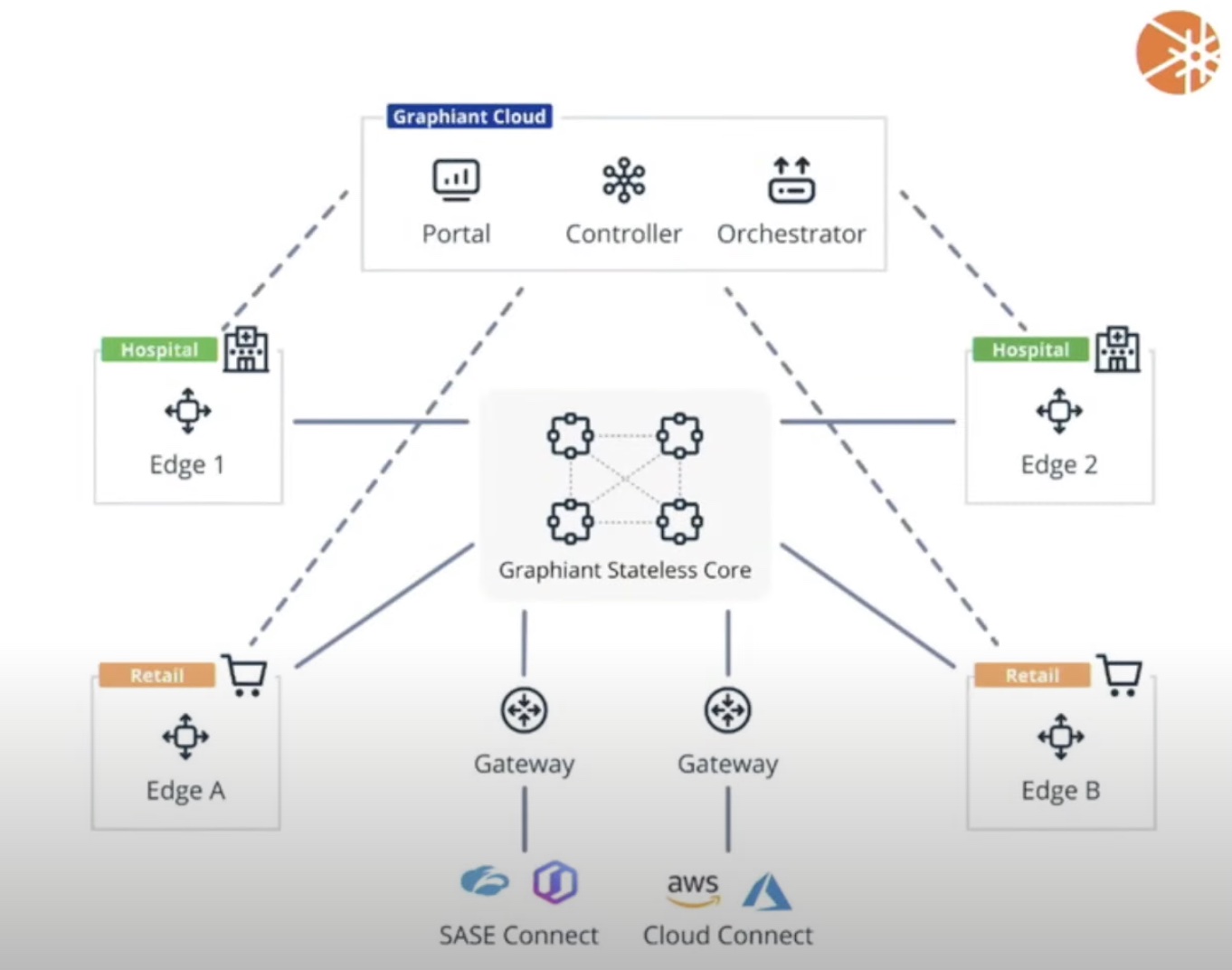
The modern-day network sprawl poses a daunting set of challenges for enterprises. Network engineers and security professionals are still grasping at straws trying to secure the network edge to edge in a way that security protocols and processes don’t get in the way of daily operations. At the recent Networking Field Day event which took place in Silicon Valley, Graphiant presented its Network Edge Service that provides an agile, secure and ready-to-consume network as a service. At the event, Graphiant’s Chief Product Officer, Ali Shaikh showcased the Graphiant Control Plane that eliminates disruptive per-hop encryption/decryption events while providing security edge to edge.
The Vices of Encrypting and Decrypting Data at Every Hop
Today’s network spans cloud, branch offices, remote users and the edge. With data traversing the network 24/7, tight security is paramount to preserve data integrity and minimize theft of information. Effective encryption is unbreakable, and as a result critical to secure data transmission, but an excess of encryption and decryption, especially when data is in transit can lead to very opposite results.
Multiple encryption and decryption is disruptive. It uses compute power unnecessarily and hurts performance, but most importantly, it raises the risk profile of the network. This happens when data plane is coupled tightly with the encrypt/decrypt boundaries of the network. Moreover, per-hop encryption and decryption adds overhead making data security costly.
Distancing the Encryption Problem from the Data Plane
Network-wide secure transmission of data will require setting up an end-to-end encrypted pathway and that’s exactly what Graphiant does. Shaikh explained, “The real problem that our Control Plane is meant to resolve is to make the encryption problem go away from the data plane.” In doing so, Graphiant eliminates decryption in transit.
Graphiant understands that securing a modern network is inherently complex with all the kazillion regulations involved. So, it built compliance into the Network Edge Service offering so that users by default are compliant from day 1. Using HSM and TPM devices only, Graphiant steers clear of generating keys or pre-sharing or storing them in unsafe locations. Shaikh says, “The key store is always on device in the HSM.”
This goes for both the hardware and the software. Graphiant has worked with Azure’s confidential computing group and AWS’ Nitro TPM when building out the Network Edge Service solution. Shaikh assures, “If you see our instance on the marketplace, it actually will always use the tamper-proof key stores for even our virtual machines because for us, data sovereignty and data control are very important.” So instead of keeping the keys, Graphiant puts them together in a key store that nobody but the administrators have control of.
Inside the Graphiant Control Plane
At the Networking Field Day event, Shaikh showcased the Graphiant Control Plane that comes with the Graphiant Network Edge Service. At the presentation, he detailed the mechanism by which Graphiant’s Control Plane encrypts payloads at endpoints while taking questions from the audience.
Graphiant makes a multitude of certificates of varying lifespans available in the solution by default. When a certificate is issued to the devices, connection is established with the cloud Control Panel. Users can access the portal using their respective login credentials, but beyond that, there are no pre-saved passwords in the environment.
Devices do not need to re-establish connection with the core network afterwards. The control layer provides the metadata information required for the communication.
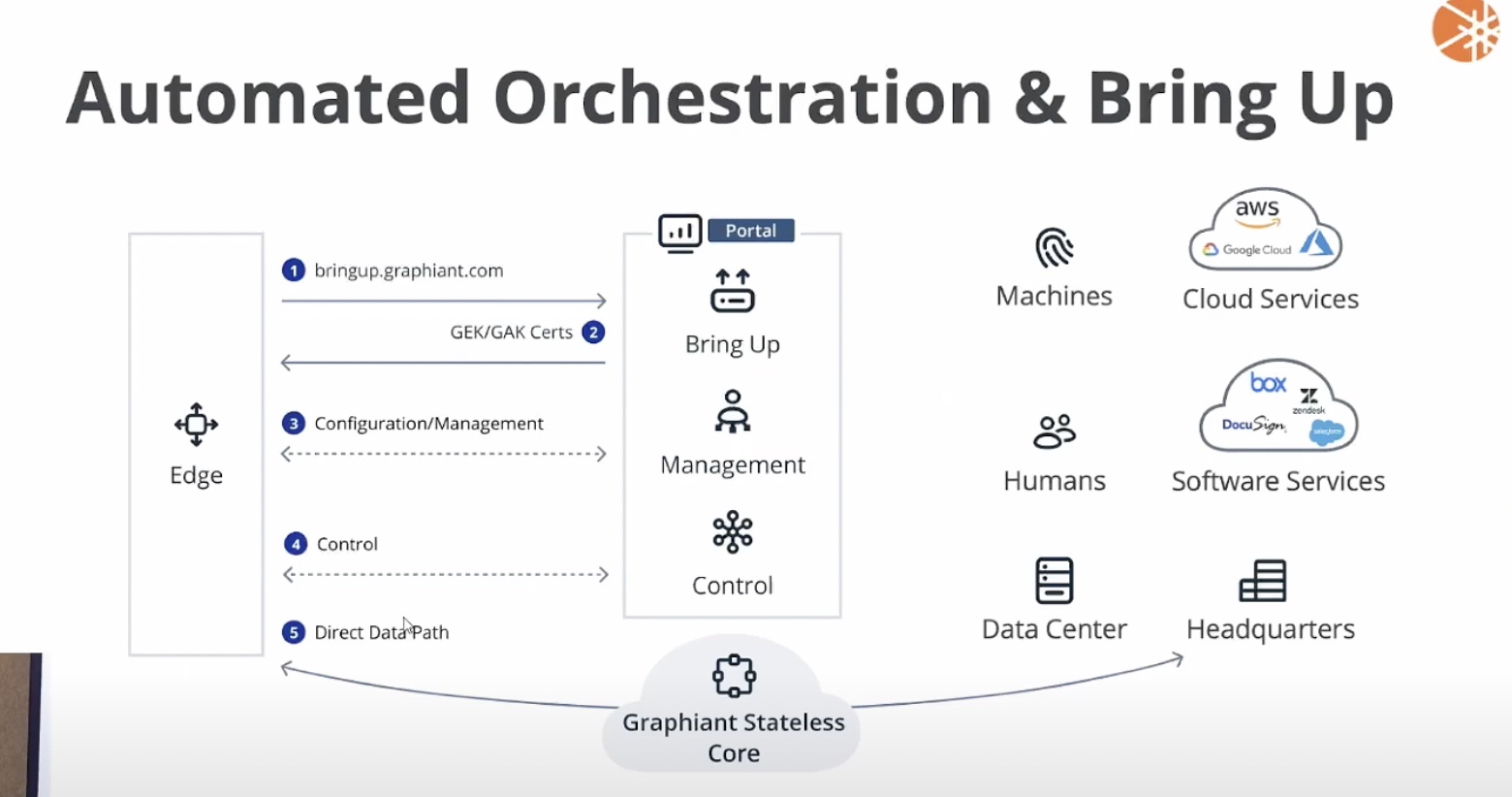
Graphiant uses an intelligent mechanism to transfer the key from one edge to the other. Leveraging the public key information already available in the HSMs at the edge, it establishes security association edge to edge.
This association is not to be mistaken for a tunnel. It is strictly a security association that allows encryption and decryption of data only at the endpoints, and through it, Graphiant encrypts all payloads traveling edge to edge without building a tunnel connecting the endpoints. This way, encryption and decryption of payloads happening at every hop between endpoints can altogether be eliminated.
Based on the latency between the endpoints and the cloud it’s communicating with, Shaikh says at each edge, the encryption and decryption events take a few seconds at most.
Wrapping Up
The practice of repeated encryption and decryption of packets in transit is a heavy burden on the security team. It not only leads to unpredictable delays, but also heightens the risk of data breach. By separating encryption from the tunnel, Graphiant Control Plane enables a secure and low-friction transfer of data through expedited encryption events.
For more, be sure to check out Graphiant’s other presentations from the recent Networking Field Day event.