The newest wave of malware is targeting processing in the system memory of your servers. How can...
Exclusives
Gestalt IT Exclusives are original long-form posts written by the Gestalt IT team and published here first. Exclusives are highlighted in our weekly Gestalt News email. Sign up today, or follow us on Twitter!
Checking Up on Transactional APIs
If you're curious about the differences between transactional and real-time APIs, look no further...
Tomversations: Episode 9 – Post-Quantum Cryptography
In this episode, we look at the looming future for RSA-based encryption and how the growing power...
Tomversations: Episode 8 – Middlebox Mayhem
Everything on the Internet just runs point-to-point, right? Would you be shocked to learn there are...
Ep. 15: Will Geopolitics Block Nvidia + Arm?
On September 13, Nvidia announced that they had reached an agreement with SoftBank to purchase Arm...
Tomversations: Episode 7 – Security and Risk Aversion
Is your security team really the Department of "No"? Are they the kind of people that never take...
Productionizing ML Models with Proper Data
In recent years, a paradigm shift has occurred. Following a Tecton briefing, Andy Thurai delves...
Tomversations: Episode 6 – The WAN Is Dead
Wide Area Networking isn't what it used to be. The cloud, SD-WAN, and the Internet have conspired...
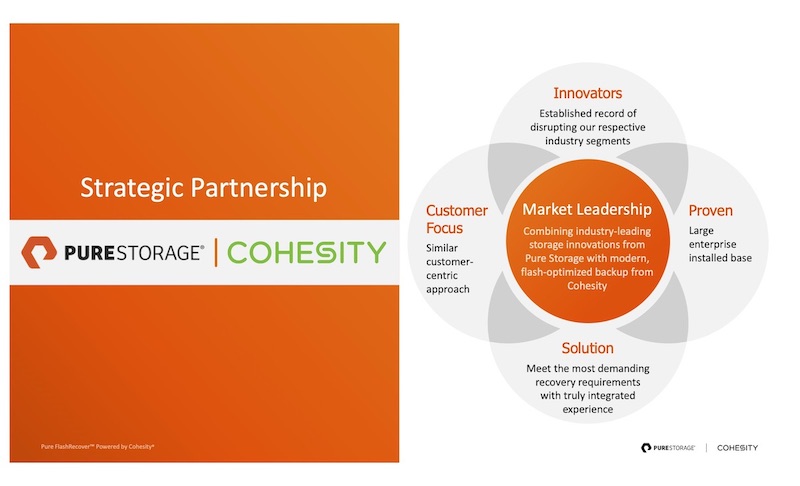
Pure Storage FlashRecover Brings Cohesity to FlashBlade
When Pure Storage promised to deliver an all-flash array to market at a price competitive with disk...
Multi-Cloud Fabric with Arrcus
What can you do when technology enables you to build beyond what you think is capable? What if you...
Tomversations: Episode 5 – End-to-End Encryption
Tomversations is back for Episode 5. Today we're talking about end-to-end encryption and how the U...
Cisco Live Interview with Khalid Raza
Tom Hollingsworth sits down with Khalid Raza, formerly of Viptela, to discuss how the landscape of...
Tomversations: Episode 4 – Edge Computing
In this episode of Tomversations, we focus on the new area of edge computing and talk about the...
Assuring Identity with ForgeRock
Are you the person you say you are? How do you ensure that the people logging into your environment...
Deep Detection with Blue Hexagon
Heuristics aren't enough anymore. We've entered a new era of malware detection that needs constant...