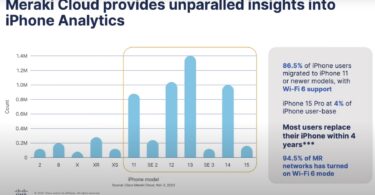
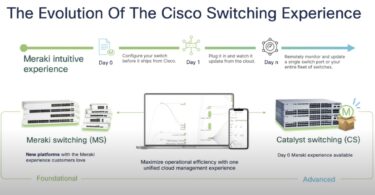
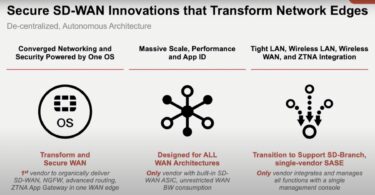
There is a growing consensus that security needs to shift left in the software development...
Latest Articles
AI Is Going To Make Malware Worse
AI is going to accelerate development of malware everywhere from code to prompts for social...
Improving the Accuracy of Domain-Specific Information of Large...
This article follows Ben Young’s journey of building a chatbot web interface for Veeam knowledge...
Next-Level Client Wi-Fi Visibility with Cisco’s Three-Way...
In this article, Sulagna Saha discusses data-driven enterprise Wi-Fi monitoring and optimization...
Meet Jon Hildebrand, Senior Product Architect at 11:11 Systems
Stephen Foskett sits with Jon Hildebrand to discuss the prevalent misconceptions surrounding...
Catalyst Gets a Meraki Makeover with the Catalyst 9300-M Switch...
In this article, Sulagna Saha reviews the Cisco Catalyst 9300 series switches that combine the high...
Intel’s AI Ecosystem and AI PCs | Gestalt IT Rundown:...
Intel has been stepping up their game in the AI ecosystem. Both Meteor Lake and the latest Emerald...
Your IT Security Policy Needs to Be Followed
IT security policies are aspirational goals because they have so many exceptions. The difference...
Meet Mike Bolitho, Wireless Engineer
Meet Mike Bolitho, a wireless engineer for a major medical company. He sat down with Tom...
Top Enterprise IT Stories of 2023 | The Gestalt IT Rundown:...
It has been a big year in the enterprise IT industry for many reasons. Pat Gelsinger and Intel...
Networking and Security Come Together with Fortinet Secure SD-WAN
In this Networking Field Day article, Sulagna Saha discusses how Fortinet brings Networking and...
It’s Always the Wi-Fi
Users are always going to blame the connectivity medium for issues and we just have to accept it...