There is a prevailing narrative in IT that complexity kills productivity. Complexity is the enemy of efficiency, and yet, it is the inevitable trade-off of upgrading to a new technology.
In networking, where there is a bewildering amount of variety just in terms of network architecture and design, operators are drowning in complex operational workloads.
Joining two types of network fabrics, for example – ACI and VXLAN EVPN – requires addressing many independent and interdependent facets in isolation. These include provisioning, security, management and so on.
It is a deeply technical and time-intensive job, one that is made trickier by the underlying architectural differences of the topologies. The skill is painfully hard-won, and takes significant training and practice hours.
A Solution that Helps Substantively
Cisco has come up with a solution that makes the highly technical work of managing and joining different flavors of data center network fabrics surprisingly low-tech.
The Cisco Nexus One Fabric Experience solution hides away complex technicalities of fabric technologies, making them operationally uniform and consistent.
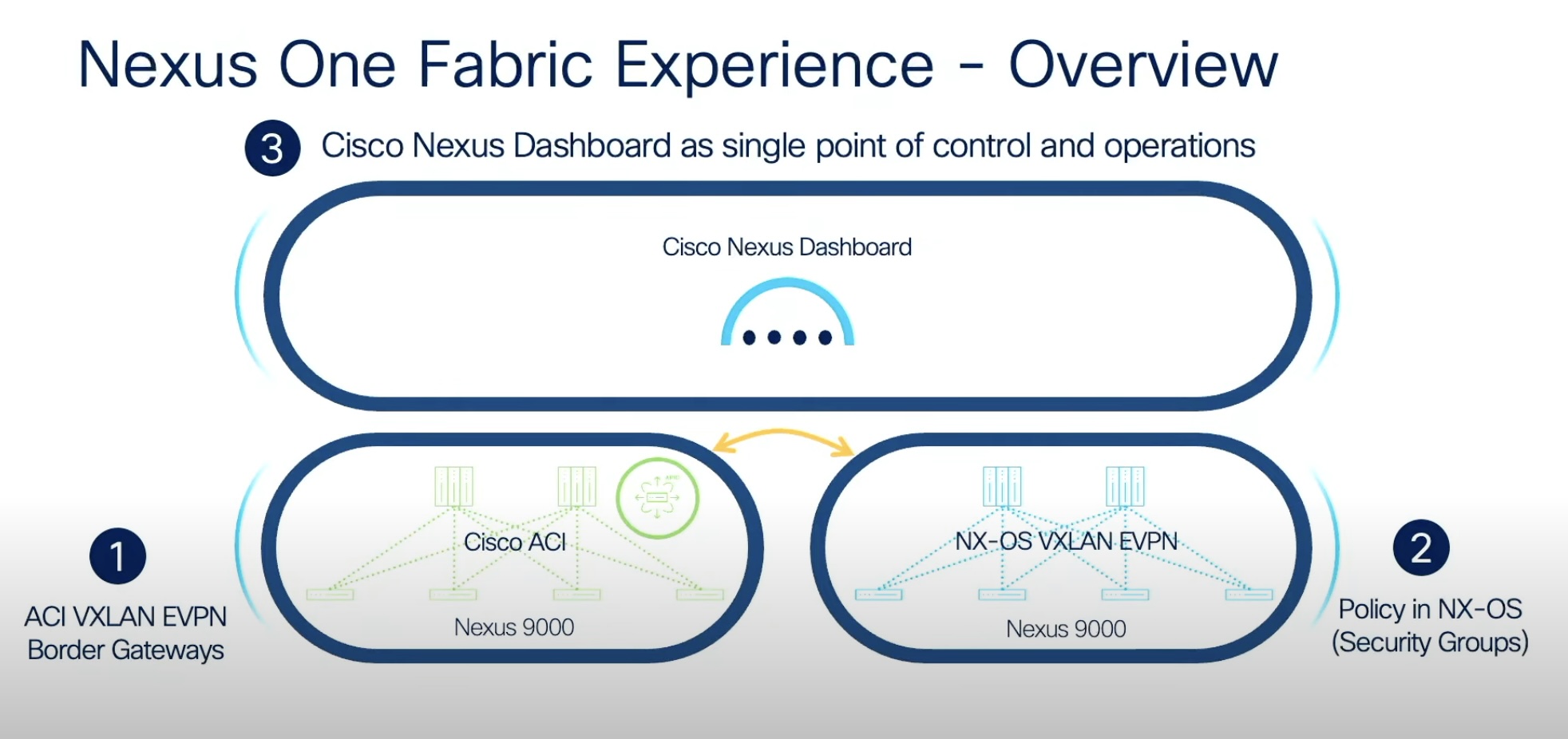
The inspiration for designing Nexus One Fabric Experience came from this: Cisco customers fall in one of three buckets – the ACI fabric users, the users of NX-OS with Virtual Extensible LAN Ethernet VPN (VXLAN EVPN) fabric, and those that deploy massively-scalable, large, routed fabrics.
What Nexus One Fabric attempts to do for each of these customers is offer “a unified experience that allows them to provision and connect application to these different fabrics and manage them in a seamless way,” said Max Ardica, distinguished TME at Cisco, while presenting the solution at the Tech Field Day Extra at Cisco Live US 2024.
Highlights of the Architecture
Ardica dug into the solution architecture that constitutes three core building blocks – ACI VXLAN EVPN Border Gateways, VXLAN GPO or group policy option (GPO), and the Nexus Dashboard.
The ACI fabric is perceived as a closed ecosystem that can only be linked to its own kind of fabrics. The ACI VXLAN EVPN Border Gateway opens up the ACI architecture allowing it to be interconnected with any standard VXLAN EVPN fabrics.
The gateway serves as the hook that establishes standard VXLAN EVPN connectivity between an ACI domain environment and VXLAN EVPN domain, he explained.
The ACI VXLAN EVPN border gateway behaves and functions essentially the same way as a fully standard VXLAN EVPN border gateway that Cisco has been shipping to build multi-site networks for the past 7 to 8 years.
“When you bring an ACI fabric together with VXLAN EVPN, you may have some conflicting resource ID like VXLAN IDs or group conflict,” Ardica noted. “We are going to build a namespace normalization translation function on the ACI border gateway that will translate to ensure that they can functionally operate as a single object even if they have been assigned different resources.”
Done this way, ACI and VXLAN EVPN will become “equal-class citizens”. The use cases formerly supported on ACI can now be extended to VXLAN EVPN.
An ACI fabric by design is zero-trust and identity-based. It is configured with endpoint groups or EPGs that are named logical entities for endpoint groups.
“When you want to establish connectivity between two endpoints, you need to map them to two security groups and create a contract.”
By contrast, VXLAN EVPN has a different design that de-prioritizes security. ““EVPN VXLAN has always been around connectivity layer 2 or layer 3, but the policy is never considered an important functional component,” he pointed out.
VXLAN GPO or group policy option allows security groups and contracts to also be enforced in VXLAN EVPN. This extension of policy makes for a unified policy domain end-to-end between the two heterogenous fabrics, allowing operators to centrally permit and deny traffic.
Customers can configure the VRF in two modes to enable GPO – deny by default, or permit by default.
“ACI is a whitelist model which means two different groups in ACI do not talk to each other unless you create a contract that allow them to talk. But we have customers who would like to start with a blacklist model where everything is allowed even if you create different groups and then just deny specific flows between these groups.”
Principal engineer, Matthias Wessendorf said, “We, from the beginning, started to decouple the forwarding from the policy because in ACI, the forwarding and the policy is coupled. Now the ESG or the GPO is across the forwarding, just defining the policy, and carrying the identity through the network.”
The Cisco Nexus Dashboard is the final piece that complete the solution. Designed to mask the differences in the fabric designs, it provides a single touch-point, offering a seamless policy management and provisioning experience without delving into the mechanics of different fabric types.
With the Nexus Dashboard One Fabric Experience, users can link two similar fabric types or two different types of fabrics depending on the use case. “You describe what you want to do and the system takes care of it,” Wessendorf said.
Know more about the Nexus One Fabric Experience by watching Cisco’s full presentation from the Tech Field Day Extra at Cisco Live US 2024 at the Tech Field Day website.

