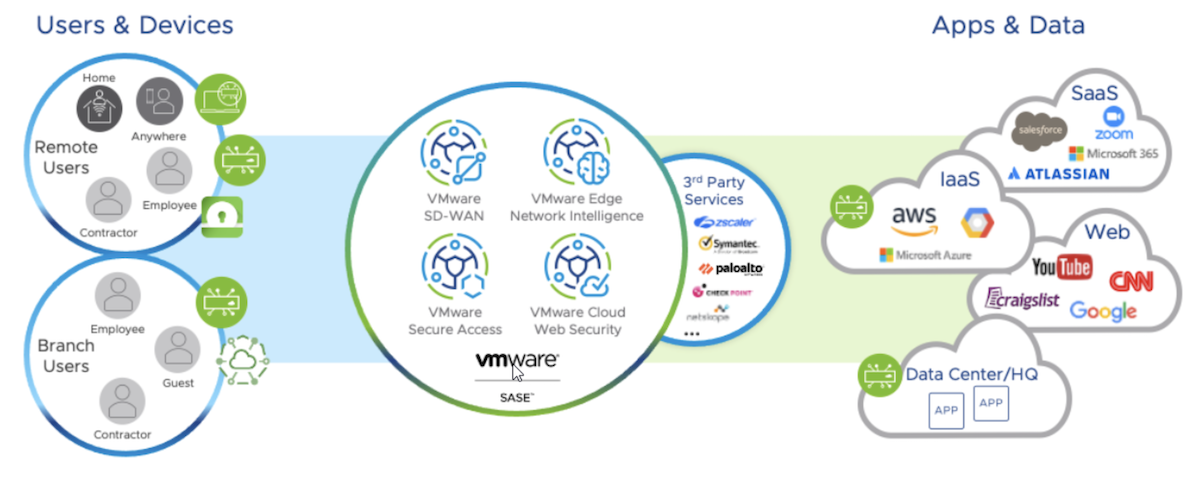
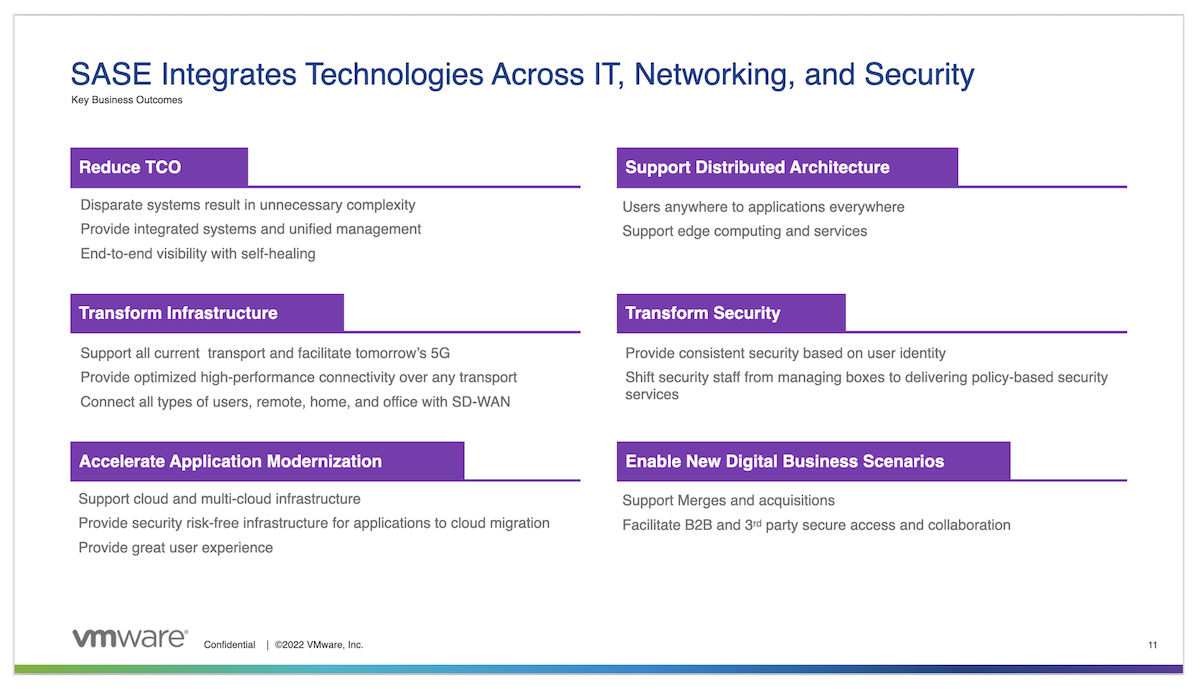
Secure Access Service Edge, better known as SASE brings together networking and security capabilities to better support the technology and business requirements of companies grappling with digital transformation. SASE isn’t a product per se, but an assembly of existing products like SD-WAN, remote access solutions, and security services.
The real value of SASE lies in what it delivers to an organization. SASE provides a more flexible way to secure access to both cloud and on-prem applications, and enables fine-grained security policies that can incorporate user IDs, device state, and device location.
The Two Halves of SASE
According to Gartner, the two main components of a SASE architecture are SD-WAN and a Secure Service Edge (SSE).
SD-WAN provides core networking capabilities, dynamic path selection, and the ability to enforce business and security policies based on applications rather than ports or protocols.
SSE provides security services, which are typically hosted in Points of Presence (PoPs) in various regions around the world. The PoPs may be owned by the SSE provider, or hosted in public clouds or colocation facilities. This hosted aspect is critical to the SSE’s inherent value, that is, customers don’t have to worry about managing the infrastructure, maintaining application stacks, or updating security capabilities or signatures. They simply consume the security features as a service.
The geographic diversity of SSEs is equally important. It means that traffic doesn’t have to be backhauled to a company’s headquarters for security inspection before sending it to its actual destination. Instead, traffic can be directed to the PoP that’s closest to the user, or to the destination application directly. This design reduces the chances of introducing delay and latency, which is critical for the performance of real-time apps like voice and video.
Typical SSE security services include:
- Firewall as a Service (FWaaS)
- Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
Other security services in an SSE may include Zero Trust Network Access (ZTNA), Data Leak/Loss Prevention (DLP) and threat intelligence.
The architectural differences come in how the SD-WAN and SSE components come together. In a converged architecture, the SD-WAN and SSE components come from a single vendor. In an integrated architecture, a customer chooses separate SD-WAN and SSE providers. Each has its benefits and drawbacks. Companies need to understand both to be able to pick the architecture that best suits their requirements.
The Convergence Option
In a converged architecture, the customer selects a single vendor to provide the SD-WAN and SSE components. The benefits of this option are straightforward.
First, the solution should be cleanly integrated because it’s coming from a single vendor. The integration must be tested beyond slideware before signing a contract. There should be fewer GUIs to interact with – dashboards and reporting should be unified – and ideally, the converged system should make performance monitoring and troubleshooting more straightforward. For example, if a user complains about poor performance, customers won’t have to play games with separate SD-WAN and SSE providers pointing fingers at each other.
On the downside, organizations using a converged SASE architecture are limited within the security services from one vendor. These services may not be best of breed.
Additionally, these services may not align with the existing preferences, expertise, and/or processes of your network and security teams. If an organization has invested considerable time and money on a security platform that’s not included in a converged SASE, the teams may balk at being forced to change.
The Integrated Option
In an integrated SASE architecture, an organization has to integrate an SD-WAN solution from one vendor with an SSE offering from another. For example, they could use their existing VMware SD-WAN, and then steer traffic to Zscaler PoPs for security inspection.
This option may appeal to organizations who want more choices for security services in the SSE component. This option may also align well with organizations prefering strict separation of duties: the network team can operate the SD-WAN network while the security team handles a separate SSE component.
This architecture also gives organizations more selection criteria to work with. For instance, two SSE providers might support the same security services, but one has more PoPs in relevant geographies or a more robust network backbone.
On the downside, an integrated architecture is more operationally complex. Administrators may need to stitch together various APIs to get the solutions working. There is be more than one management and reporting console.
The solution may also require more complex routing to steer traffic to separate providers. As a result, ops teams have a harder time monitoring performance and identifying the root cause of problems.
Think Architecture, Not Product
While making a choice, it is important to remember that it is an architectural choice, rather than a plain licensing of product. The architecture one chooses should align with the business outcomes, because it will have a direct impact on network and security operations, application performance, and troubleshooting. Vendors, such as VMware, support both converged and integrated SASE. At all times, customers must read through the fine prints to be certain that the provider/providers offer all requisite capabilities.
To watch VMware’s Showcase video, head to the Tech Field Day Website go to https://sase.vmware.com/sase to learn more about the offering.