The journey that software developers have been experiencing with their hardware is long and winding. Only a few years ago it was difficult to get the right kind of support for their development and deployment needs. Organizations needed to buy the right servers and networking equipment and deploy it in order for the applications to run correctly. With the advent of new platforms like those found in the cloud, the need for hardware procurement became much less important.
Thanks to public cloud providers, developers can purchase server resources, develop applications, and run them with almost no effort required to build out hardware infrastructure of their own. This ease has led to the focus of a software application changing from the capabilities of the infrastructure to the limits of the developer imagination. With the freedom of platform independence, the view becomes based more on the application itself.
This shift in viewpoint has led to applications becoming more modular and easier to deploy. Instead of thinking about software in terms of how many servers it takes or how much storage is needed, developers have started using microservices models to build scalable programs that can be used by any number of users or organizations of any size. If you need more capability, you just need to bring more modules online. These microservices containers make it simple to build code that can run anywhere.
Securing Services
No matter the location of the program code, security is still a major concern. With the amount of data being generated and analyzed in the modern application it becomes paramount that you must ensure that information is protected at all costs. Containerized workloads make it easier to deploy services but harder to track what is in use and how long it has been there. Proponents of these new software architectures will say that the ephemeral nature of microservices makes it harder for them to be hacked. However, that same nature also means it is harder to detect when those same services have been violated.
It’s not just the data that attackers are looking for. The intellectual property of your organization is as valuable as the information it helps to generate. The race to create new software or applications or even algorithms to make use of data collection and understand your userbase is heated. If you have an edge on that market what is to stop some unscrupulous people from trying to obtain that IP from less-than-legal means? If the attackers were able to nab their information from the cloud by capturing a container would you even know what happened?
One of the biggest targets that attackers are looking to exploit is memory. If the application is doing any kind of work, it must do so in the system memory or store data in a CPU cache. If attackers are able to write tools that allow them to violate these shared areas, they can get access to anything being analyzed by the software. This means that these spaces need to be secured against other programs reading from areas not allocated to them. The nature of RAM and cache makes this difficult under the best of circumstances.
This exploitable hardware issue requires a hardware solution. How can you protect memory from other programs? How can you ensure a zero-trust architecture for a CPU cache? With containers relying on the infrastructure without any visibility into what’s going on, how can you solve this problem without modifying them and making the entire system less flexible or less scalable?
Intel SGX Secure Enclaves
It’s no surprise that Intel is one of the best when it comes to making hardware that meets the needs of developers looking to do advanced operations with software. The list of advancements that Intel has developed over the years to increase performance and provide utility to those that write software is long and impressive. Intel also realizes that securing workloads is the responsibility of every part of the IT infrastructure stack. That realization has led to Intel Software Guard Extensions (SGX) which solves for the problem of shared memory exploitation, thereby securing data while it is resident in memory. SGX allows for the creation of secure enclaves that are encrypted and unreadable to any programs that do not have the key to decrypt the enclave. This means that the execution of secure workloads truly has isolation from any other processes running in memory.

The first thing that might come to mind when you think about secure memory isolation of these workloads is protection against hackers. This is another angle I find exciting. For a number of organizations there is a significant challenge in sharing data, especially data related to customers. The easiest example of this is something like a patient record in a healthcare environment. This data is very important to the patient and very critical to the operation of the healthcare organization. However, most of these organizations don’t focus on the kind of analysis that could provide insights into the health and well-being of a patient. They rely on third parties to do that work. How can the organization ensure the security of the data as it is being analyzed?
With Intel SGX, you can not only secure data against exposure but you can verify access for third parties using the attestation capabilities of SGX. If you want to secure the amount of data that the outside party can access and set a limit on how long they are able to analyze it, you can do that. Set up an SGX enclave for them and when the window of time has expired all you need to do is revoke the key. The data is then secured and you can verify that no one else has access to it. Since you are the one that generates the key, you can also verify that the data was accessed at a specific time. This helps confirm the outside organization did the work they were supposed to do and provides positive confirmation for any audits done at a later date.
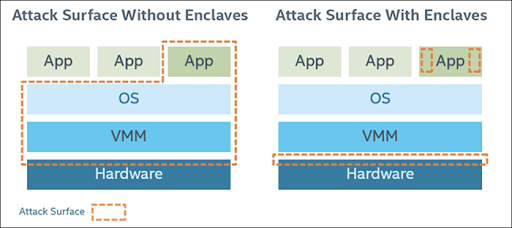
This kind of compartmentalized access to data works in concert with the container development method. Because the services for the application are scalable you can provide a number of SGX enclaves of varying security for access. You can protect some data with one enclave and require a separate enclave for more sensitive information. You can set keys for both and even create keys for specific users to prevent data leakage between them. Intel has been doing this kind of work already for medical researchers to use advanced AI algorithms to do research to help increase medical science in the future.
Bringing It All Together
Intel SGX is a hardware security solution that has significant potential to secure microservices and containerized workloads. The development of technology to create zero trust architecture for the most shared spaces on a system means that we can begin to think about data security in new ways. We can build isolation and access rights and verify that data is truly safe at every point of the journey from creation through use and eventual retirement or long-term storage. We can also provide access levels for the data to help further isolate those workloads to provide true “need to know” access and revoke it when necessary. With the work that Intel has provided and the effort they have put in with the Confidential Computing Consortium, there is a bright future for Intel SGX on the horizon for security professionals.