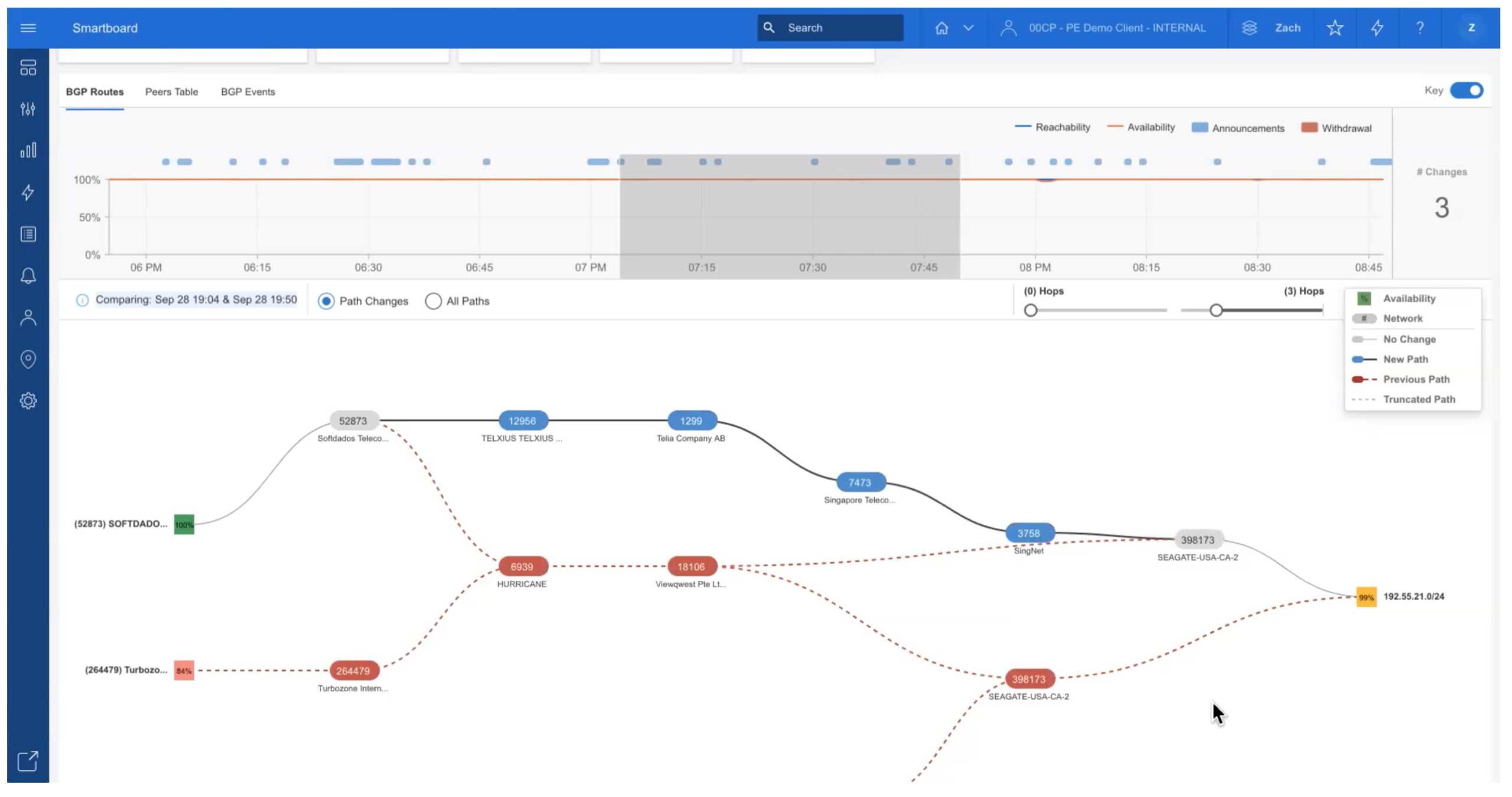
BGP is as important to the Internet as any other protocol. We learned that recently when Facebook decided to shut everything down because BGP and DNS withdrew all their routes. But the long history of BGP misconfigurations and malicious traffic hijacking attempts makes anyone that configures the protocol nervous when someone says the need to update the announced routes.
Why is BGP so flakey? Is it because it was created in a time when everyone was trusting of the rest of the computers on the Internet and we would never dream of someone stealing traffic? Is the extensible nature of the protocol to blame for creating complexity and the ability to introduce issues into the system? Is the lack of security and authentication going to cause more issues than we know how to deal with?
In this episode of Tomversations, I investigate how BGP is built and why it needs to be fixed soon to prevent the kind of attacks and issues that we see happening more and more frequently. I list some of the proposals in place to mitigate the trust issues and potentially solve the hijacking issues once and for all.