You may have heard of a Router-on-a-Stick before. It’s a network configuration trick to configure routing for two different networks when you only have a single interface on a router. We’ve done it for a number of years for things like voice networks when we’re limited on resources. However, it’s been so long since routers have only come with a single Ethernet interface that stick routing has mostly become a configuration oddity.
However there is one device that is still in wide use that has a single network interface that benefits greatly from this old routing trick. The Raspberry Pi is the most popular small computer for hobbyists as well as for IT pros that need to deploy basic compute to some interesting locations. However, the lack of multiple Ethernet interfaces makes it hard to deploy as a router. Looks like we’ve found a great reason to resurrect the router-on-a-stick for a computer that can easily fit on one!
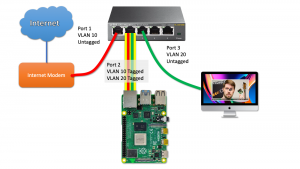
Louwrentius has an excellent write up on how to configure the Linux OS running on a Raspberry Pi with VLANs and routing protocols to make this a reality for you. Here’s an excellent excerpt from his post:
As you can see, the VLAN packets that arrive as tagged packets, are send (without their tags) to a virtual network interface belonging to that particular network. Those virtual network interfaces all share the same physical interface (enp2s0f0). The virtual network interfaces are just the physical interface name with “.(VLAN ID)” added.
From here on out, you probably understand where this is going: those two virtual network interfaces are basically similar to a setup with two physical network interfaces. So all the routing and NAT that needs to happen, just happens on those two virtual interfaces instead.
Make sure you read the entire article for configuration snippets and theory behind why the Pi makes a great router: Raspberry Pi as a Router Using a Single Network Interface

Yep! So many great reasons to put things “on a stick”. Firewalls are a big investment in a branch, so we don’t invest in HA. It sits on a stick, gets bypassed when it fails where the internet traffic goes to the cloud for inspection as a backup. Firewalls don’t tend to have fail-to-wire interfaces so best not to have them in-line especially if you only have one of them.
It can also be used for internet circuits. L2 extend the circuit, so multiple devices can use it without having something in the middle. Get a /28 or /29 from the provider and use that circuit to provide a public IP to the firewall, SD-WAN router, temporary laptop for testing, monitoring, etc. Firewall fails? SD-WAN will take care of that traffic for you. SD-WAN / Router fails? At least your firewall is still providing internet access and potentially tunnelling traffic for you to a backup entry point in the network. Rely on dynamic routing to determine when to insert devices and where they should be in the north-south network boundary.