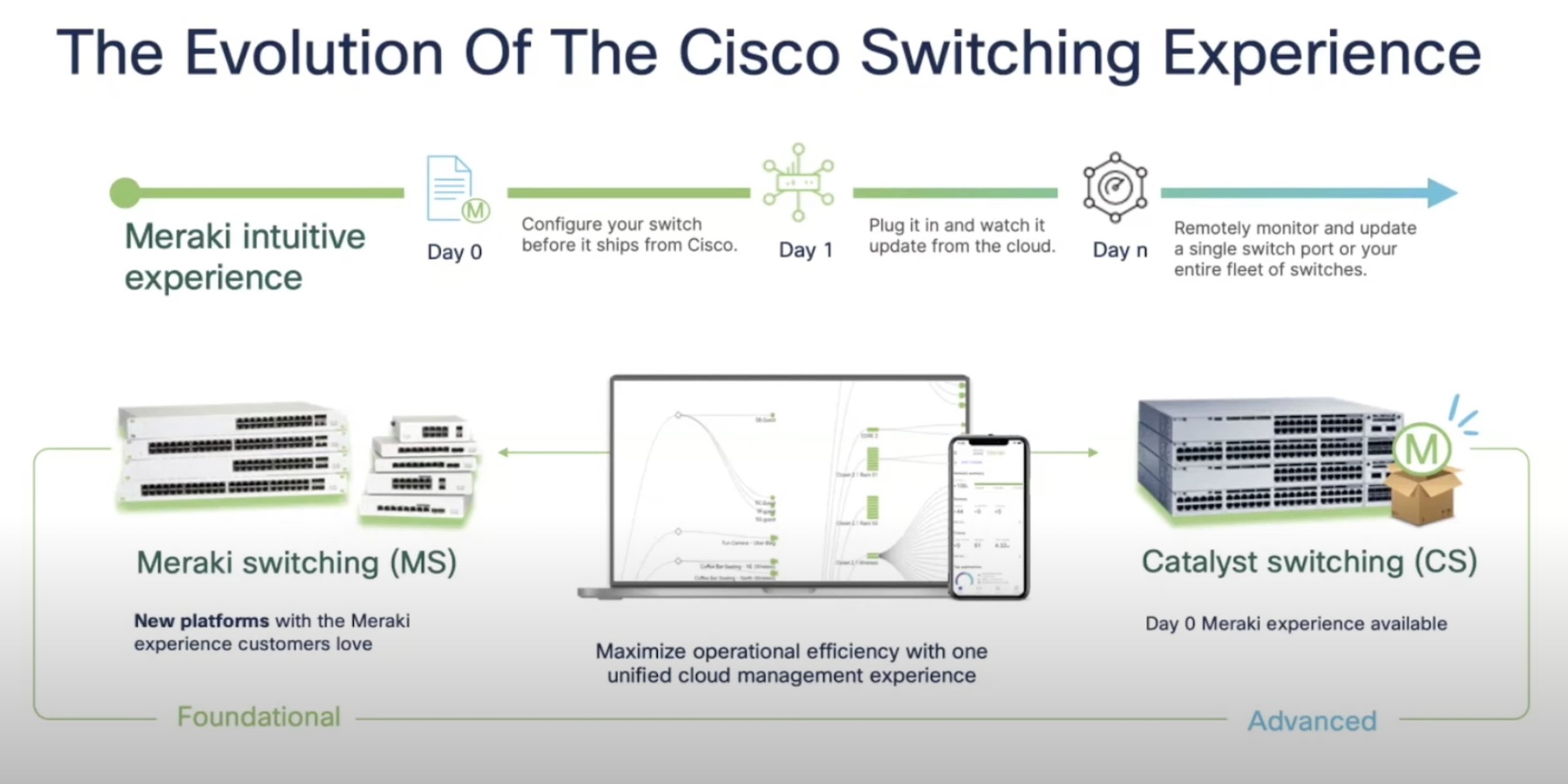
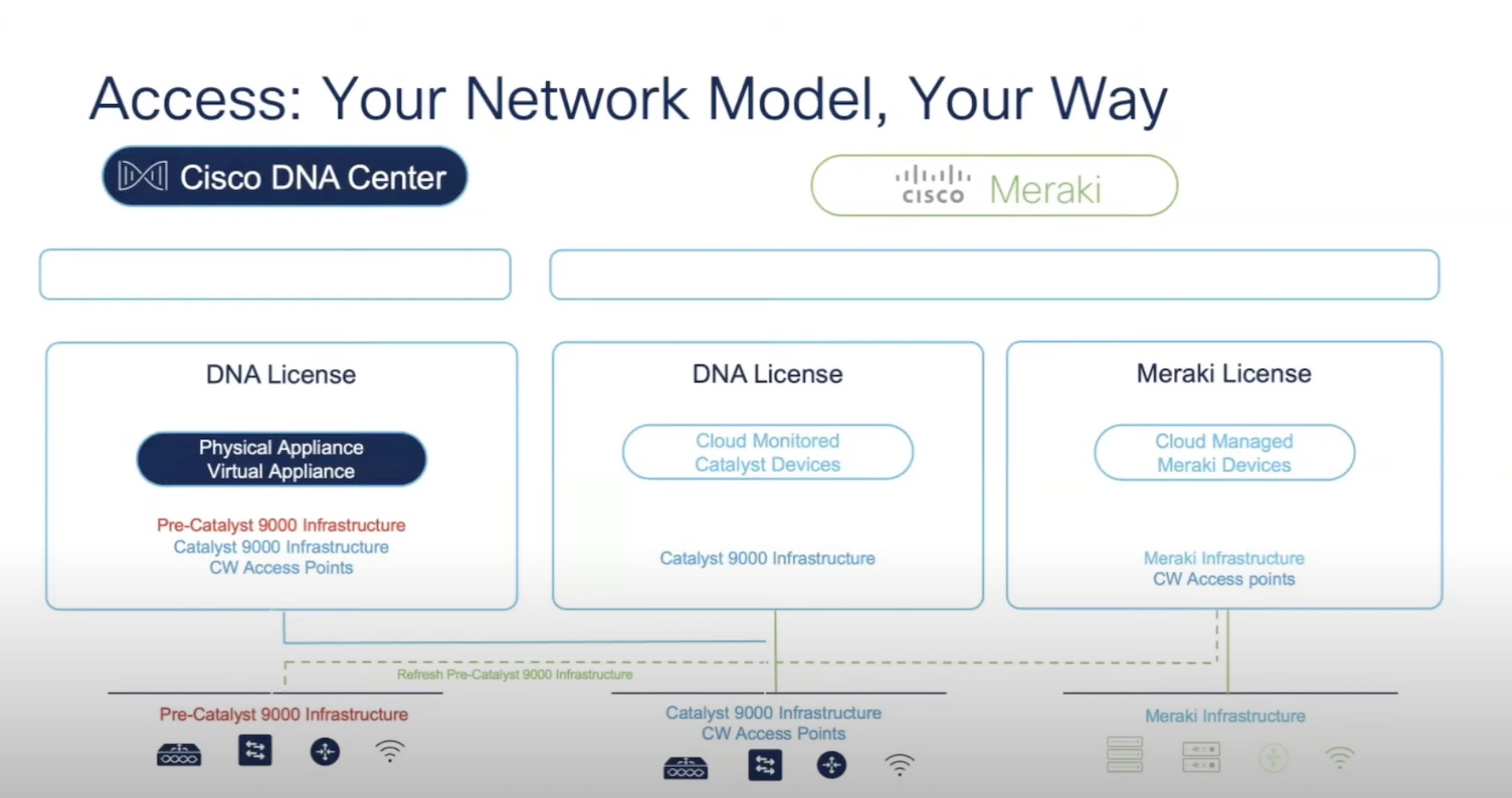
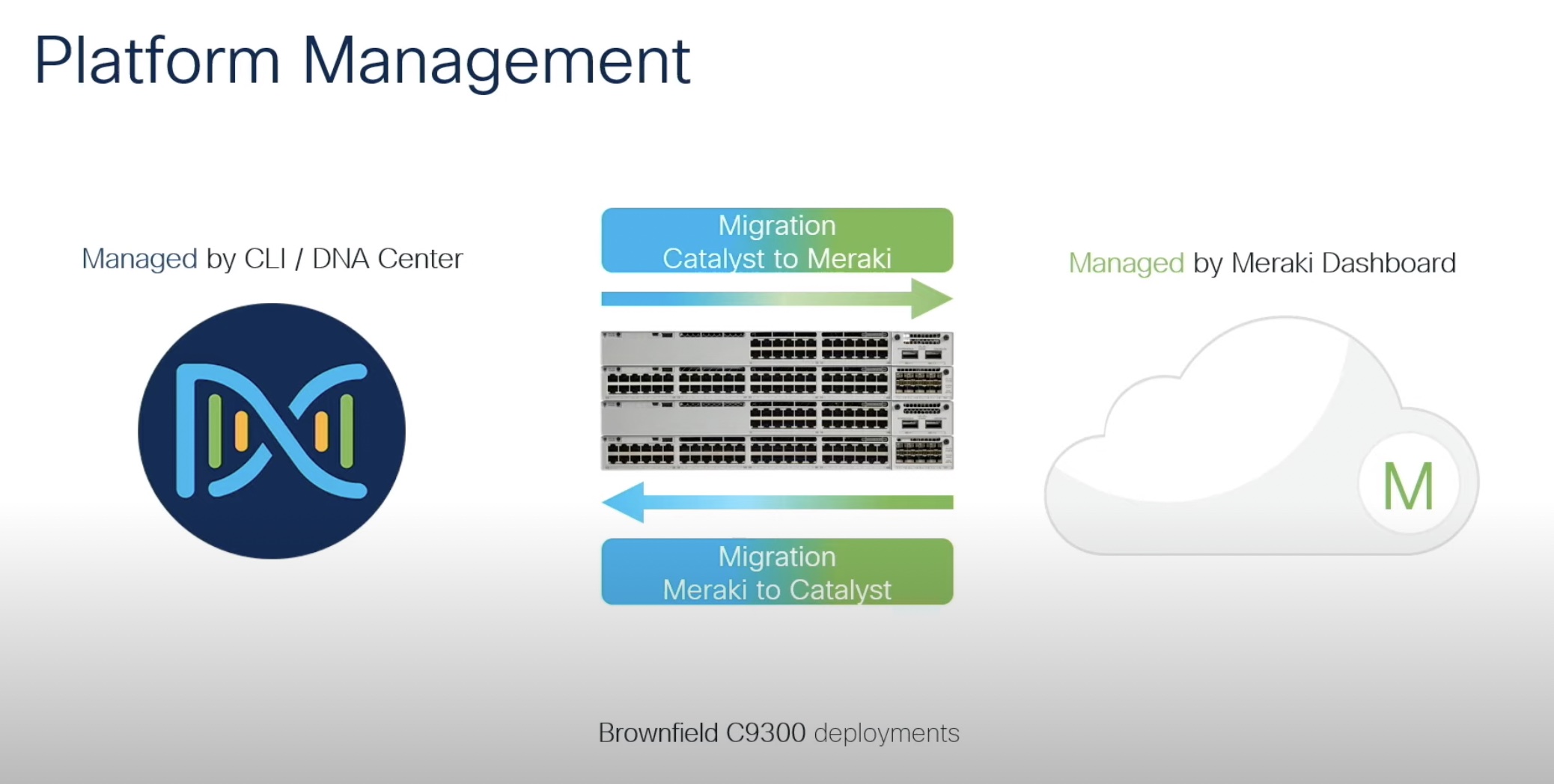
A permanent gap has existed in IT between what teams need today and what they will need down the road. FOMO and an intense pressure to futureproof has led many organizations to accrue more solutions in hopes of closing this gap. But seldom does the journey end favorably for the people involved.
There are several downsides to having too many tools in the box, notably, surging costs and complexity. The situation has left many enterprises grappling with growing technical overheads.
Extending Product Longevity through Continual Evolution
Cisco is one of the few names that have the record of continually evolving their products to fit the changing requirements of users and help control product glut. The company strongly is pushing for networking solutions that are self-driven and holistic, reminding us that a great solution is one that provides value today and tomorrow.
At Tech Field Day Extra at Cisco Live US 2024, presenters, Chris Weber and Chris Pacheco announced and demoed some of the newest updates around the Cisco MX platform, that re-establish the company’s drive for simplicity and resourcefulness.
Autonomous Updates on Meraki MX
The first feature Cisco introduced is firmware-independent autonomous upgrades. Everybody can agree that firewall lifecycle management is a major inconvenience, and that is doubled by the planned downtimes they accompany. Cisco Meraki’s push-button firmware updates make things considerably simpler. But taking it a step further, Cisco is now introducing cloud-delivered firmware updates.
Pacheco explains that the MX platform’s multi-core data plane constitutes several service blocks, namely, routing, QoS, firewall, Meraki SSL Decrypt and Meraki Application Platform. Sitting on top of the last block are two cybersecurity solutions – Snort3, an IDS/IPS system, and ThousandEyes, a user experience monitoring tool.
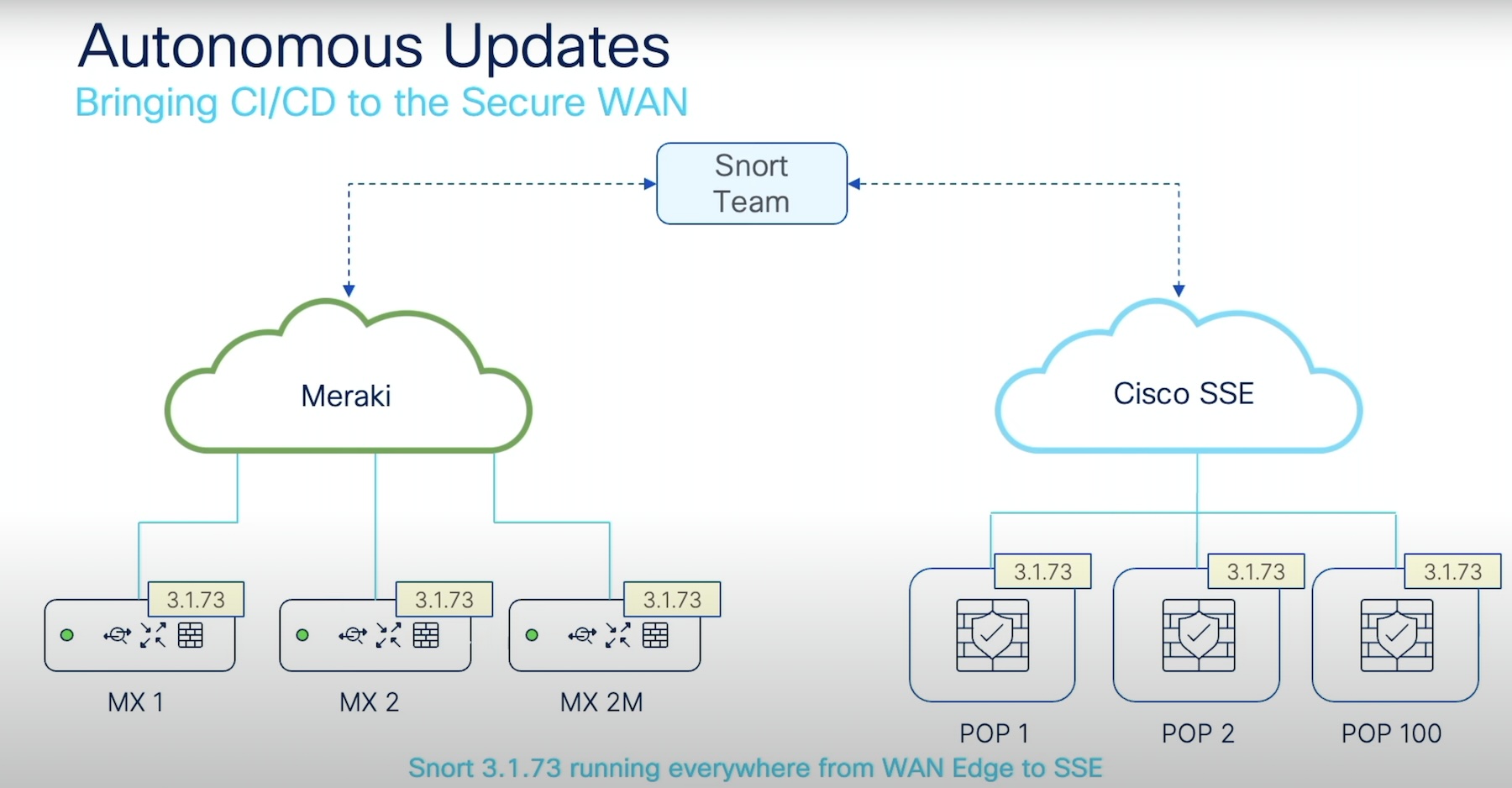
Both the components are outside the data plane. “The reason that they are out there is so that we can update these two containers from the cloud without any need to update firmware. It’s just automatically pushed from our cloud, directly to the devices at the edge,” Pacheco says.
When the Cisco Snort team releases an update, they distribute it across the cloud platforms. Each cloud can consume the updates independently, testing it against their nodes, and eventually upgrading to the next version.
In the last 12 months, Cisco has pushed over 5 firmware upgrades autonomously without involving the customers, Pacheco informs. All of the existing 700,000 MX nodes world-wide can be upgraded to the next version of Snort within 24 hours with this new feature.
MX-OS Gets a Makeover
Next, co-presenter, Weber, gave a walk-through of a new modular architecture for the MX-OS. This architecture spans the entirety of the MX portfolio, and is designed to unify two of Cisco’s decades-old solutions – the Cisco Meraki and the Cisco Vector Packet Processing (VPP).
Cisco VPP is a software data plane known for its fast packet processing. Platforms like Webex leverages it to handle high volumes of packets and data.
“Nothing can forward packets faster than VPP on Intel servers,” says Weber.
Cisco leverages VPP for its SSE/SASE solutions, and with the new architecture, it is debuting the solution for MX firewalls at the edge.
The Meraki data plane, as noted, has blocks of features and components in the service channel along with the Meraki Application Platform. Underneath that, Cisco has introduced a new layer which is the “software ASIC” layer powered by VPP.
This is how the flow path looks in the new model. As the first packet of any flow comes up from the hardware layer, it passes through the VPP before entering the “slow path” where it moves through the different components of the service chain in the Meraki data plane. Security and routing decisions are made at every hop, and the packet is pushed down into the VPP layer. This will allow the rest of the flow to go directly to the VPP bypassing the slow path and arrive at the destination faster.
Two new products leverage this architecture – the vMX-XL for AWS and the MX650. The vMX-XL delivers 10 Gbps of IPSec performance and 10,000 tunnels on a single 8-core instance.
The MX650, a security and SD-WAN appliance, that is a top-of-the-line product in the MX portfolio, also delivers significant performance and protection throughput gains leveraging the new architecture.
“We’ve over doubled the performance on VPN throughput on this platform and we’re getting significant performance improvements on the threat protection throughput as well, all thanks to this architecture design,” Weber informs.
Unifying SOC and NOC with Meraki and XDR Integration
The third feature on the list is the Meraki and XDR integration which creates SNOC, a combination of NOC (Network Operations Center) and SOC (Security Operations Center).
The Meraki dashboard which features ThousandEyes and Umbrella will now include the new XDR. This will allow both security and networking teams to look at all flows from the Meraki Dashboard.
By signing into the XDR account, they can pull XDR incidents into the dashboard. “You can view them, or you can manage them,” Pacheco says.
In the traditional path, packet is received by MX, passed through traffic analysis and other features before getting transmitted to the destination. The integration allows telemetry from MX devices to be imported directly to the XDR by the way of Meraki Cloud, without using a flow collector or sensor.
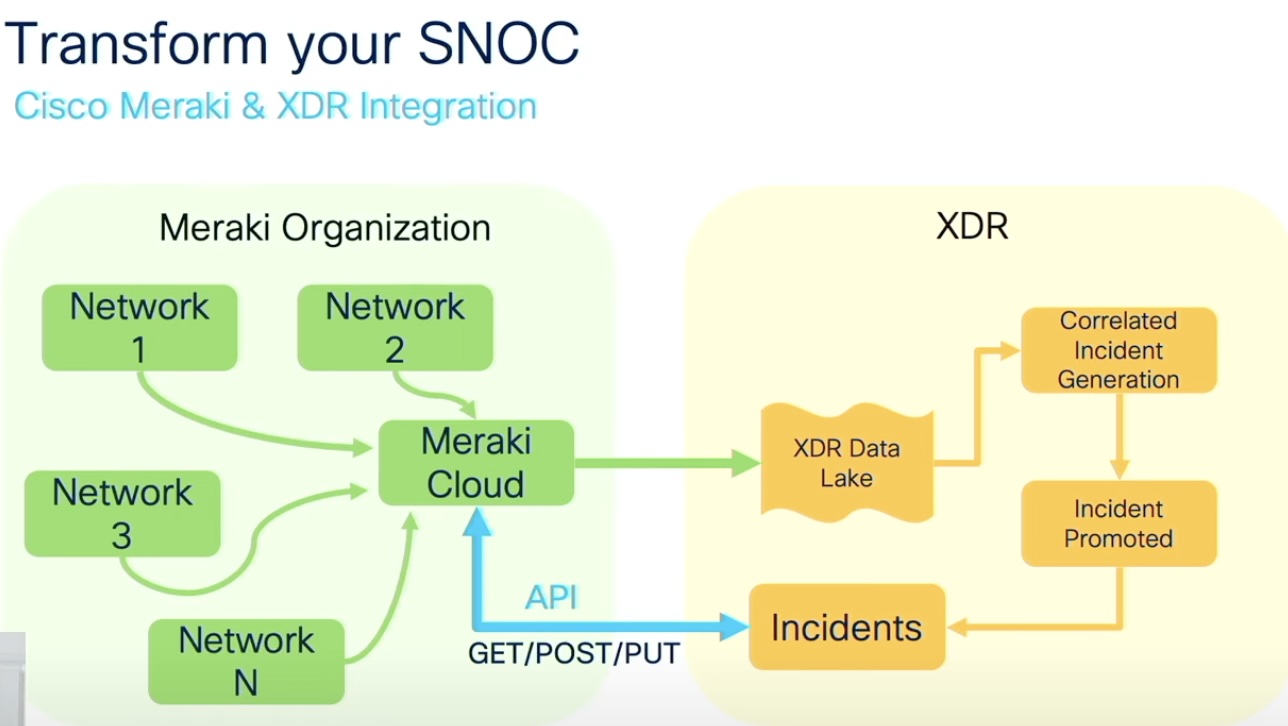
All the networks send their data to the Meraki Cloud from where copies are created and sent over to the XDR data lake. The flow, as it passes through traffic analysis, is captured in the kernel and sent over to the user space. An application in the user space handles TLS and encryption.
It transmits data to the cloud every 60 seconds or less. “I say 60 seconds because if the oldest flow is 60 seconds old, we’ll send it out. But it could happen sooner when you have a lot of flows going through and you can’t send them all in one packet out to XDR. It the buffer is full, or it hit that 60 second mark, we’ll send the traffic out. From the MX, it’s a separate TLS connection going to the Meraki Cloud.”
XDR applies AI/Ml and advanced analytics to crunch through that data and detect malicious behaviors and indicators of compromise (IOC).
Following this, XDR creates an incident page that displays all the threat details.
“We’ll show the incidents in the Meraki dashboard. We’re doing that all via API. We’re not storing any XDR information in the Meraki dashboard. Any of the incidents that you actually see there is being pulled via API.”
As a result, any changes made in the Meraki dashboard gets collected and populated in the XDR incident page.
For more, be sure to check out Cisco’s presentations from the recent Tech Field Day Extra at Cisco Live US 2024 event in Vegas.