Lately, ransomware attacks seem to have gotten out of control. In the last couple years, every major company that you can think of has been hit by one or more attacks. A report published by McKinsey shows that the damages have rose to nearly 300% since 2015. Amid a roaring security crisis, organizations are scrambling to navigate the complex tapestry of modern-day cybersecurity.
At the recent virtual Security Field Day event, Matt Honea, Head of Security and Compliance, at Forward Networks, and colleague, and Technical Product Marketing Manager, Mike Lossmann, explained how a digital twin can serve as the foundation for security.
Weak Visibility Introduces Vulnerabilities
“It’s great that we’re propping up our defenses, it’s bad that the attacks continue to happen, and so we need to think about the macro environments and figure out the threats and trends so that we can react as a security team and mitigate against them,” Honea emphasizes.
Live mapping and monitoring, the typical approach to security does not create opportunities for understanding the network and its connected devices. Nor does it result in a definitive analysis of system behavior every time. Instead, Honea says, being able to observe all the devices provides significant security advantages. For example, knowing what you are up against makes it easier to plan a response.
But when it comes to large and complex networks, engineers falter to achieve that kind of full-fidelity visibility. “A lot of those threats are actually related to human behavior and that’s something that’s always been hard to model historically,” he reminds.
Ransomware attacks are cloak-and-dagger operations that thrive on weak visibility. Hackers preferred targets are these large and complex networks where a lot goes on and a lot of it happens out of sight of the operators. The ever-expanding technology footprints with devices like switches, routers, APs, firewalls, not to mention a prolific number of endpoint devices like IoT systems added to the list, serve as an opportune distraction for them to break in unnoticed.
With vulnerabilities increasing year-on-year, network security has become a difficult problem to solve. “Your employee accidentally exposes a port, and attackers come in with brute force, break in within seconds and install backdoors or crypto miners. A lot of it doesn’t even cause business disruption. Some of it might be throttled, so you may not even know unless you get your bill that month,” says Honea.
The Blueprint of a Strong Security Framework
What constitutes a successful security program, one may wonder. “For small, medium and large businesses, the way to do this, in relation to all the threats that we’re facing, is to have a very strong policy framework and executive support.”
For small companies, security is consistently low-priority, and with their sparing amount of resources, they are nowhere near ready to face the threats. That makes it critical to have a policy in place that provides a fundamental level of protection. “If you have a policy that says we need multi-factor authentication for everyone, that goes a long way with protecting from these types of breaches.”
The second sine qua non, Honea says, is observability and awareness. “Inventories, labels and ownerships in your network are super key to responding to new threats that come up, and old threats that are evolving into new threats. You can’t react to any of that unless you know your software, hardware and network inventory and understand what you have.”
Especially to respond to new threats, the operating team must know the macro environment inside out. Typically, the default way to address a vulnerability is push an update or deploy a patch. But things are rarely that simple anymore. “You might have to add web application firewall rules, or do network isolation, block ports or throttle traffic. There are so many different ways that you might be able to respond and you can’t respond if you don’t know what it is,” he cautions.
Digital Twin Can Transform the Way Enterprises Approach Cybersecurity
The Forward Networks Platform supports building this security program from scratch. For years we have been using satellite navigation systems to navigate the world around us. It has helped us explore new and unknown routes, kept us updated about traffic and transportation in real-time, and given us hands-free assistance on the road.
“Google Maps, and Apple Maps are the digital twins of the road. Why has this never happened in the network space?” asks Lossmann.
So Forward Networks brought to the market a software that can generate a digital twin of any network. “Forwards’ go-to-market was to help network engineers be able to troubleshoot multi-complex networks and use our search features like Google, to find stuff inside of their network,” he says.
The digital twin delivers on that. “We use digital twins every day in our lives. It sits in a map platform on your phone that sends updates in real-time, versus us having to go out and buy a stack of maps to keep the map section inside your car updated,” he remarks.
The platform provides vast amounts of rich network intelligence that serves three vital use cases – network security, multi-cloud and NetOps. “It’s just so hard to find a tool that works across these stacks. Everyone in NetOps has their own tools that they love, so it is in cloud and in network security. You basically pay licenses for 10 users here, 20 users there and 100 users somewhere else. The platform we’ve built essentially unifies this,” told Honea.
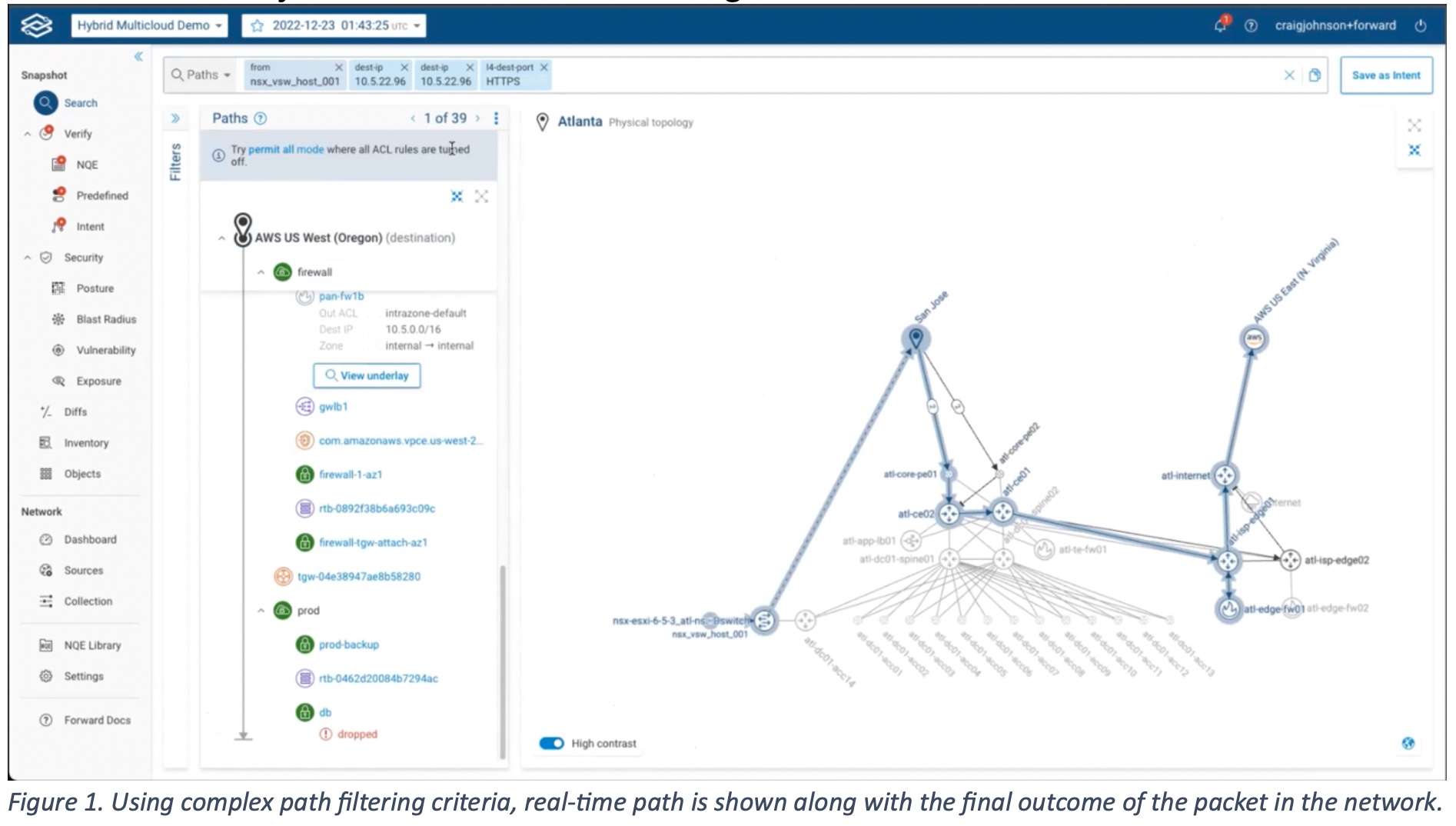
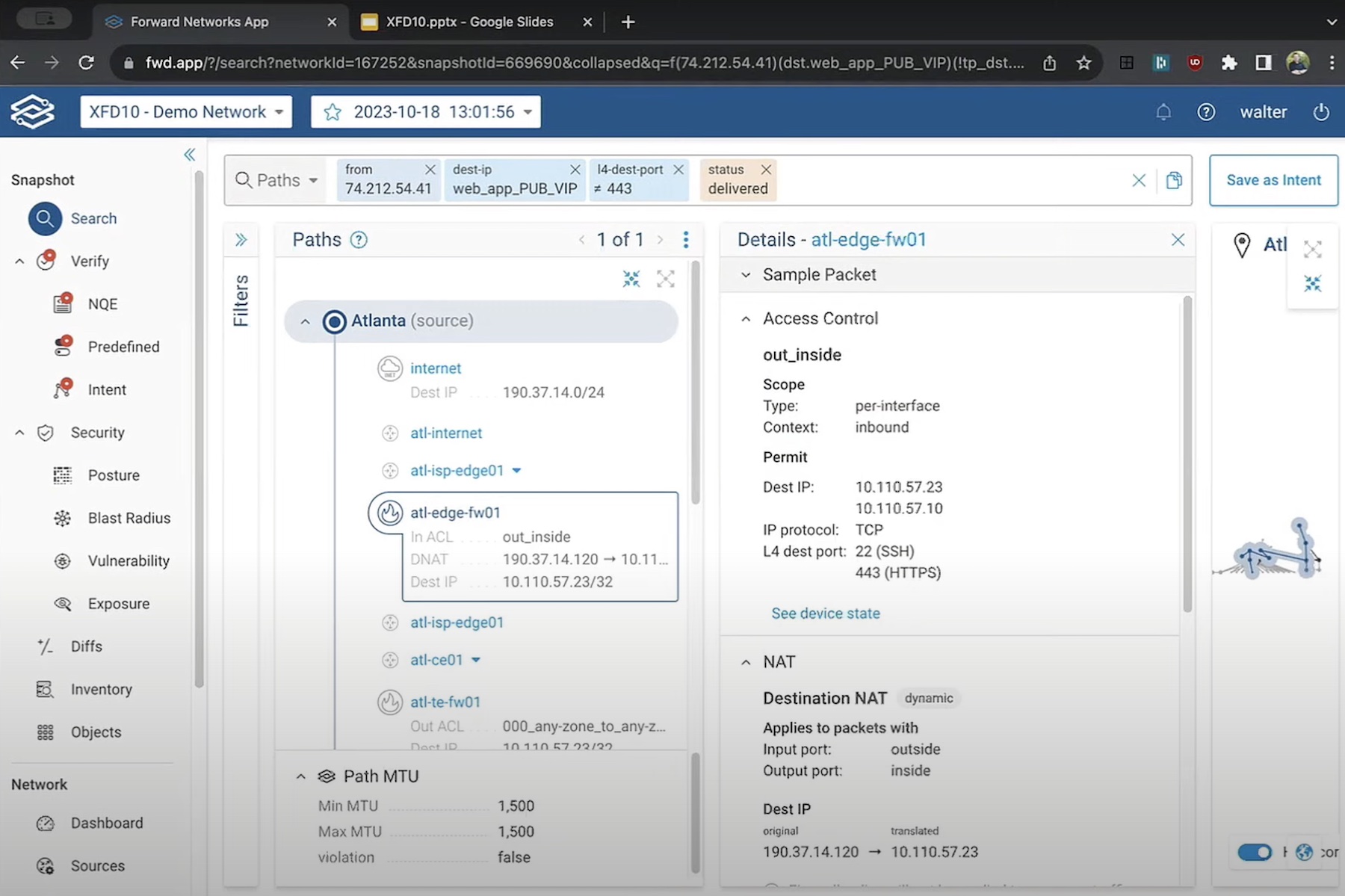
With actionable intelligence on things like incident response, vulnerability management, zero trust security, service assurance, visibility, change control, compliance, inventory management, and so much more, at the fingertips, it is easier for teams to scope out threats and understand the blast radius.
The goal is to build a searchable “network behavior database” that has everything from device state to configuration, flows and more so that teams have visibility of everything, including compromised hosts and devices they connect to. To find specific information, users can query the data easily and find answer to any question.
Wrapping Up
Actionable network data is critical for network behavior analysis and verification, in the security context. Forward Networks’ solution seeks to provide broad and pinpointed visibility of all network assets including the rogue ones and their associated traffic. This provides SecOps an easy button to harvest network data and triage threats proactively. Whether it’s coming from outside the organization or inside the network, knowing in real-time makes all the difference.
For more, check out Forward Networks’ full presentations from the recent Security Field Day event.