Monitoring network traffic through metadata is by no means a new concept; Cisco’s NetFlow was launched over 25 years ago, and in the years since, solutions such as jFlow, sFlow, IPFIX and Netstream have all been developed as alternatives or improvements by other vendors. While flow records themselves are not new, Progress believes that Flowmon offers unique visibility into data flows, network security and application performance all in one platform. These tasks typically require multiple parallel infrastructures, so Flowmon is absolutely positioned as a triple threat in the monitoring space.
Scalable Architecture
Flowmon is based on two key components:
1) The Flowmon Collector, which can accept data from:
- NetFlow, sFlow, IPFIX (usually generated by network devices)
- Native cloud flow logs
- AWS vTAP port mirroring
- A Flowmon Probe
2) The Flowmon Probes, which can monitor interfaces from 10Mbps to 100Gbps and accept full mirrored packet flows. The Probes generate their own flow records to send to the Collector, analyzing packets at a deeper level than regular network devices (for example, they analyze TLS flow data). The Probes can also ingest IDS event feeds (e.g., from Suricata) to integrate with the flow data. This goes well beyond the typical “endpoints and byte count” metadata one might be accustomed to.
A simple Flowmon architecture might look like this:
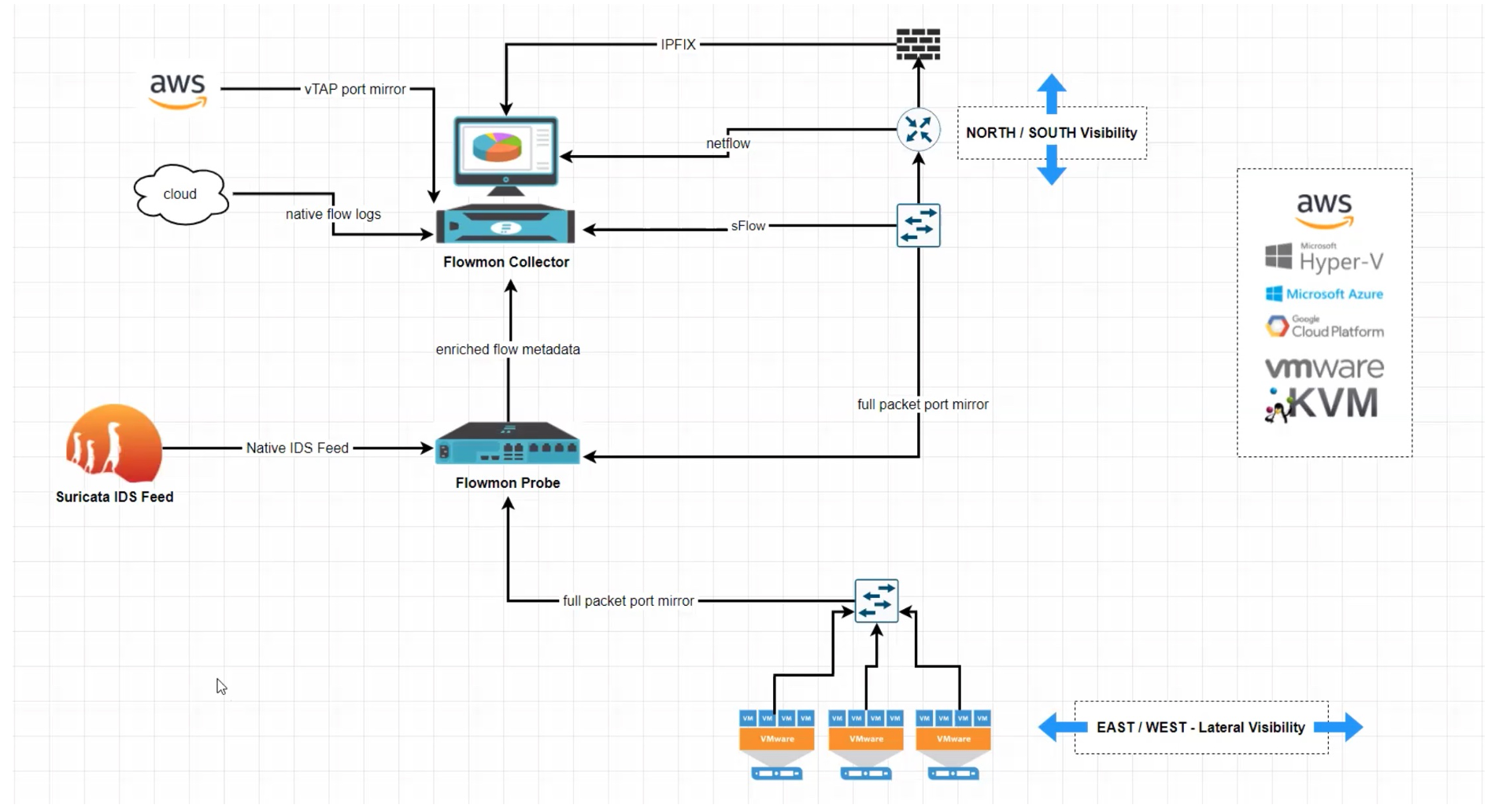
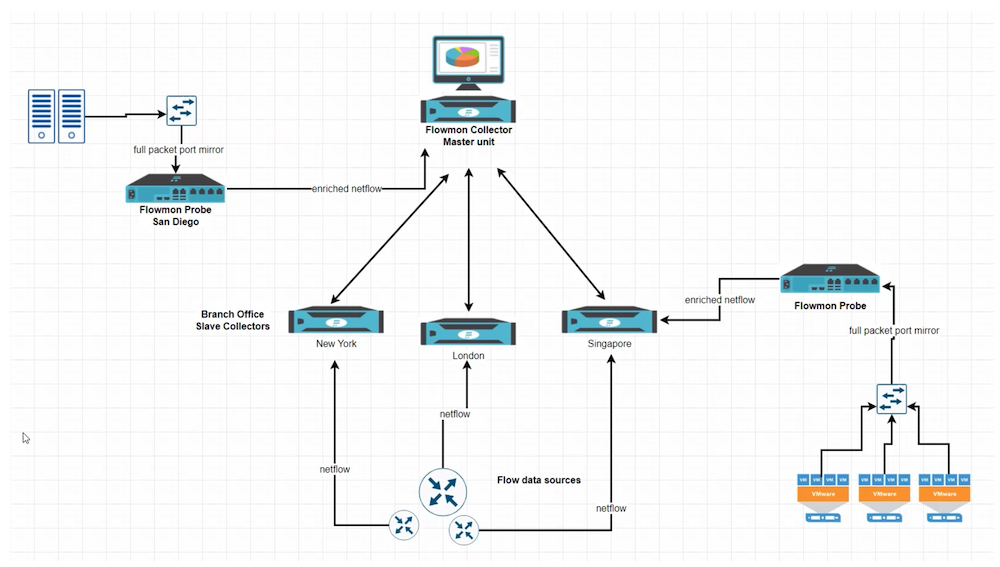
On the other hand, as geography and throughput scales, so does Flowmon, with multiple Collectors and Probes able to share the load:
Data Analysis
The Flowmon Collector is where the flow data is collated and processed, and three modules deliver the network, security and application performance analysis over and above the basic network traffic monitoring:
- Anomaly Detection System (AI-based threat detection and response)
- Application Performance Monitoring (SLA and experience transaction monitoring and correlation)
- Packet Investigator (automated tcpdump and analysis)
I’m choosing to look in a little more depth at the first of these modules – Flowmon ADS.
Flowmon ADS (Anomaly Detection System)
ADS uses behavior-analysis AI rather than static signatures to identify suspicious network behaviors even if a specific threat has not been previously cataloged. But by ingesting the event feed from a signature-based IDS like Suricata, it effectively doubles up on detection capability across the network.
Once an issue has been identified, Flowmon’s NDR (Network Detection and Response) can take proactive steps to protect or neutralize a threat. An example given by Flowmon is that a detected attack could trigger a product like Superna to start a proactive data backup of storage systems and to increase the logging level.
I really like the ability to trigger response actions, which go beyond just blackholing traffic. A traditional IPS (Intrusion Prevention System) mindset would suggest simply blocking the packets, which is a blunt (if effective) mechanism, but only if every suspect flow was successfully identified. NDR on the other hand allows us to trigger an action that may include filtering identified suspicious traffic, but also to take additional actions that could help in recovering if an attack were to be successful, or providing extra information that could help in a post-attack analysis.
Security events are presented to the user in a number of ways, but primarily the idea is to categorize them in a way that makes sense, like MITRE ATTACK™ category, or by priority.
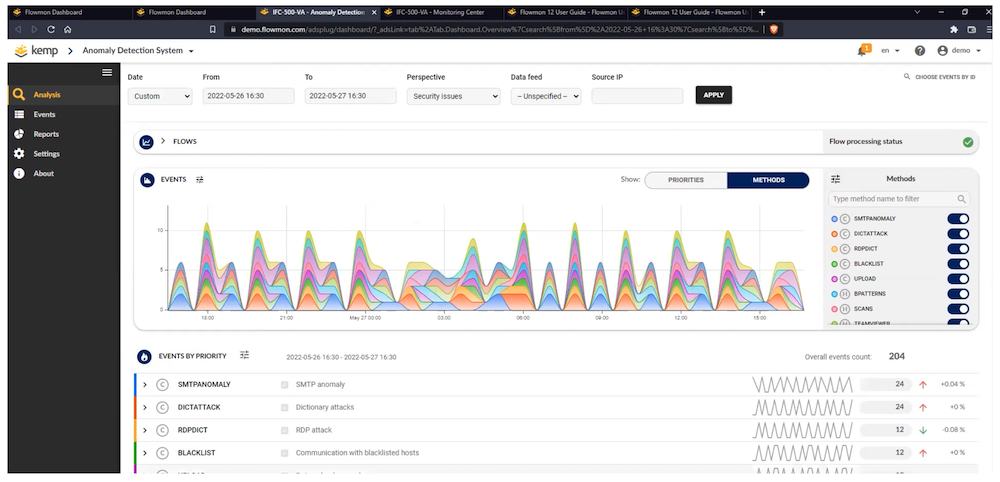
Drilling down into an event shows an explanation of the event, its duration and number of flows involved, and if Flowmon has been connected to authentication servers it will try to identify the logged-in user associated with a suspect source address:
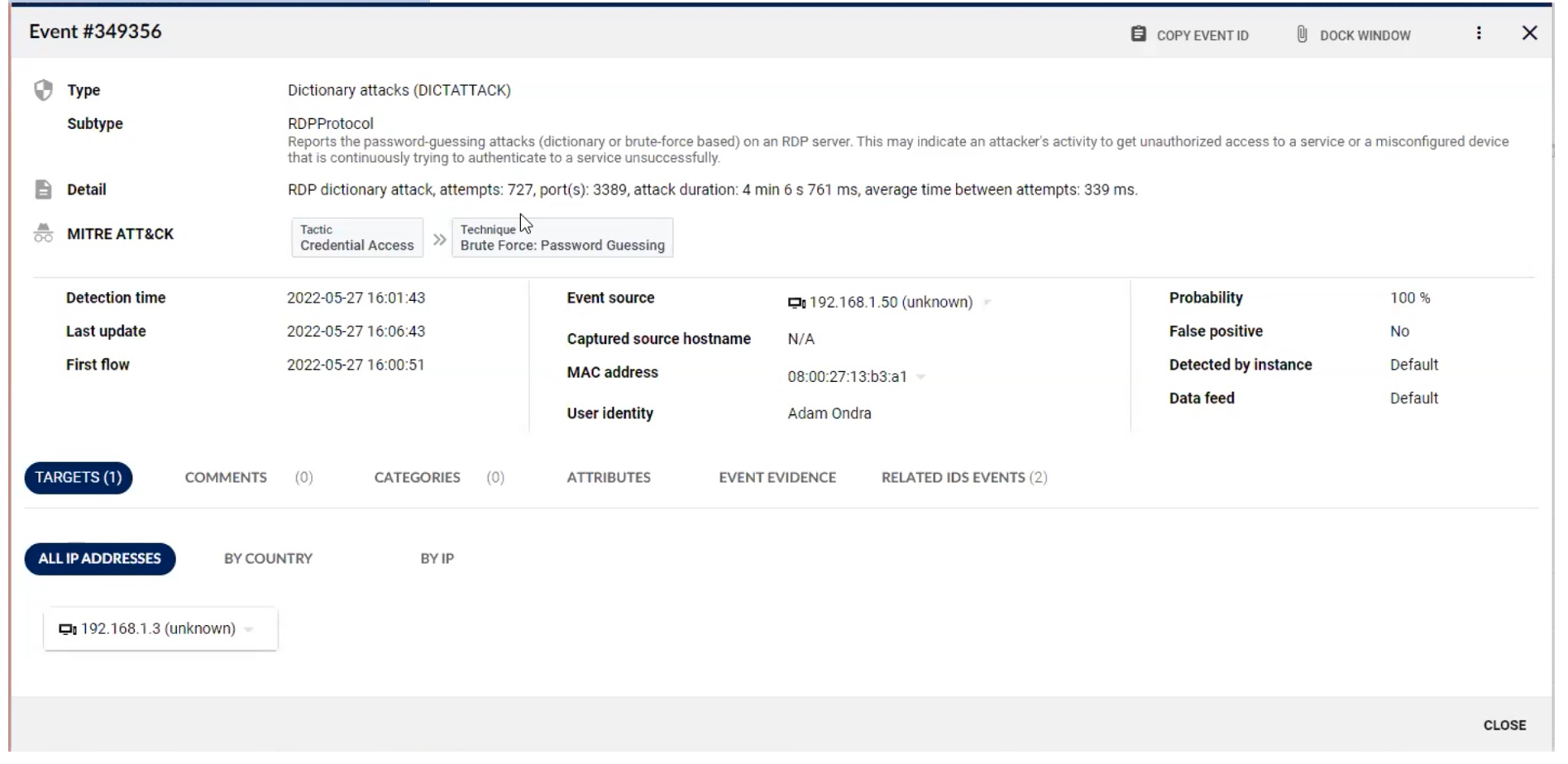
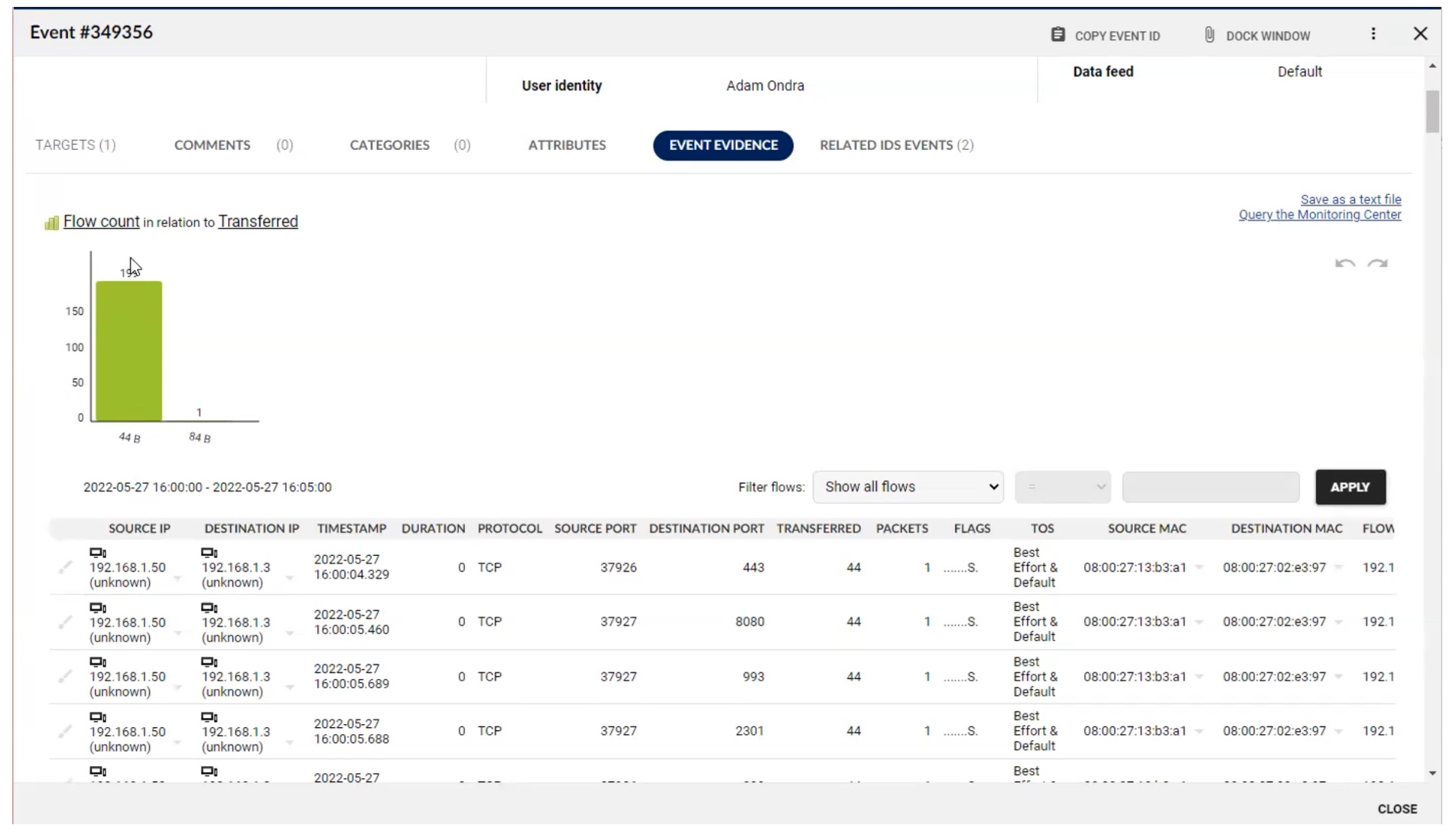
There are multiple tabs containing more information. For example, the flows that are related to this event can be shown:
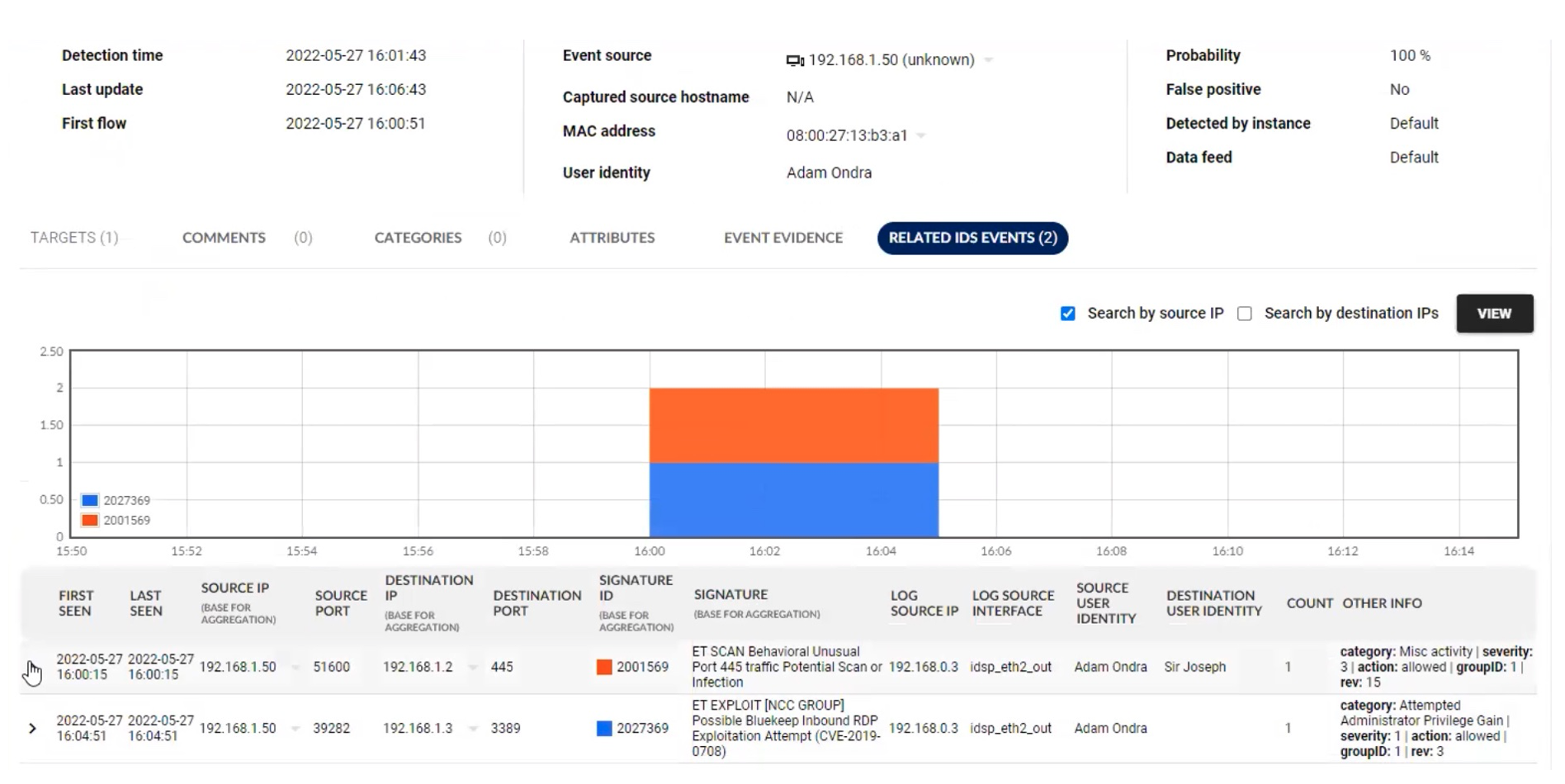
If the event was identified by Suricata IDS as well, that notification is shown within the same event; there is no duplication of Flowmon ADS and Suricata events, and instead this can be used to strengthen the conviction that the event is a true positive:
Flowmon
Flowmon (and in particular Flowmon ADS) has got my attention, and I am impressed. Ideally, I’d want to deploy Flowmon Probes everywhere and feed that enhanced metadata to the Controller, but in reality, I know I’d probably start with a couple of Probes in key locations and use my network devices to provide the rest of the data, then over time I’d want to add more probes simply to take the load off my network devices and gain the enhanced data view.
While I’ve looked at the security aspect of Flowmon, the inclusion of application performance analysis and the ability to remotely gather packet captures in addition to the network data analysis are also exciting features. Having three core monitoring capabilities in a single product is very attractive, and I think Progress is making a strong showing with Flowmon.
For more information on Flowmon by Progress, check out the presentations on the Tech Field Day website or the Gestalt IT Showcase page.

