The migration to cloud for enterprises isn’t always easy. It is critical that you match your needs to the available options for infrastructure. That means understanding the dynamics of what cloud offers. If you walk into a cloud migration project with an old mindset you’re going to end up costing the company time and money that could be better served in other areas.
That same lesson applies to security as well. The traditional thinking around creating perimeter security and keeping attackers out doesn’t address the ways that attackers are operating today. Gone are the days of compromising endpoints in the hope of gaining some foothold in the network. Today’s criminals want to break into your public systems and get credentials that can gain them access to other areas. They want to take your information and hold it for ransom rather than just locking down your systems in the cloud. They know that you can spin up new instances quickly. Your data, on the other hand, is almost priceless. How can you address these issues while still keeping your security team functional?
Cloud Changes Our Perspective
You can’t just apply old thinking to the cloud. False negatives are much more common because of the amount of traffic that needs to be sifted through to analyze traffic patterns. The way that we analyze the network traffic in the cloud has gotten much more complicated thanks to the massive amount of traffic flowing back and forth. Add in the way that we’ve adopted API-driven application usage and you can see why traditional security tools can be overwhelmed on the best of days.
Even if you wanted to approach the issue with modern tools you have to look at how you’re utilizing the cloud. Tools such as Endpoint Detection and Response (EDR) and Network Traffic Analysis (ETA) work great in a traditional environment. What if you’re using serverless methods now? Can you even install an EDR agent in a container? Would you know how to prevent that software from being compromised? Where would you look to find out if it had been?
The key to solving this issue is to look for solutions that are built for the cloud. One such solution was recently release from Data Theorem. I had the chance to sit down with Doug Dooley, Chief Operations Officer, to discuss their approach to solving the issues they see with the way cloud security is done in today’s landscape. Doug was also joined by AlphaSOC CEO Chris McNab. The two companies are partnering on Data Theorem’s Cloud XDR solution and looking to address the changing landscape of threat actors in the public cloud.
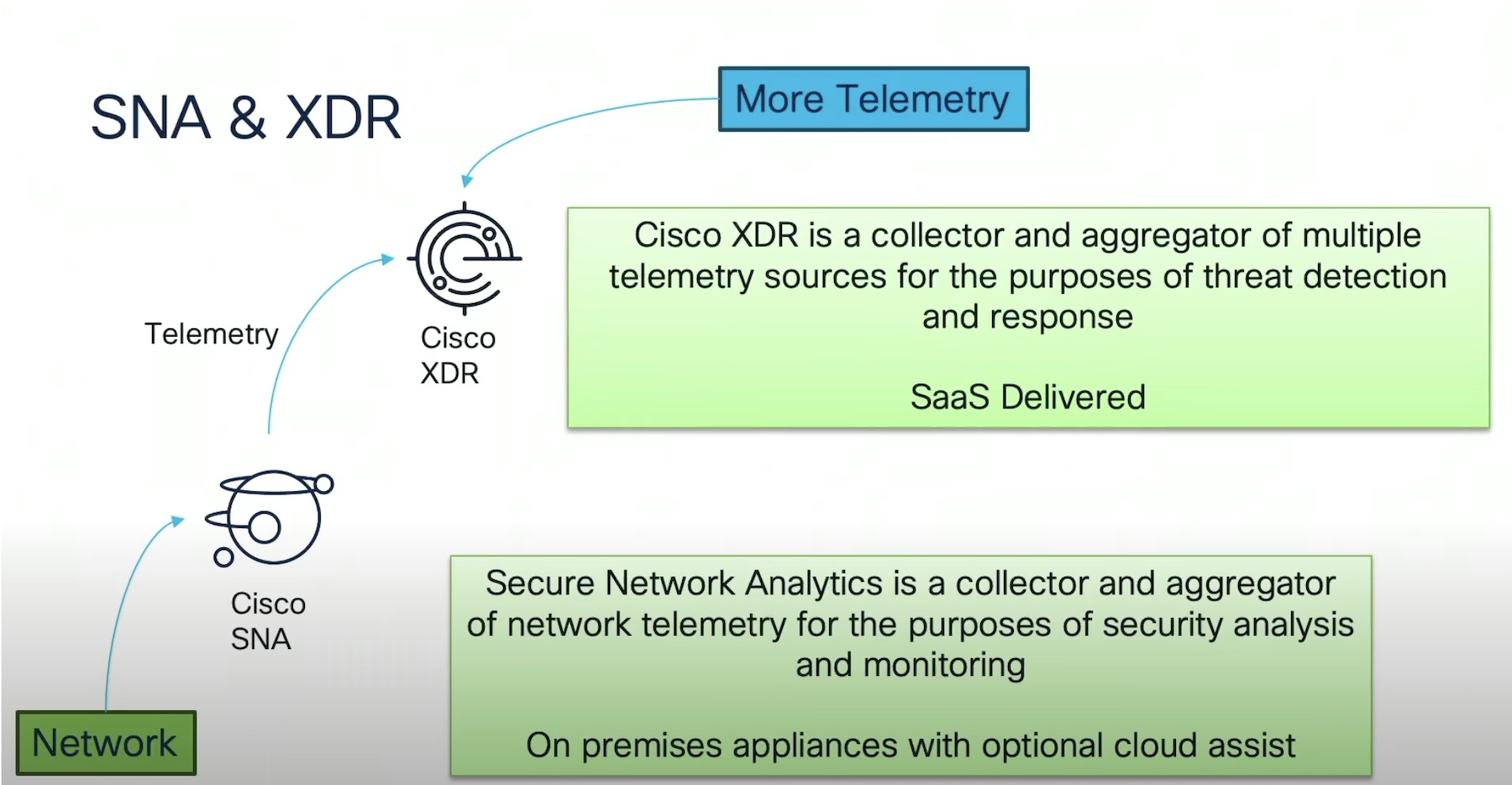
One of the things that Doug brought up is that traditional SOAR vendors are trying to stitch together a large number of tools. That’s what a SOAR is really designed to accomplish. However, trying to weave that fabric together is harder than most people realize. It requires time and skill and a lot of programming. XDR was created to ease the process and make it better for SOC teams to accomplish. However, XDR isn’t exactly magical either. Companies that just want to install an XDR agent on devices and forget about them are creating the kinds of issues that lead to embarrassing news stories. After all, XDR agents don’t work in a serverless environment either!
The way that Data Theorem approaches the problem is by rethinking what XDR should be doing in the cloud. The first step was to integrate cloud infrastructure entitlement management (CIEM) into their solution. This gives them visibility into everything you have provisioned in the environment. You can see what’s being used and what your potential attack surface looks like. More importantly it’s also visibility to the XDR solution.
XDR lives on data. You need to feed it valuable information to ensure it’s making the best decisions. That’s where AlphaSOC comes in. Their partnership with Data Theorem allows them to leverage the AlphaSOC Analytics Engine and analyze a variety of important cloud data, such as DNS queries and cloud services logs. This data can then be used in the XDR solution to examine potential threats and prevent them before they happen.
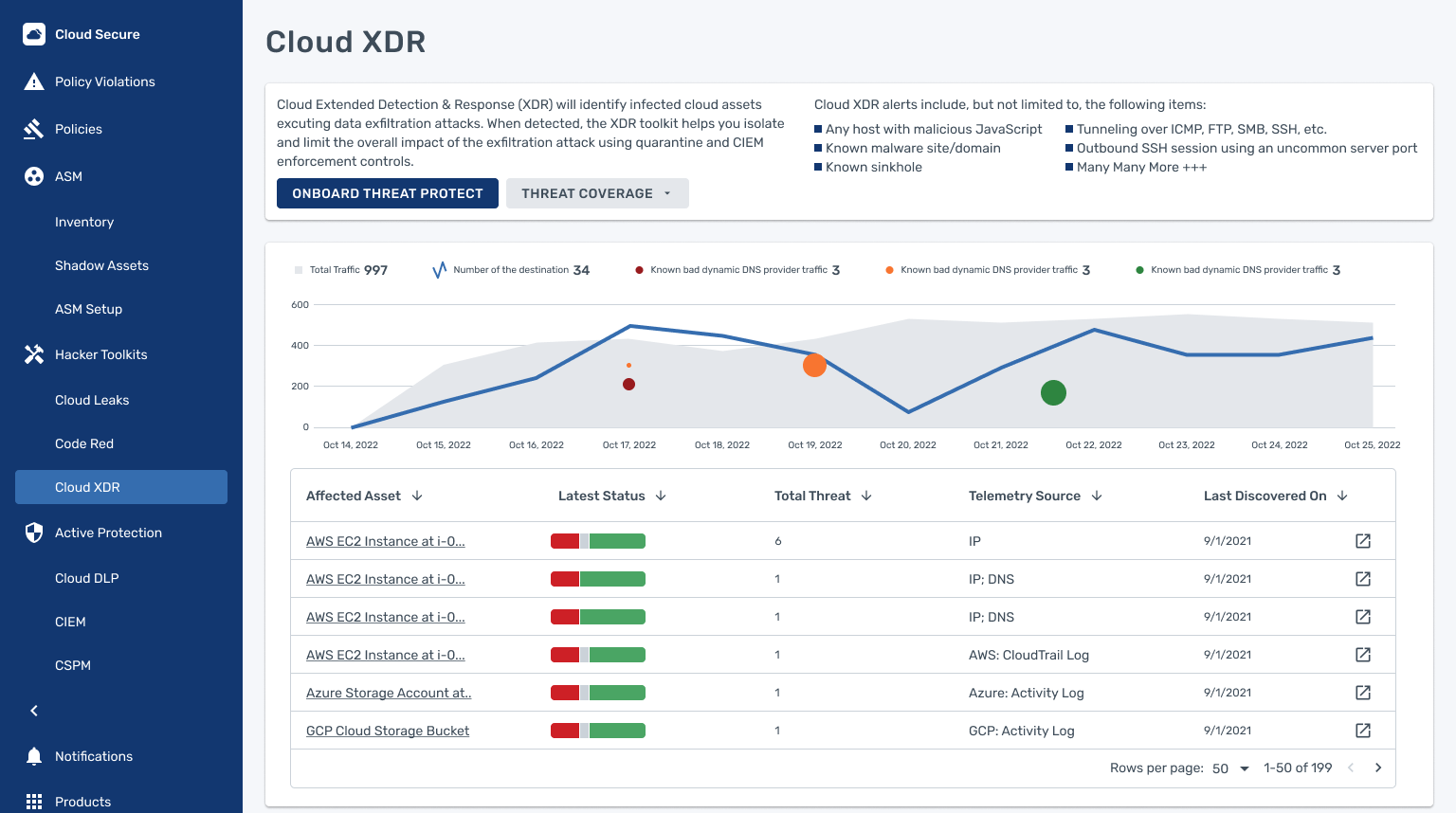
One example that Doug and Chris shared with me is data exfiltration. As stated earlier the real value in the cloud is stealing data and getting it out of your environment. The attackers want to compromise credentials and start accessing data to get it out of the cloud and into a location they control. They also want to set up command and control inside your environment to allow them to get back in and take what they want regularly.
Thanks to Data Theorem Cloud XDR you can now see what’s going on. You can see that data is moving somewhere it should be going. You can leverage AlphaSOC AE to notice that things aren’t adding up. You can also see if any additional resources are being spawned thanks to the integration between XDR and CIEM. In short, your SOC will be alerted and you can put countermeasures in place rapidly to prevent attackers from gaining a foothold and ransoming your critical resources.
Bringing It All Together
We have to shift our thinking when it comes to cloud. We can’t assume our traditional security infrastructure is going to save us. Likewise we have to realize that the changing environment also changes the way we need to secure our assets. Instead of looking at traditional solutions we need to look to the future. Data Theorem has an excellent platform with Cloud XDR and and a wonderful partnership with AlphaSOC. Make sure you check it out if you’re trying to keep your cloud environment safe and sound and make sure your data stays where it’s supposed to be.
For more information on Data Theorem Cloud XDR, make sure you check out their website at http://DataTheorem.com