The world is caught in a maelstrom of savage cyber-attacks. Reports from leading threat intelligence firms show that more companies were illegally hacked in the recent months than in years. With stories of brutal attacks emerging every day, and companies’ defenses failing increasingly to clever attack mechanisms, the prospect of attack on big corporations and small firms are at par.
A more robust effort is required to counter the ceaseless attempts of breach. As attackers pull off notorious feats of swiping out corporate secrets, sabotaging power grids and pipelines, and commandeering control of guarded systems, CISOs are leaning towards more meticulous security practices.
The drill begins with setting the bar high for security requirements, and streamlining and heightening all internal security protocols. But this is easier said than done, as accelerating security operations places too much burden on the security operations center that is already tasked with monitoring, and addressing events 24/7.
The OODA Loop
To elevate security and counter high-stake situations, a lot of companies have absorbed a military strategy known as the OODA loop into their cyber design. A four-stage linear cycle designed to enable proactive decision-making, it constitutes the steps of Observe, Orient, Decide and Act.
As strategically sound as it is, mastering the OODA loop is the bulk of the work. To achieve speedy decision-making which is the goal of the loop, an enterprise requires to corral massive amounts of threat intelligence and analytics.
At the recent Tech Field Day Extra at Cisco Live US 2023, Mathew Robertson, Distinguished Engineer at Cisco, tapped into this discussion. “Analytical outcomes are driven by data. If you say you want a very specific type of detection, you may need very specific types of data,” he commented.
For enterprises, the biggest ordeal remains executing the OODA loop quickly and effectively. In the session, Robertson presented two of Cisco’s solutions – Secure Network Analytics (SNA) and Cisco Extended Detection and Response (XDR), both designed around enabling a swift and speedy execution of the OODA cycle.
Data as the Most Important Piece
Typically, the OODA loop starts with Observation, a stage where when a piece of evidence arrives indicating a breach or compromise, the security personnel get to figuring out what it implies for the organization.
At the high level, SecOps has two primary objectives – to understand past exposures, and monitor and control all ongoing exposures, because when a security incident strikes, CISOs want to focus on two things only – the consequence it will engenders, and how that will impact the business.
The quest to finding the answers of who, what, when, where, why and how of an attack is what data collection is about. Roberson noted, “Accelerating security operations is all about getting data into the hands of analysts, and presenting it to them in a way that they understand it.”
Here is how the OODA loop is implemented in the context of security: All relevant data inputs are brought in, data points are oriented in business context, SecOps arrives at a decision, and finally the decision is executed.
A Joint Solution
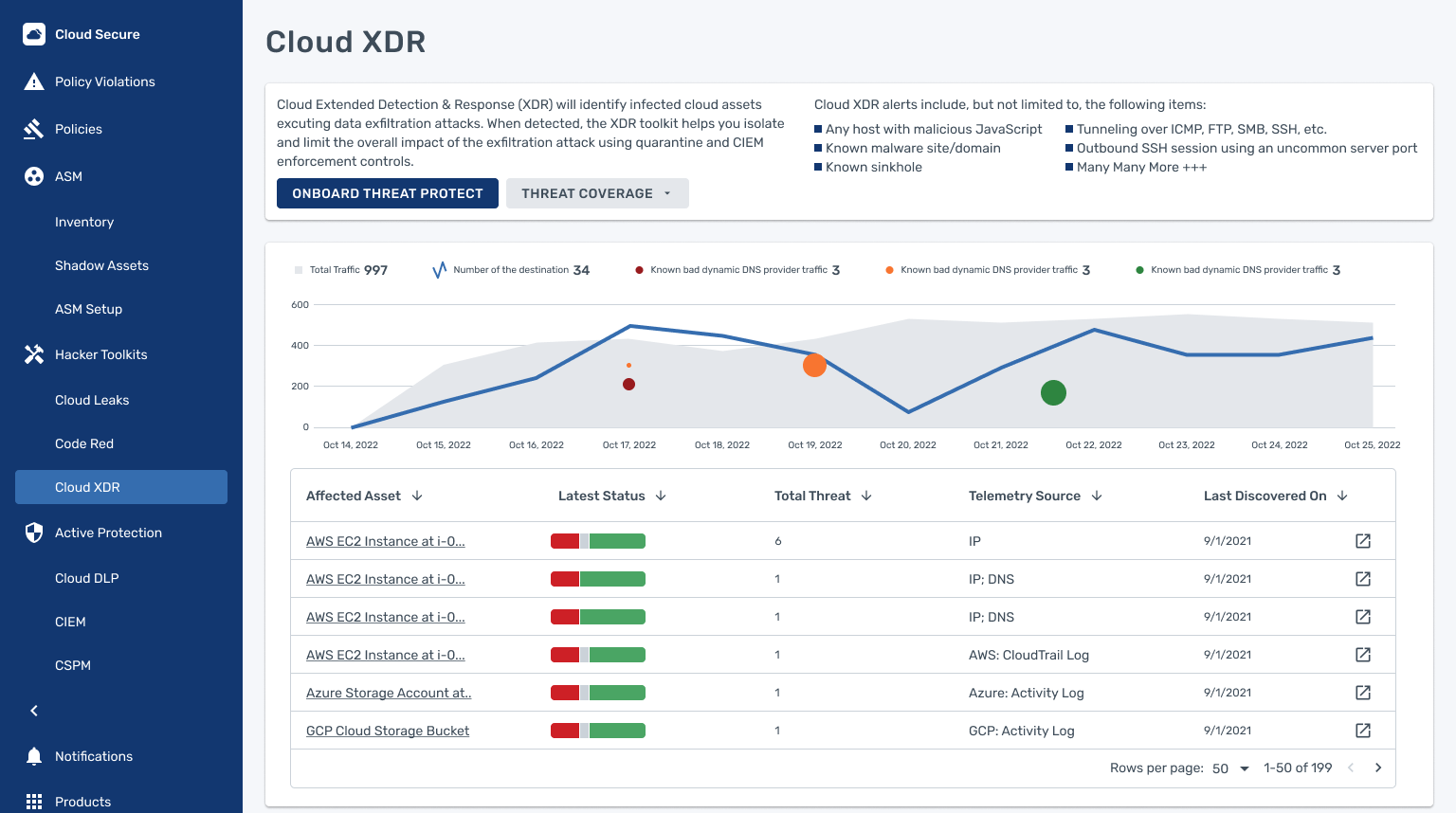
Cisco is known globally for its exhaustive line of networking solutions, and has a reputation of trust and integrity among its customers. When it comes to full-stack observability, it has an impressively wide product line. The newest addition to that is the Cisco XDR – a solution designed to assimilate data from disparate tools and produce intelligence.
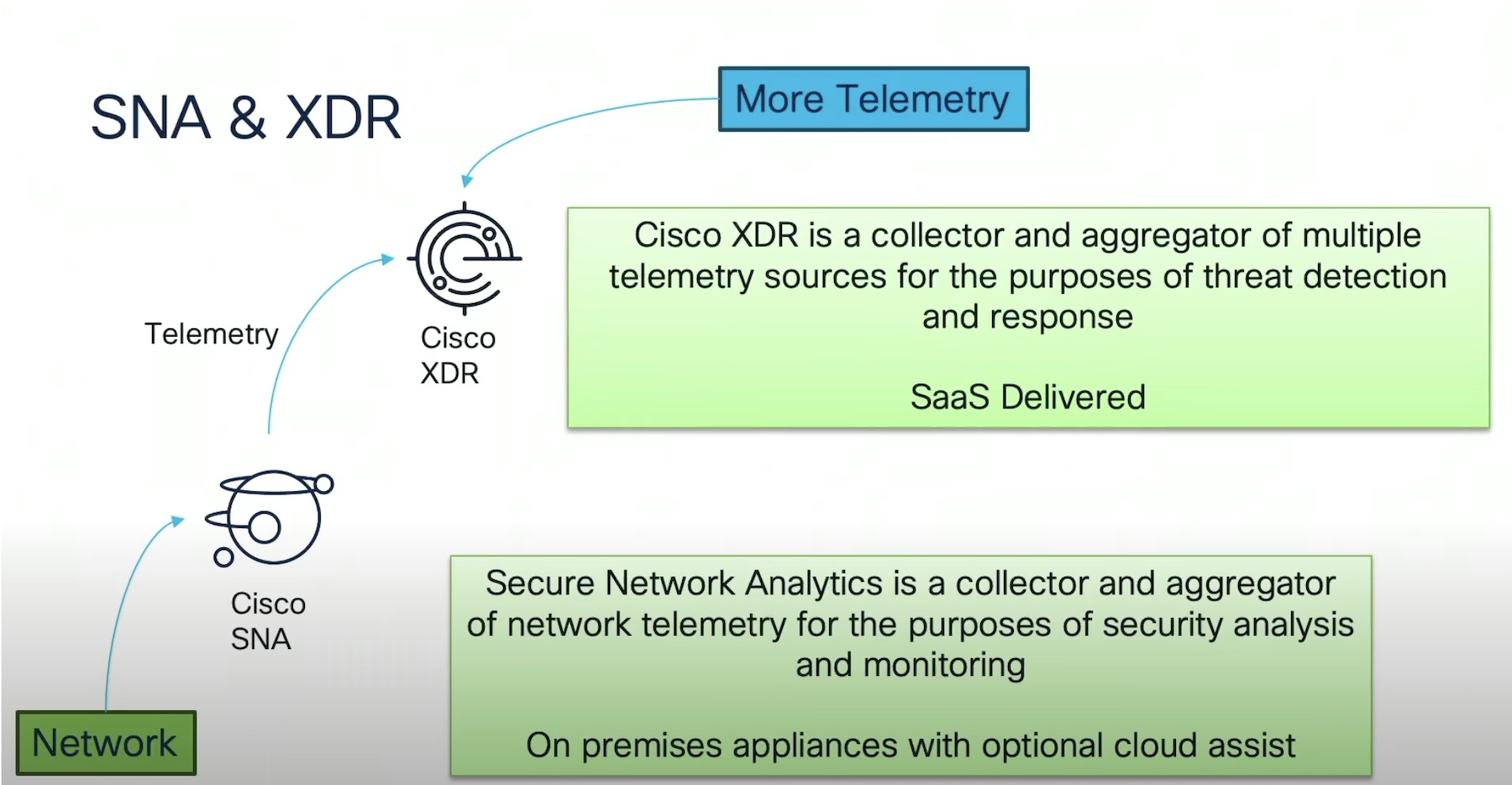
Cisco XDR works in tandem with a much older solution, the Cisco Secure Network Analytics. Been around 23 years, Robertson explained that Cisco SNA is a collector and aggregator of network telemetry that provides broad security analytics.
Cisco SNA is an on-premises appliance that is widely used for the purpose of monitoring. SNA ingests network data from multiple sources, stores it and applies analytics on it to produce information that provides specific threat detection. With its optional cloud assist, users can integrate it with Cisco XDR.
The new SaaS delivered Cisco XDR works hand in hand, collecting and aggregating data from multiple telemetry sources, and determining the maliciousness of a component, driving prompt response.
Cisco understands that when it comes to security, the end goal is just accumulating massive amounts of data, but what you do with it. “It’s about delivering outcomes with the data that you collect,” noted Mr. Robertson.
Cisco SNA is a form of stealth watch that uses NetFlow/IPFIX as the primary data input. SNA also has the ability to ingest NVM logs from Cisco Secure Client and firewall logs. Optionally, users can make use of the Cisco Telemetry Broker that enables ingesting data from multiple inputs in a standard format.
Data is synthesized, correlated and stored in a flow table. SNA measures all data against the network’s baseline behavior to discover anomalies. The data collected can be stored in a central data store which is a high-performance data redundancy system, or collected data via single appliance flow collectors. Users have the option to scale the system horizontally by bringing in additional flow collectors.
More options are available to streamline the data. “We have recently introduced something called Essential Data Store that allows you to separate collection and storage into multiple physical or virtual appliances,” said Robertson.
Three detection engines running on the flow collector filter and clean the data, while a central manager – a VM or a physical appliance – manages the deployment. The manager features an analytics node that runs against the central data store applying analytics on enterprise-wide data as opposed to analyzing isolated packets of data coming from individual flow collectors.
Via Smart Assist Service, operators can also turn on global threat alerts, an ML-based cloud service that does active profiling of worldwide threats.
The biggest value of Cisco SNA is that it can make specific detections from specific types of data. It’s unique data processing allows it to capture unique datasets from a multitude of data exporters that report data differently, and analyze it uniformly.
The recently launched Cisco XDR collects telemetry from multiple data sources such as the network, endpoints, cloud and other sources that it is integrated with, and analyzes it to surface threats and incidents. But before the alarms reach the operators, XDR enhances and prioritizes the threats paving the way for faster remediation.
Wrapping Up
With Cisco’s twin solutions, operators have the resources they need to monitor the network and its assets in real time. By refining and enriching data through aggregation, correlation and prioritization, the solutions make the job of security professionals a lot easier, driving them to swift decision-making and prompt responses. With their pinpointed detection, it is possible to find weak links and cloaked threats automatically, and prevent jeopardy of the entire stack. Together, they make adoption of high security standards involuntary.
For more on Secure Network Analytics and Cisco XRD, be sure to watch the presentations from the Tech Field Day Extra at Cisco Live US 2023 event at the Tech Field Day website.