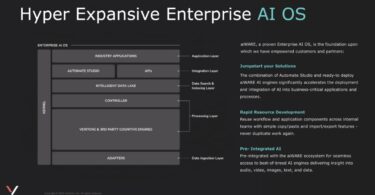
Veritone’s aiWARE platform stands out among new enterprise AI platforms with its decade-long...
Exclusives
Gestalt IT Exclusives are original long-form posts written by the Gestalt IT team and published here first. Exclusives are highlighted in our weekly Gestalt News email. Sign up today, or follow us on Twitter!
Commvault Shift 2024 Live Blog
Stay up to date on Commvault Shift 2024 by tuning in to our Live Blog.
Analyzing AMD’s $4.9 Billion Acquisition of ZT Systems
AMD announced that it is planning to acquire computer hardware design company ZT Systems, for a...
The Three-Way Monopoly in the Cloud
Cloud adoption is still at a nascent stage, but the level of competition is growing every day. To...
Digital Transformation, a Strategic Imperative for Businesses
In this exclusive article, Sulagna Saha writes about the essence of digital transformation, which...
Why Is No One Keen on Being a Network Engineer Anymore?
In this exclusive article, Sulagna Saha writes about the growing concern over the viability of...
Interviewing Brandon Heller of Forward Networks about Digital...
I had the chance to interview CTO and Co-founder Brandon Heller of Forward Networks during Cisco...
Securing Your Flow with RheoWorx from Entegria Systems
Transferring files between systems can be a hassle. Especially if regulations and privacy are a key...
Accelerating Information Acquisition with Prosimo Nebula
Multicloud networking is hard enough. Why not let AI help you understand the challenges and reduce...
Becoming a Handoff Hero with Swimlane Turbine
AI can help you write, but it can also help you figure out what other people wrote. In this...
Driving Sustainability in IoT Use Cases with LoRaWAN – A Chat...
Sustainability in tech has been a vigorously discussed and debated topic. In this Gestalt IT Tech...
Prioritizing Problem-Solving over Passing the Blame with Sam...
The Wi-Fi team encounters a host of tickets every day, some well outside their area of expertise...
How to Give a Tech Talk that Lingers with the Audience, with...
An outstanding presentation not only relays the message in the intended way, it also stays with the...
ACL Management at Scale with Invariant
If you've ever managed ACLs for a firewall you know there has to be a better way, especially at...
Preventing Attack Escalation with Network Segmentation – A...
An integral component of the zero-trust architecture is microsegmentation. In this Gestalt IT Tech...