Redundancy is becoming more and more important in the app-focused world of the enterprise today. No one cares about storage replication or multipath traffic or even fault tolerance. They just want the app to be available like their favorite one they download from an app store and install. It never goes down, right? Well, that is the case when all of the above things they don’t really care about are taken care of.

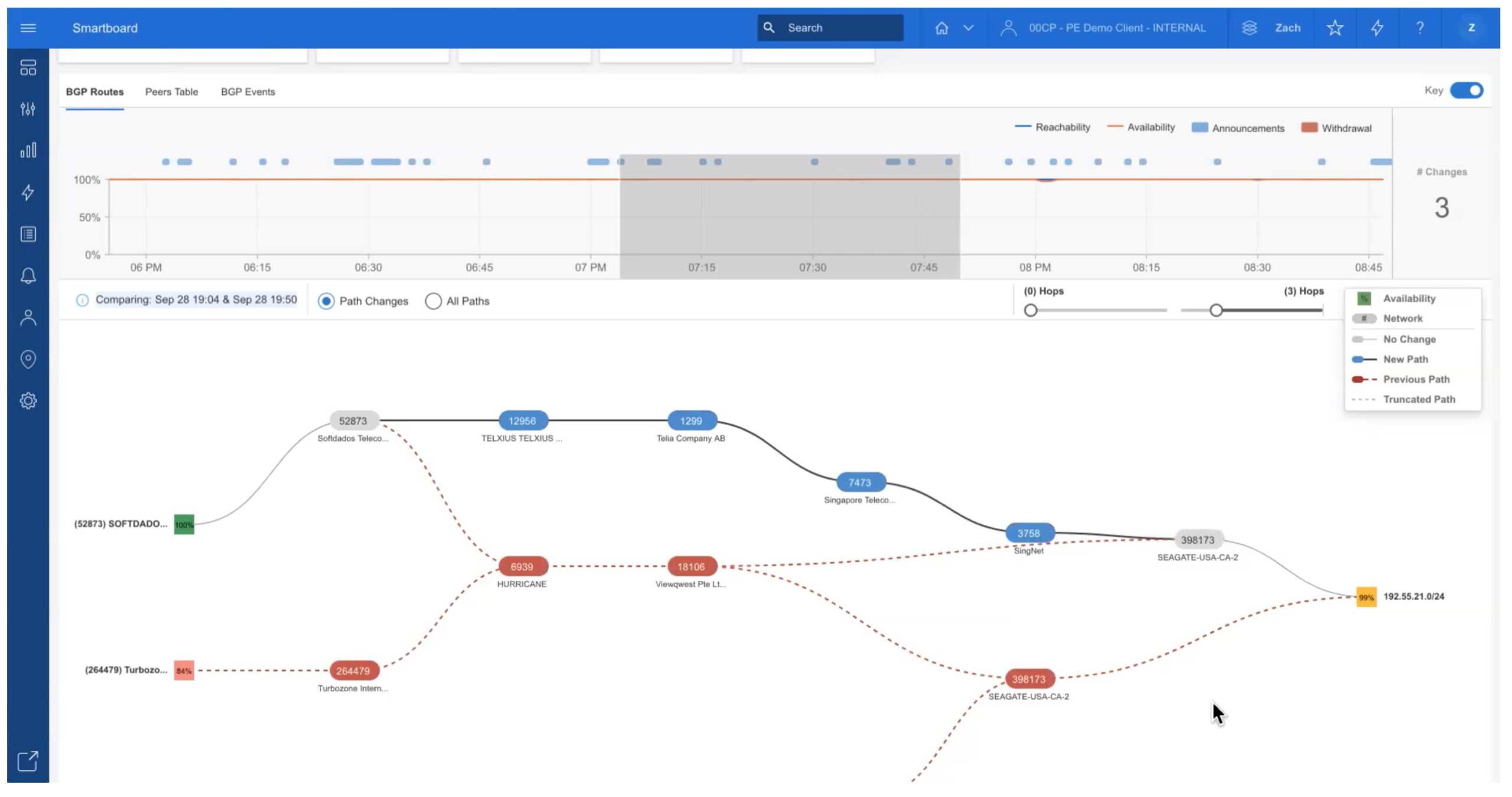
One of those huge issues is how configure your system to send traffic through firewalls and ensure that primary and failover sites are doing what they’re supposed to be doing. That’s fine if the sites are in the same network, but unless you’re stretching your network over an interconnect link you’re probably not going to have that setup. Instead, you’re going to need to use an exterior routing protocol to ensure that traffic is flowing properly. And that means BGP.
Before you freak out and run for the hills instead of configuring this esoteric and unctuous relic of the pre-cloud Internet, make sure you take a moment to read up on using BGP communities to do path steering to help with your firewall configuration. Vince Schuele has done an amazing job of consolidating what you need to know into an easy-to-follow post. Here’s a great excerpt of some things you need to keep in mind:
With two firewalls it is easy to introduce a state problem and have packets rejected because of invalid state. When a packet ingresses one firewall and egresses another this introduces the problem as firewall 2 does not have a session for the flow. “How come we don’t run an HA pair?” is a common question; these might already be an HA pair and you’re preparing for a migration, they’re different vendors, or they’re in different data centers completely.
Read more to find some configuration examples and some gotchas that you want to make sure you watch out for: Utilizing BGP Communities for Traffic Steering – Part 1: Firewalls