Issac Newton said it best – “to every action there is always opposed an equal reaction” But what about when there is no reaction? Especially in the cases of emerging threats in the cybersecurity landscape of our industry. For the last few years it’s been no secret that our environments have changed rapidly and with it, the number of threats and attacks that we face. If you think about it, these changes in the industry have always existed but in the recent years they have grown substantially. So how do we remain proactive to these emerging threats? What can we do to ensure that our data remains protected at all times? Let’s dive into how we can eradicate these issues in real time, and also meet with an organization that’s changing the way we protect our data at every level!
Everyone Is Accessing Everything!
Our change of view towards how we view threats and protect our data has been interesting and progressive, to say the least! It started with everyone being interconnected at every level. Everyone accessing everything with any device anytime! Following that, we saw the shift in virtualization which took the industry by storm – consolidating hardware at the data center level and moving to cloud. The belief of some was that if no device is connected to the internet, no threats could come through, so no issues! But that was farthest from the case and because of companies taking no action and not being proactive in these situations, more and more incidents started to occur. But one organization rose to address this demand. That company who knew that security & data were top priorities and treated every incident as if data was top secret. Enter Racktop. Founded by cyber veterans with their roots in national security, RackTop took a highly effective and completely transformative approach to cyberstorge protection utilizing the zero-trust model and remaining at the forefront of today’s constantly growing data-driven attacks that we face. Becoming more educated about ransomware attacks, they’ve managed to leverage these patterns into one phenomenal solution! So how do we take this information and transform it into a more definitive solution moving forward?

BrickStor SP At Its Finest!
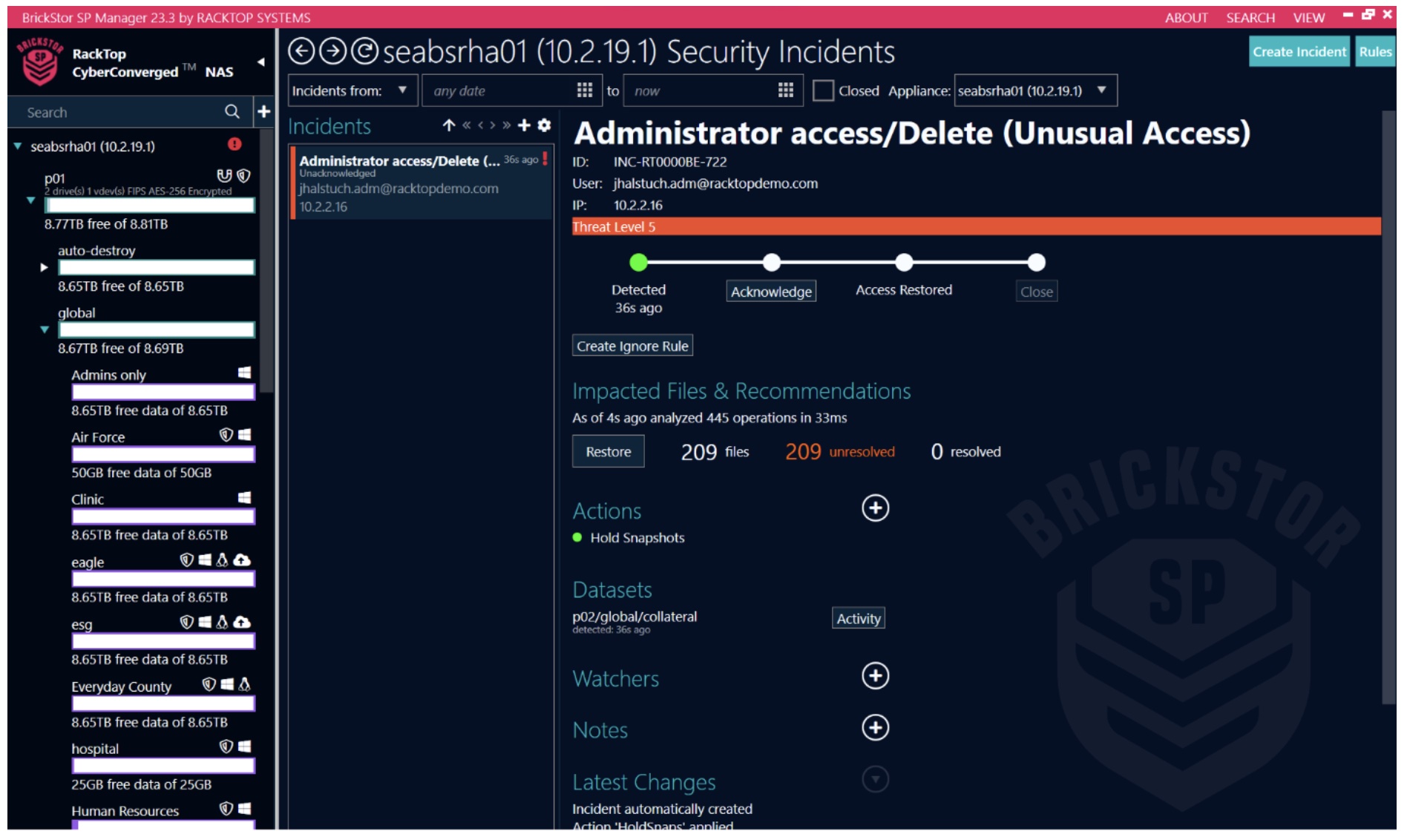
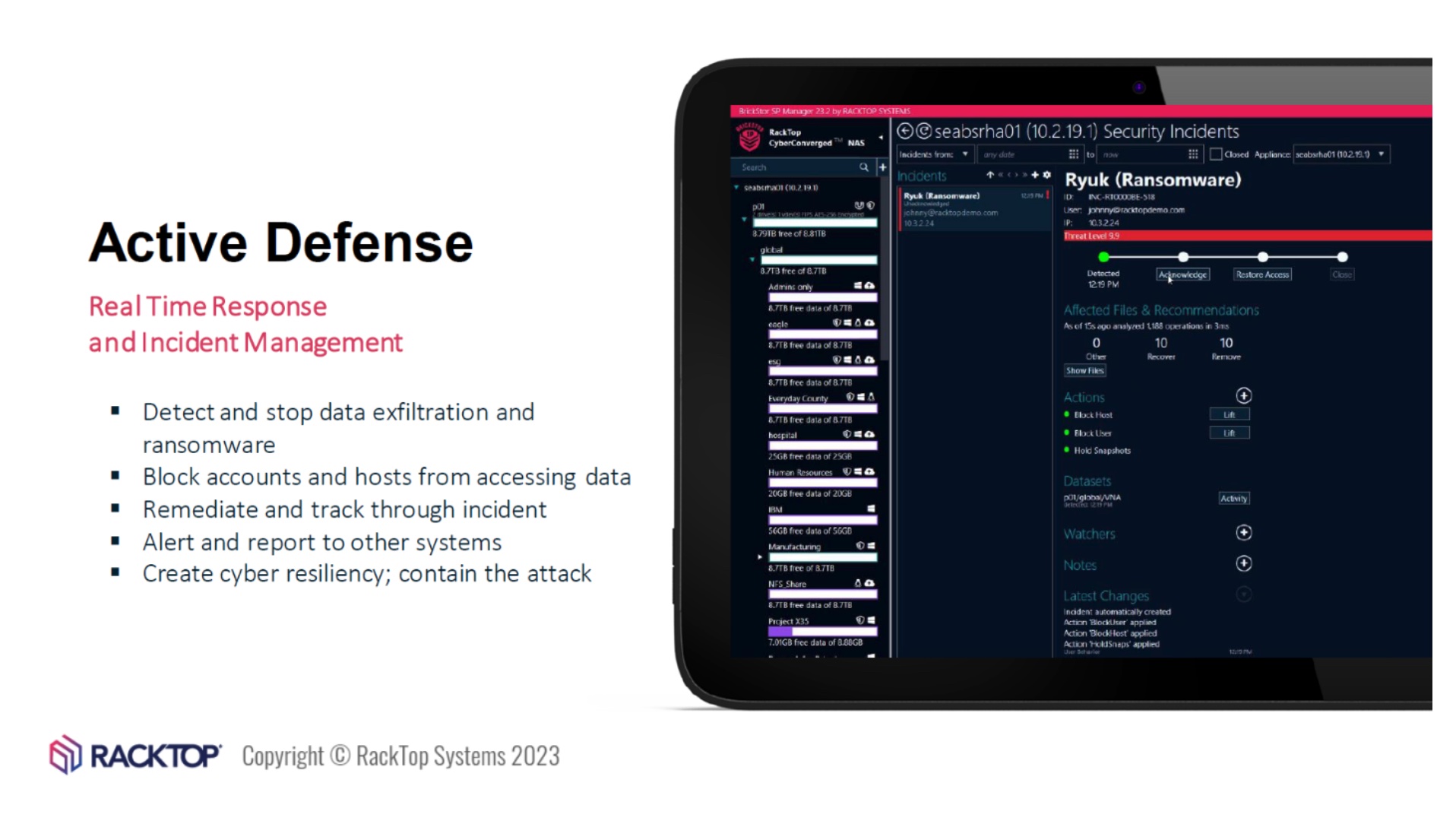
For me solutions and getting to see them in action is like a kid opening that one big gift they can’t wait for on Christmas! I had the honor and privilege to see RackTop’s BrickStor SP solution in action at the Security Field Day 7 event. I’ve maintained that it’s been my favorite solution to see and for good reason. Designed as a software data storage solution coupled with high level advanced security and compliance features, it’s the first of its kind at the data security level and focuses on key areas such as defending against ransomware, insider theft and more. It also has some other phenomenal features such as real time monitoring & detection showing any unusual or suspicious activity, as well as user behavior though auditing and analysis.
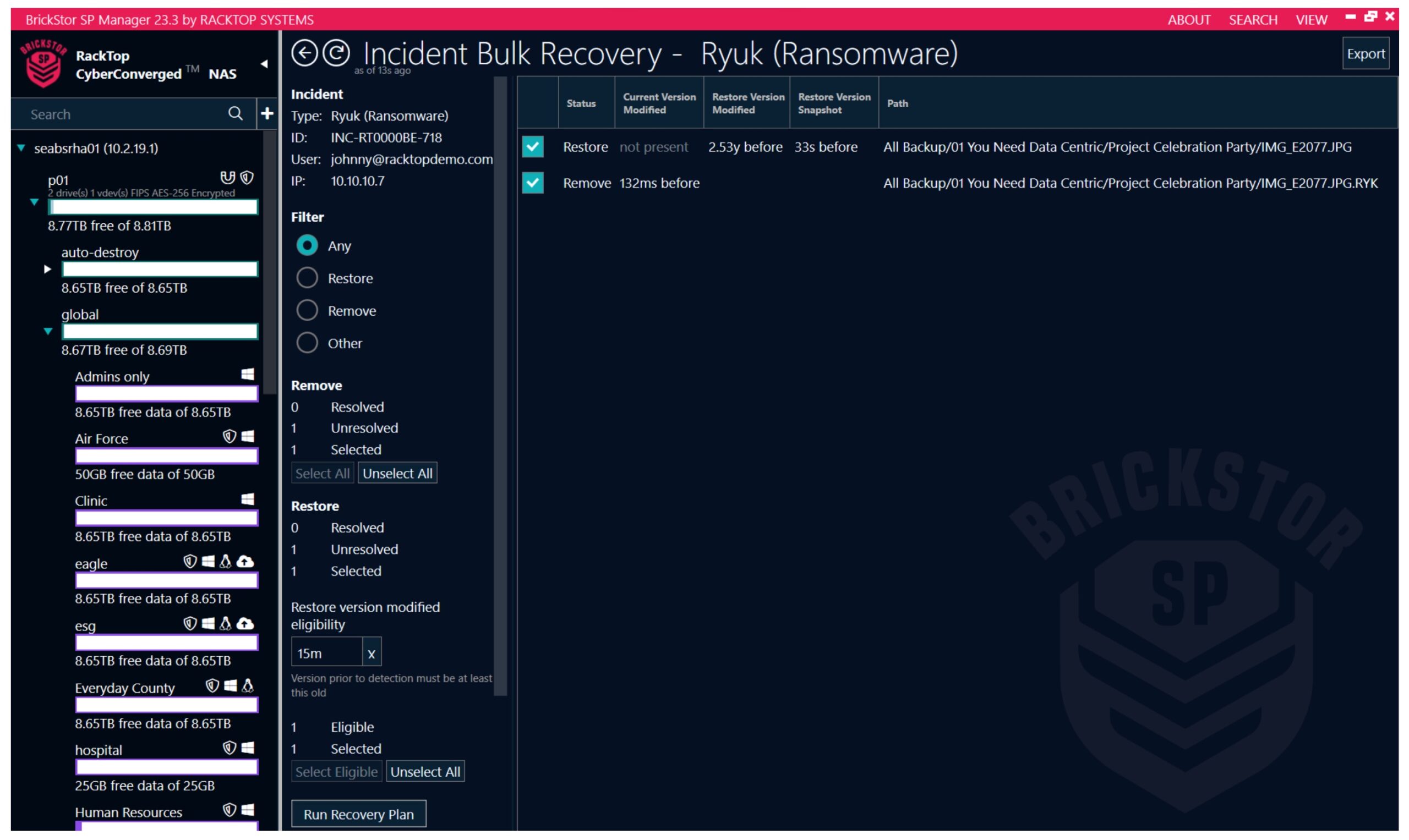
The demonstration I saw not only highlighted what a malicious attack could look like, but it also showed that BrickStor’s intelligent UI shows every detail down to what file, what paths, users and hosts could have been affected and more. Additionally, it also showed where the issue began and where it ended and what was contained and quarantined. If you haven’t checked out the demonstration yet, definitely do so. You won’t be disappointed! So then, the big question- should we continue to sit by and do nothing? What chances are you willing to take with your data and infrastructure?
Doing Nothing Can Be Costly!
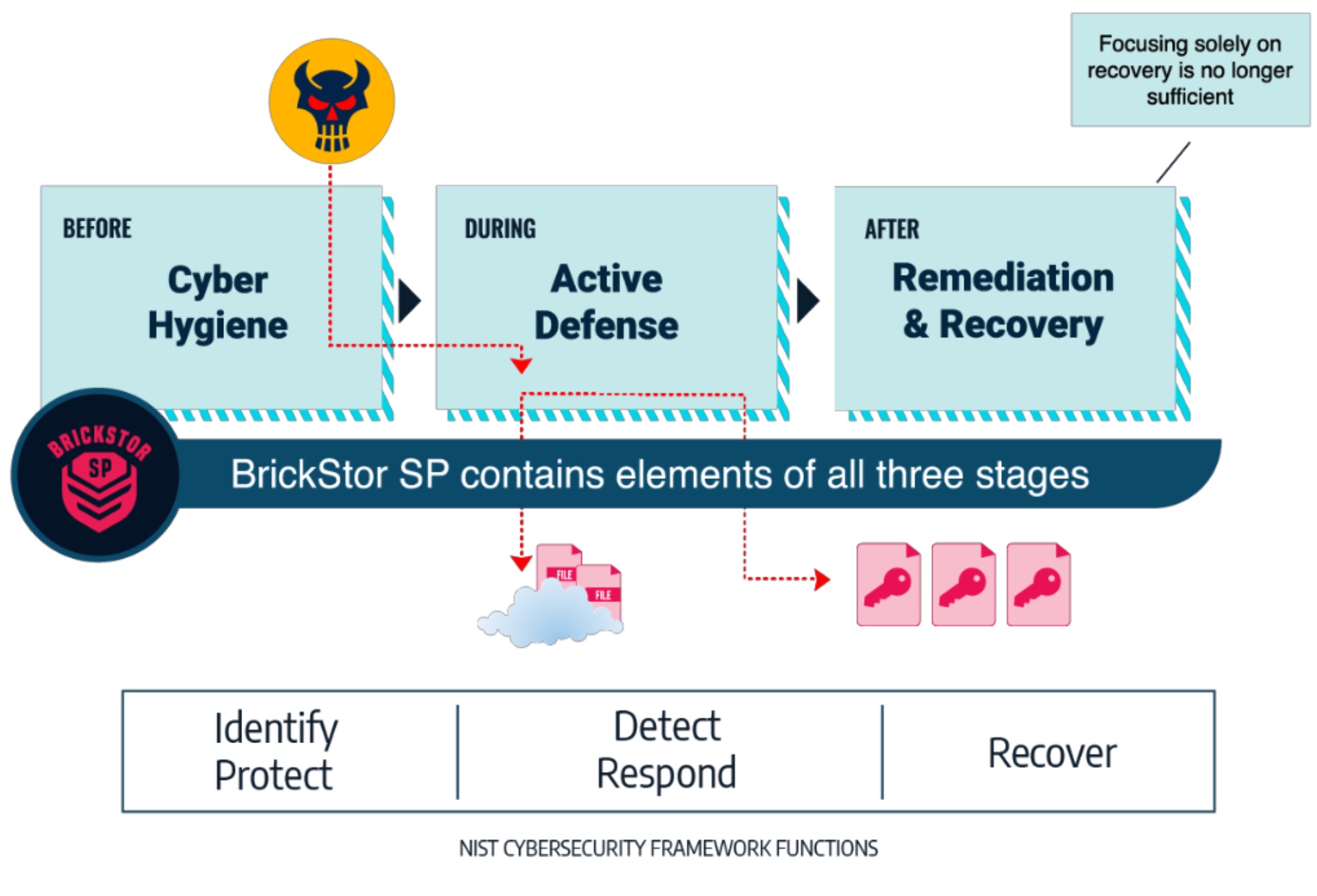
It’s terrifying to think that ransomware has substantially grown and shows no sign of ending anytime soon. What initially started as a 20-billion-dollar problem is now projected to grow into a 250 billion dollar one. For the longest time we thought we could combat these attacks, and even after countless process improvements, best practices, and incidents, there’s still something missing. Implementing EDR solutions, attack plans and more still wasn’t enough, there was one missing piece to this puzzle, and it was this – at the file level, a huge void could be exploited, and threat could come walking in like the Van Halen song. All the solutions in the world cannot address a threat once it enters your environment. RackTop’s protection sits where the data lives, and provides organizations the confidence that they won’t become the next victim to the threat of ransomware.
Analyzing The Threats of Tomorrow!
Whether we realize it or not, we’ve become modern day intelligence analysts, harnessing the power to not only see this data in real time, but also find these processes and events correlating to these attacks, how they happen and how we can properly address them at the file level. There are many ways we can improve our security practices across the board and by utilizing such a powerful tool as BrickStor SP, we can elevate our practices and approaches to not only build further awareness in the Cybersecurity space, but also change the way we combat these never-ending threats. RackTop’s BrickStor has paved the way for a new era in which we protect ourselves and our data. That said, now there’s only one question left – will you come along or take that chance of risking yours? I think we both know the answer to that!