberScope. Nmap is a vulnerability scanner that automatically scopes the network for weak links and exposures. Using pre-built and custom commands, it performs deep analysis of every device and connection in the network, identifying all potential threats and probable issues.
Reporting is a big part of what CyberScope does. The tool ingests information from the network in real-time, and translates it into analytics that show up as reports, also in real-time. Users can get assessment reports, topology mapping and error notifications instantly. Its built-in remote control feature allows full mobility, making it the perfect tool to collaborate for engineering teams.
Wrapping Up
Every minute a new device or user connects to the network adding to the long list of components drawing from its resources. Enterprises running tens of sites tend to fail to keep in touch with every device and equipment, allowing rogue devices and vulnerabilities to exist in the network. CyperScope elevates awareness of those vulnerabilities, warning users against threats, and helping security teams manage and minimize risks at least impact. Handy and ruggedized for outdoor use, and with a battery life that lasts all day, CyberScope is an instrument designed for smarthands who are out in the field, doing site to site inspection, enabling them to do security scans in one quick sweep.
To learn more, check out NetAlly’s presentations from the recent Security Field Day event.

