Companies the world over are facing a common threat that we all know as the dreaded ransomware attack. This is especially true for organizations with older technologies in place, such as older operating systems and databases, which either are very behind in their support cycle from the vendor, or just plain out of support as the vendor has effectively killed off the product.
Products like Windows 2003 and Informix come to mind. To this day, many companies run critical components of their infrastructure on these antiquated software packages.
Evolving Techniques
Ransomware isn’t anymore the “spray and pray” approach that it was just a few years ago. The attacks have become very targeted, not just against specific organization, but also with what attackers are looking for within the organization.
For many attacks, attackers specifically look for the companies’ cyber insurance documents as part of the breach. They use these documents to decide how much ransom to ask, and typically that amount is the same as what the insurance covers.
As Jim McGann VP of Business Development & Marketing at Index Engines points out “Ransomware attackers are businesspeople, they just happen to also be really good technologists.”
The Way Back
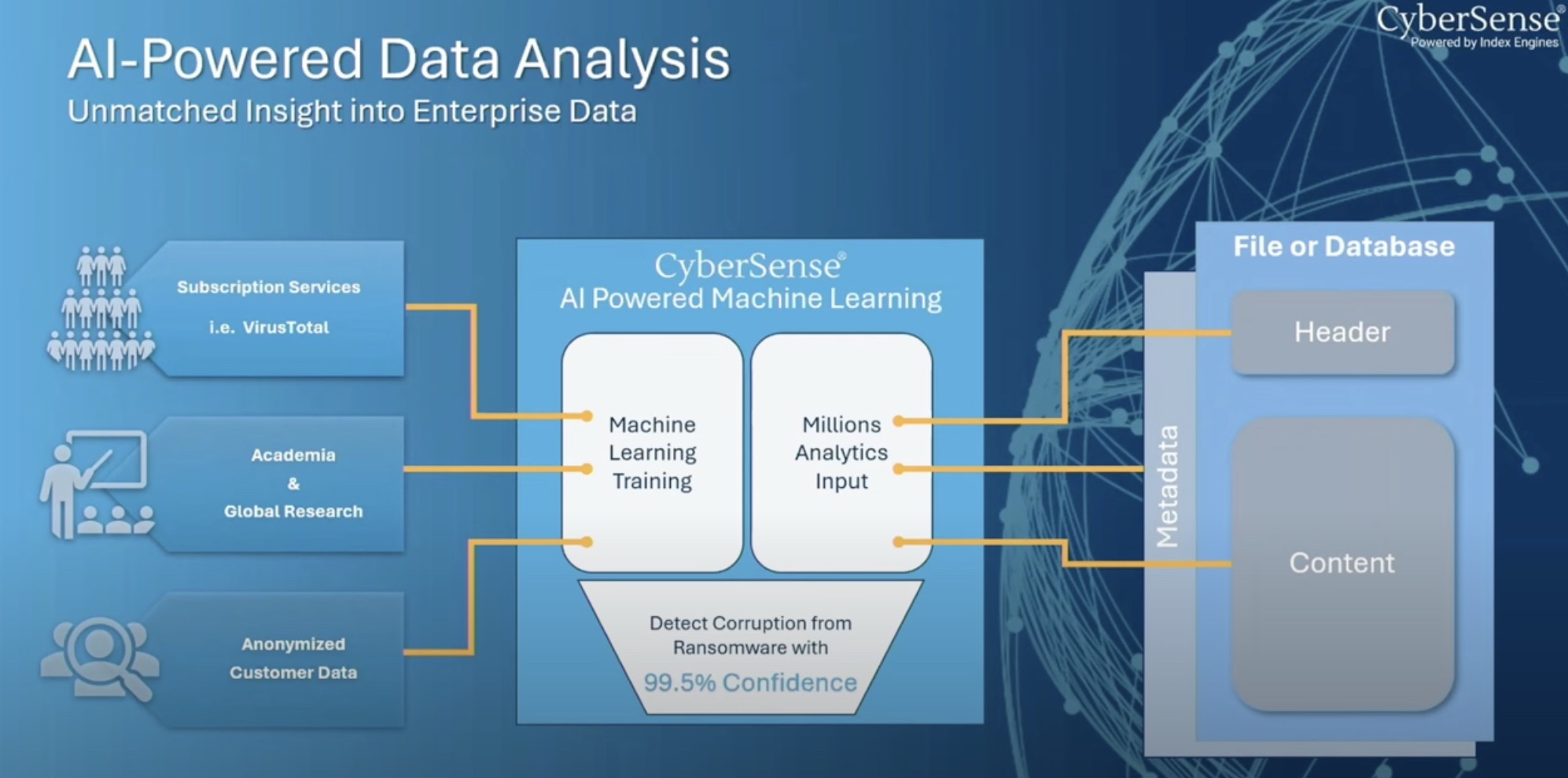
Being able to detect when the files are being encrypted help recover from a ransomware attack. This is one of the ways that Index Engines differentiates itself from other companies in the same market as CyberSense.
In addition to the normal methods of searching for files which are going to encrypt and exfiltrate data -fingerprinting and algorithmic inspecting of files, for example – CyberSense takes the detection a step further by looking not just at the file metadata, but also the data of those files themselves.
Ransomware attackers have varied their techniques over the years to include slow encryption of files, where instead of encrypting as fast as possible, the software will go intentionally slowly in order to avoid detection for as long as possible.
Attackers also encrypt files without increasing the file size. So looking for large numbers of files to have an increased size simply won’t cut it.
Taking stealth to the extreme, some ransomware software read the headers of the files while encrypting These encrypt just some of the files, leaving them able to function within the application which reads them, but rendering the data within, useless.
Index Engines demonstrated one example of this approach with an attack on a SQL Server database file which contains the Stack Overflow sample data (this was all done in a lab, no harm came to StackOverflow). Figure 1 shows a database file which is 1.728 GB in size, and the meta-data of the file, that is an SQL Server database file.
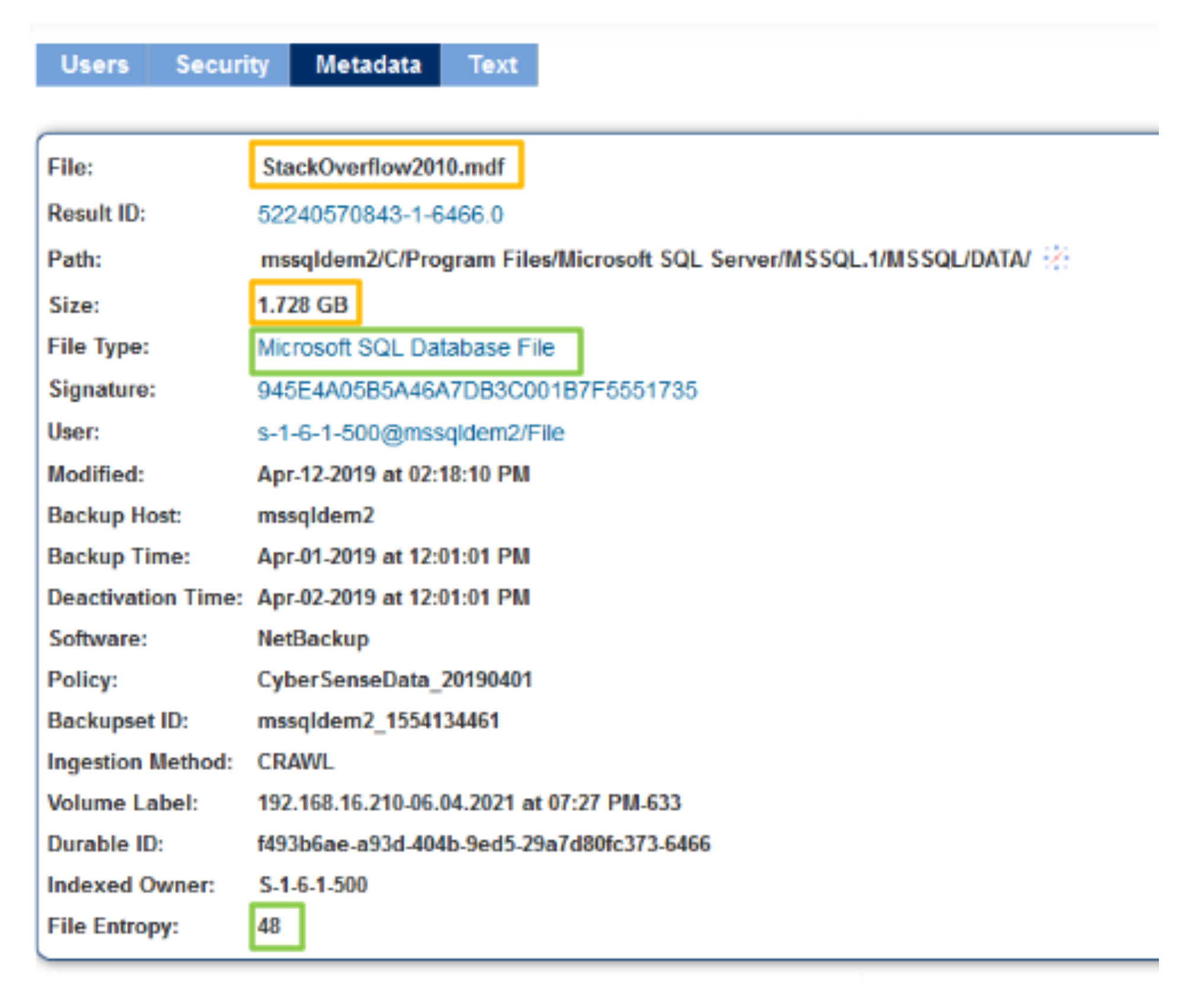
Figure 1: SQL Server Database file pre-attack
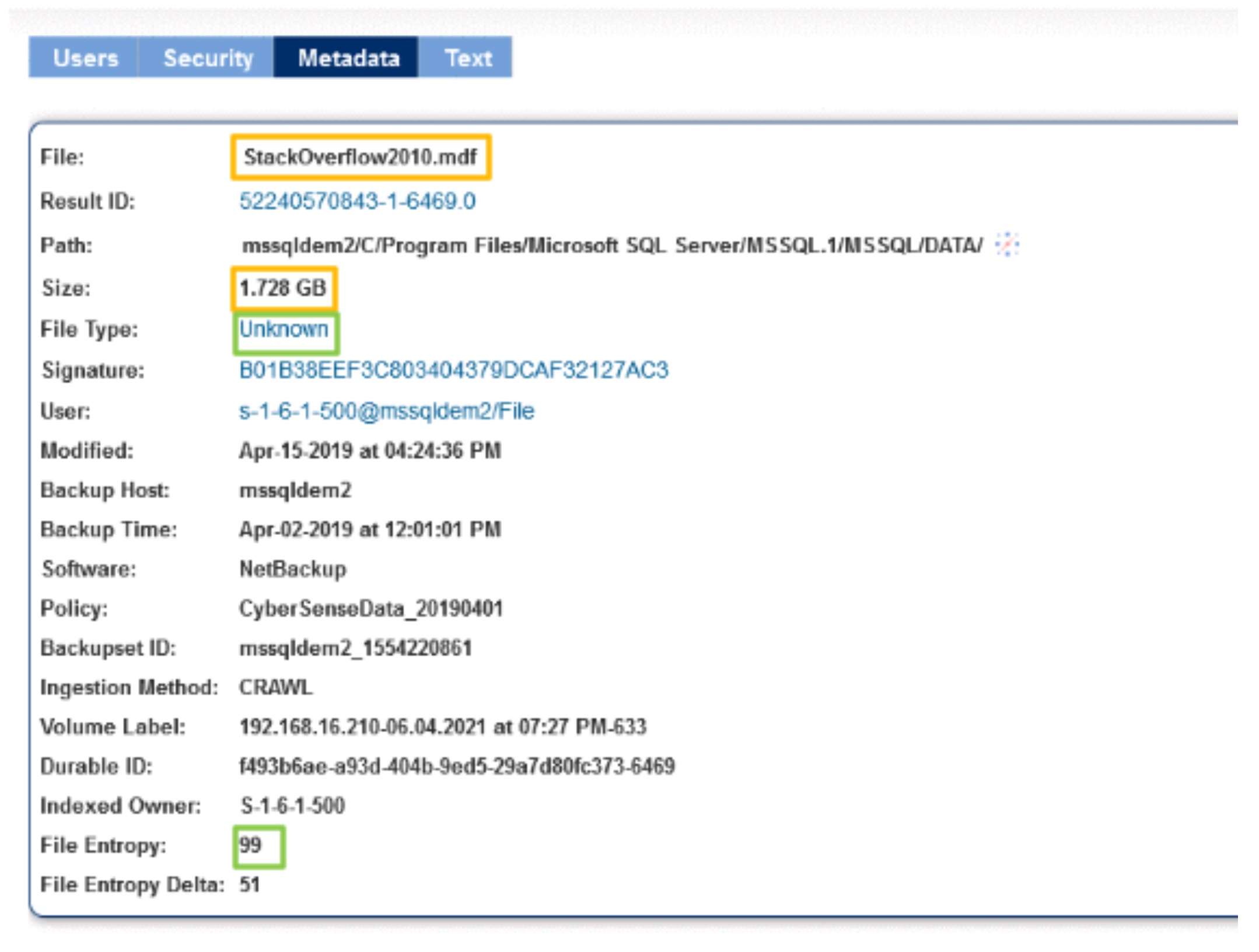
After the ransomware attack is completed, in Figure 2 the file stays the same. But the file type is now listed as unknown even through the filename hasn’t been changed. This is because the CyberSense software is looking at the contents of the data rather than just the file extension.
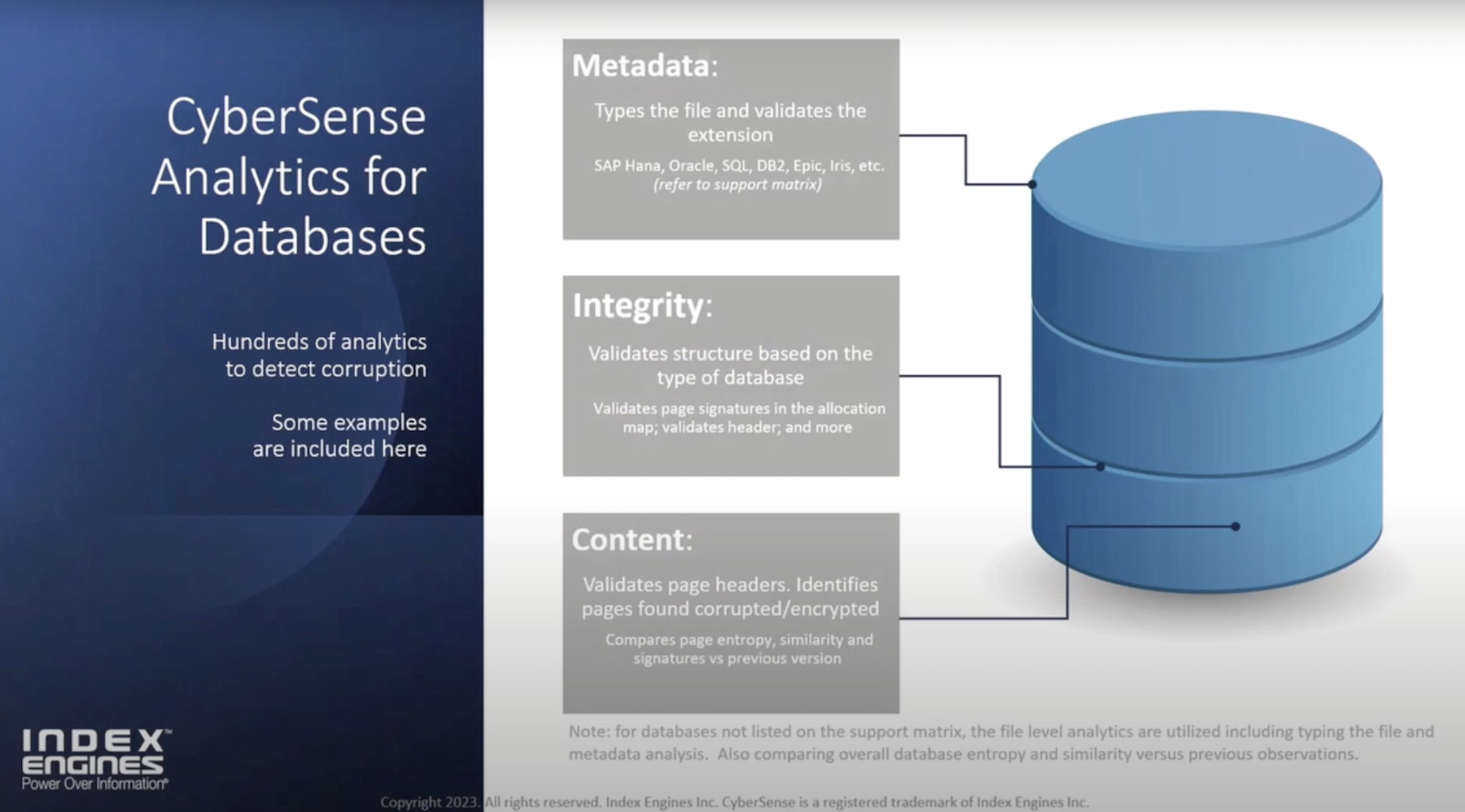
With CyberSense both older and more modern platforms can be scanned, validated, and counted as safe from ransomware. CyberSense mounts snapshot backups or tape backups of company servers to a set of servers running the CyberSense software.
The CyberSense software then scans through the backups looking for files that are infected with ransomware. This includes both files which are infected themselves, as well as files which are ransomware payloads, just waiting to be executed to infect the files within the organization.
In the figure above, there is also a change in the file entropy. Before the attack, the file had an entropy score of 48, whereas in the post-attack scan, the entropy score for the file is 99, which is a delta of 51 since the last scan.
With the massive change in entropy, the CyberSense software is able to make the conclusion that this file is more than likely encrypted, and will alert the administrators.
Conclusion
Any company that is worried about ransomware – which they should be – should regularly scan their enterprise for ransomware. CyberSense by Index Engines can do that scanning for them, detecting all signs of corruption before a full-scale attack unfolds.
For a deep-dive, check out Index Engines’ presentations of CyberSense at this recent Storage Field Day event.