One of the most talked-about things in any discourse in technology these days is cybersecurity. Progressive talks of cyber defense, and buzzy phrases like “shift left” and “AI-powered security” have peppered conferences and forums of late, as cases of security exploits heighten.
Although now widely underwritten, it took some convincing to get everybody to shift their outlook and be onboard with the urgency of the matter. At the brink of this new awakening, the industry is preoccupied with a new enemy – ransomware.
“If you look at ransomware attacks today, they tend to be pretty complex. They often involve more than one workload, and more than one cloud, and may involve multiple tactics and attack techniques,” said Stijn Vanveerdeghem, Director of Technical Product Management, VMware, while detailing a newly launched solution to the delegates in attendance at the recent Tech Field Day Extra at VMware Explore US 2023.
A Precarious Picture
Vanveerdeghem illustrated the complexity of the modern attack chain with an example. Typically, in these attacks, the attackers enter the network through an embedded backdoor, or by bypassing a deadbolt. Lately, they are seen to stray more and more from the initial attack target, and venture out into the resource-rich environment. This is known as the infamous lateral movement.
As they go pivoting from one workload to the next, they escalate privileges and manipulate resource settings arbitrarily, in the process laying ground for the stay. The surf continues until an object of interest is found. At that point, they establish a command-and-control connection with it, seizing charge of the object.
According to the latest intelligence, 62% of organizations surveyed suffer zero-day attacks resulting from software vulnerabilities, and in those attacks, 44% of the times, lateral movements take place.
This attack behavior is revelatory of the vulnerabilities that exist in enterprise environments. Contrary to what was believed earlier, vulnerability is not an unlocked door or an open seam in the perimeter, as it were. It is, in fact, a myriad of internal and external factors playing part in making a breach possible. Software vulnerabilities, open S3 buckets, back-dated OS versions, unprotected secrets, to name a few.
“The problem with exploits, from an attacker’s perspective, is that they tend to be noisy. There’s a high chance of getting detected,” noted Vanveerdeghem.
To avert that, modern cyber cartels have resorted to launching quiet attacks that exploit common protocols and allowed channels. The result is less drama and more impact.
Seeing Is Believing
Visibility is security teams’ ultimate weapon when it comes to screening out bad actors. “Visibility across all of the environments, across all of the clouds is really crucial for them to be able to quickly determine what is going on, how to scope it and what should be the priority of what’s happening in the environment,” Vanveerdeghem emphasized.
But ironically, what empowers them is in scarcity in the distributed and complex topology that is the cloud network.
The rise of lateral movements underscores the importance of east to west visibility, and network segmentation within internal networks, he said. Armed with just these two, security operations center (SOC) can easily sweep the attack surface, rout adversaries, and minimize the blast radius.
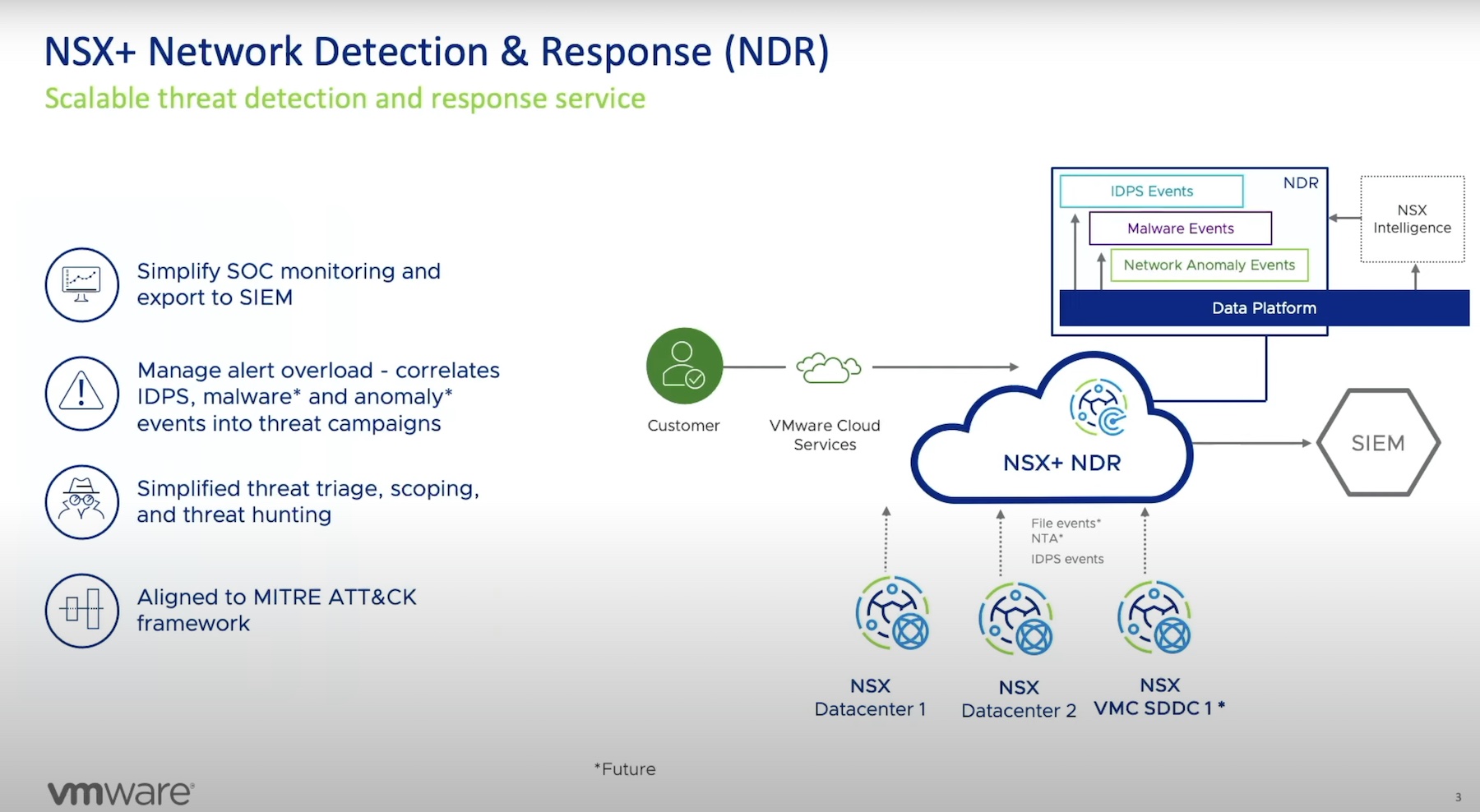
NSX+ NDR
At the event, VMware launched a new network detection and response (NDR) service within its NSX+ suite. Its key capability is to assist security operations in rapidly discovering and eliminating threats.
As the threat landscape matured and settled into more inimical strains of threats and attack techniques, many security incumbents have stepped forward pioneering product development of the latest and greatest kind. VMware, an old member of the tech hall of fame, has introduced its line of proprietary security solutions to this end, of which NSX+, a networking and security platform, is a flagship one.
Total visibility is paramount to defending the network against rogue invaders. To make that possible, VMware designed NSX+ NDR to ingest signals from intrusion detection and prevention systems (IDPS) and network traffic analysis (NTA), and establish a baseline behavior for each workload. Supervised and unsupervised ML is applied to this data to identify the anomalies and deviations. From the irregularities, it then separates out the signals that are relevant to security.
NSX+ NDR also scans files, classifying them into benign, suspicious and malicious, based on the behavior. The algorithms correlate the final events tracing out patterns for SOC to analyze.
In solving the low visibility problem, VMware has rewritten the playbook. NSX+ NDR boasts a distinguished architecture. It is not deployed inside guest virtual machines, but on the network itself. It front-ends with every workload in the environment giving operators the ultimate, high-fidelity visibility of the topology. This architecture not only provides visibility at the perimeter where known vulnerabilities exist, but also into the nooks and crannies of the network that are easy to miss.
While this is only a glimpse of what it can do, Vanveerdeghem offered a deep dive into the features.
Simplifying monitoring for SOC is basal to what NSX+ does. It offers a unified index of events across sites. This includes a full record of all events of interest and context-based findings. The dashboard visualizes the information by laying it out as graphs and maps aligned with the MITRE ATT&CK principles. An intuitive search function, backed by a set of filters, allows users to find events based on time and metadata.
Another feature Vanveerdeghem called to attention is campaign correlation. Using a standard correlation logic, NSX+ NDR can find events that are related, and group them together into campaigns. Post-analysis, it can tell if a string of events is related to or have contributed to an actual attack in the past.
NSX+ NDR integrates with SIEM solutions allowing administrators to export correlated campaigns and detected events outside of NDR.
One of SOC’s worst Achilles heel is excess alerts propagated by monitoring software. Buried under false negatives and unimportant notifications, security professionals often find themselves at a loss trying to isolate the alerts that truly matter from the ones that don’t.
Communication gaps between teams and a prevailing lack of context in security policies, further increase vulnerabilities within the system in the form of operational inefficiency and unaddressed threat vectors.
Thanks to the correlation capability, NSX+ NDR can visibly reduce the alert overload. From the thousands of events it absorbs from IDPS and NAT solutions in the network, it prioritizes notifications based on relevance and category, and shares the results with the SIEM solutions. SOCs can export both atomic and campaign events to the SIEM solutions for threat investigation and troubleshooting. This not only makes scoping and hunting threats surprisingly simple, but also improves accuracy and ultimately, reduces the volume of alerts.
NSX+ NDR is available for trial. “At the initial release, what is available today is the correlation of IDPS events from our distributed and our gateway IDPS. In a future release, we will be adding anomaly events from NTA and malware events into that campaign correlation framework as well,” said Vanveerdeghem.
For more information, be sure to check out VMware’s complete presentation and demo of NSX+ NDR from the recent Tech Field Day Extra at VMware Explore US 2023 at Techfieldday.com.