Despite the extensibility and cost-effectiveness of the cloud, a common hang-up involved with cloud usage is its security, especially when it comes to the integrity and confidentiality of data in use. Although some companies simply accept the fact that entities outside of their organization have the potential to access their information, others can’t stomach the potential vulnerabilities that come with offloading to the cloud.
A few weeks ago, I wrote several pieces covering Intel’s exclusive Tech Field Day event where they announced the release of their new 3rd generation Xeon scalable processors, called Ice Lake. One piece, in particular, covering their Cloud Field Day appearance regarded Intel’s Software Guard Extensions, or SGX. Since then, I have had the opportunity to chat with Jesse Schrater, Director of Security Technologies from Intel, to learn even more about Intel SGX and how it can be used to support a zero-trust approach to security by safeguarding in-use data.
The Need for In-Use Data Protection
Protecting data, regardless of where it is, is critical to running a secure IT operation. For example, organizations have long been protecting data at rest on the hard drives of laptops and other computers through tools like Bitlocker or FileVault. These tools encrypt data while it is stored, preventing it from being accessed until an authorized user accesses the machine. That way, if the computer were to be stolen or otherwise compromised, the precious data stored on it cannot be lifted from the machine, making it into something akin to an expensive paperweight.
Protecting data in transit, such as across networks, is also crucial, but like at-rest data encryption, this has been at play for some time now. Using approaches like mutual TLS and others, data transferred between services and storage are protected from being accessed mid-transfer, reducing the risks of man-in-the-middle-type attacks.
The third form of data protection, covering data being used by applications or other processes, however, is the latest vector of attack from sophisticated adversaries. Data in use is arguably one of the most important forms of data to protect; when being accessed by an application or even manipulated by a cloud infrastructure service, data can be viewed and even written over by someone with malicious intent. That could mean a run-of-the-mill external hacker, an undercover malicious insider, or even an undetected malware virus.
Ultimately, because this data is actively being used by whatever endpoint is consuming it, protecting it has not been easy to achieve. That is, until Intel SGX.
Using Intel SGX for In-Use Data Protection
Originally created for protecting identities on laptop machines, Intel Software Guard Extensions runs on the CPU, whether it be a single core or several dozen. Since its inception, Intel SGX has been expanded beyond the initial small data scenarios it was created for and into big data environments — whether they’re in on-premises data centers or hyperscale cloud infrastructure. When configured, Intel SGX allocates a section of memory, now up to an entire terabyte, which is set aside as an encrypted data enclave.
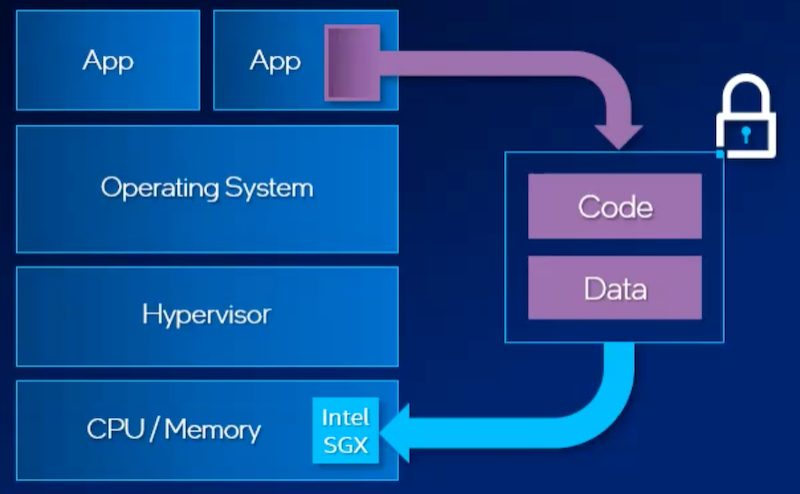
Now, what is a data enclave? It’s a secured data environment where applications can run and manipulate data completely secluded from other parts of the server stack. And, because it runs separately from those parts, the software can control who has access to it, cutting down on unauthorized access to data in use significantly.
Zero Trust and Intel SGX
This denial of entry to any non-approved user is exactly what makes Intel SGX such a powerful tool for a zero-trust approach to security. In zero-trust, regardless of where access attempts come from — inside or outside an organization — no trust should be granted to allow that attempt unless the user or machine attempting to access has established a trust relationship. With operations that rely on cloud-based infrastructure and applications, a zero-trust approach is useful in preventing security events that arise from practically any source.
Many of the most damning attacks we see today come from someone who leverages privileged access to enter the most critical parts of an organization’s infrastructure. Armed with these “keys to the kingdom,” a hacker or even a bit of malware can completely control the operating system and hypervisor of a server stack, allowing them free reign over the associated data.
Intel SGX fundamentally helps protect against these attacks — even if someone has completely breached your organization — by keeping the code and data that power your application secluded within the data enclave on the CPU/memory level of the stack. It completely bypasses the OS and hypervisor, reducing the trusted computing base (TCB) to solely the CPU and memory of a stack.
This differentiation is what makes Intel SGX so critical for zero trust. In essence, by cordoning off the data enclave, even a bad actor within a cloud service provider (Amazon, Microsoft, or Google even) with root access who can get into the cloud servers your application runs on won’t be able to access the valuable information inside. Intel SGX inherently runs with the least amount of trust necessary to ensure that your data remains as confidential as possible while being computed.
Intel SGX Use Cases
During my conversation with Intel’s Jesse Schrater about SGX, he detailed some of the key use cases of the product as they relate to the enterprise.
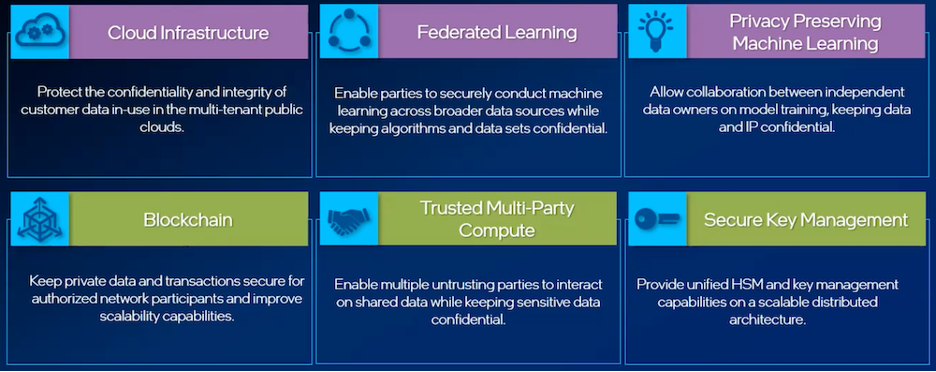
Cloud Infrastructure
The first of these, which is really more of a benefit than solely just a use case, is the securing of customer data within cloud infrastructure, the example that’s been laid out up until this point in the article. With so many organizations relying on the cloud, having a solution like Intel SGX creates additional assurance that data is secured, even though it isn’t under the company’s direct control. Such an approach allows IT departments to leverage the extensibility and mobility of the cloud without having to worry about who can access or alter their data. That way, instead of going back and forth about the usefulness of the cloud in comparison to its security, organizations can reap the full TCO of the cloud with little to none of the drawbacks associated with it.
ML / AI
Another important use case of Intel SGX’s confidential computing is for machine learning / artificial intelligence (ML / AI) applications. With so much data required to create working, accurate ML models, Intel SGX enables developers to keep their proprietary algorithms and IP separated from the data itself, allowing for the use of shared data sources to train AI models while still keeping the models themselves protected from being snooped upon or manipulated.
Blockchain
Expanding further, Intel SGX also provides similar security benefits to blockchain applications, which are sensitive to tradeoffs between integrity and privacy. By routing blockchain ledger transactions through the Intel SGX data enclave, the creation and alteration of ledger lines remain untouchable by those who aren’t allowed to. This approach helps with a couple of notorious issues faced by many blockchain users: speed and scalability. Intel SGX keeps the process of writing to a blockchain secure while also making sure the process is as smooth as possible, and since it can be leveraged at hyperscale, it means that blockchain networks can be ramped to similar scales while maintaining their integrity.
Multi-Party Compute
Intel SGX also proves useful in multi-party compute use cases where multiple parties need to interact with data in an application, but no one party has a higher level of trust than the other. This could be the case with competitors who must still exchange data, which has typically previously been solved with 3rd-party intermediaries. The data enclave of Intel SGX keeps the most sensitive parts of the process secured, even from the other parties in the transaction, while the outputs required by each party remain accessible.
Secure Key Management
In situations where multiple keys, like SSH keys or others, are being used to authorize access, Intel SGX allows admins to keep private keys locked away in a unified location, even while they’re being proffered to the targeted server or service provider
Zach’s Reaction
Having learned more about the immense benefits that Intel Software Guard Extensions provides by way of security, especially a zero-trust approach to security, I firmly believe that it is a necessary defense-in-depth addition to any enterprise. By protecting the confidentiality and integrity of the most crucial data and processes, Intel SGX ensures that no one can access critical information while it’s being used, and in practice, such a capability prevents some of the biggest threats to today’s organizations.
Learn more about the power of Intel SGX by visiting their website for more technical documentation and be sure to watch the video above and the rest of Intel’s exclusive Tech Field Day event for even more information regarding Intel SGX and the other facets of their Ice Lake launch.