From spammy email links to rogue software gone wild, a company faces many cyber threats. Although not all threats are high-profile, companies must keep their guard up against the most vicious to the lesser-known variants out there, because as far as data and privacy are concerned, any bug or bot can cause serious damage.
At the recent Storage Field Day event, we had a company among us that is on a mission to enable organizations to look out for perils in the digital wilderness, and not get caught out. Index Engines presented CyberSense, an AI-powered security solution that serves as organizations’ “last line of defense”.
Fighting Data Corruption
Experts categorize data corruption in three levels. The basic kinds are corruption by appending certain file extensions to metadata, or making large changes to file size, both of which are pretty easy to spot. The advanced sneakier kinds corrupt file structures and use valid extensions for disguise. The third and the deepest level of corruption is where a malicious program hides inside the content, dwelling in the environment for months on end. This is the kind that is raging around the cyber scene.
Studies show that at the moment, the levels of corruption are the worst they have ever been. It is made worse by low reliability of tools. Ensuring data integrity in a fast-paced hyperconnected time takes inspecting every single datapoint – IP, passwords, files, databases, what have you – round the clock.
Few tools cover that many grounds. Most solutions scope out core files and data, and roll out a disproportionate number of alerts with high false positives which amount to a weak oversight at best. In the scramble, thousands of dollars are lost, and the level of corruption remains steady at an eye-watering level.
CyberSense Looks at Everything
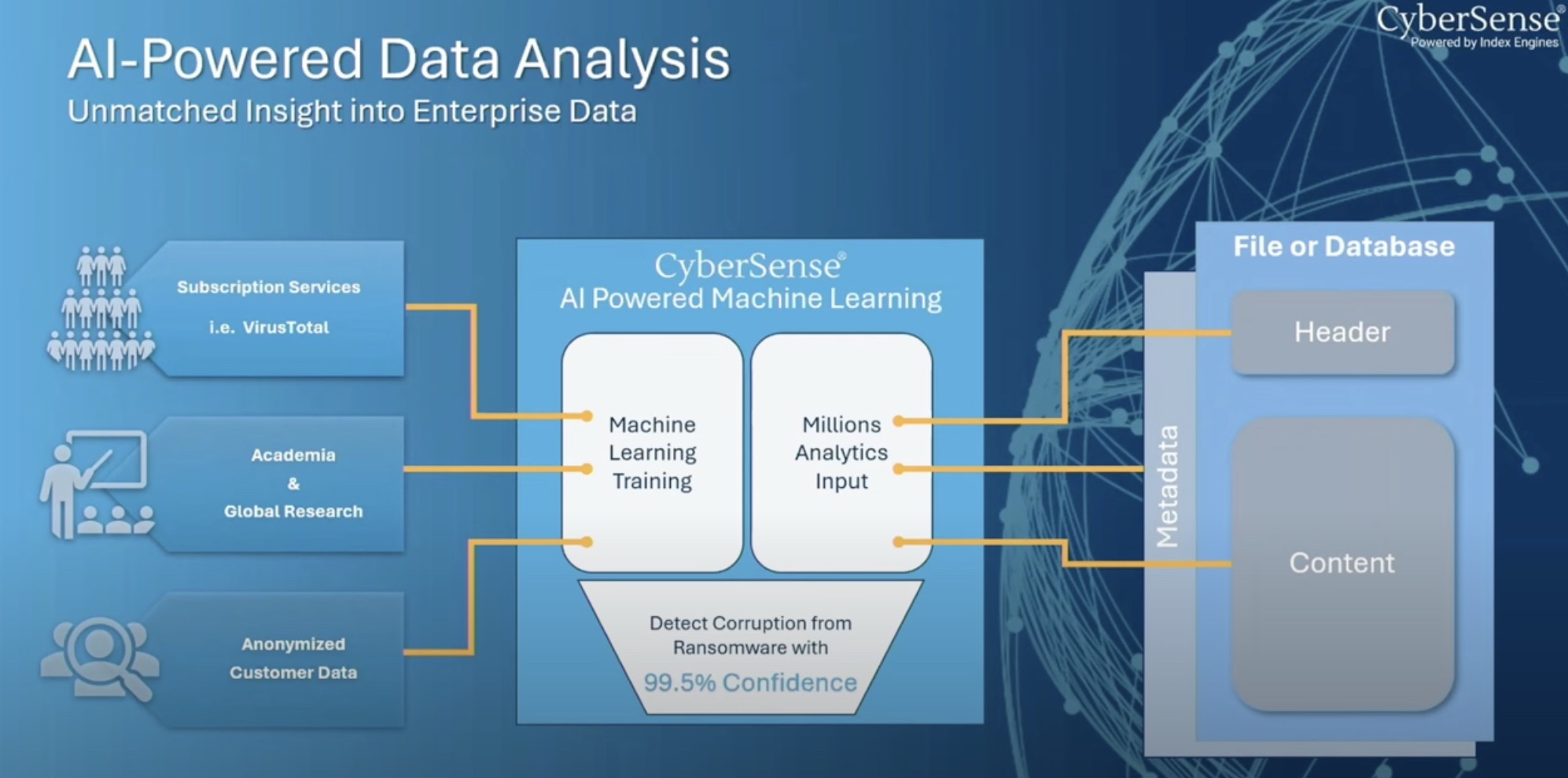
Index Engines seeks to change this reality with a solution based on full-content analytics. It’s strength – data observation and analytics. CyberSense detects advanced variants that hide their tracks with highest accuracy, and provides a high level of confidence.
Jim McGann, VP of Marketing and Business Development at Index Engines explained, “We layer on top of different applications. We’re not backup, we’re not storage. We’re just software that sits on these environments and adds a layer of intelligence.”
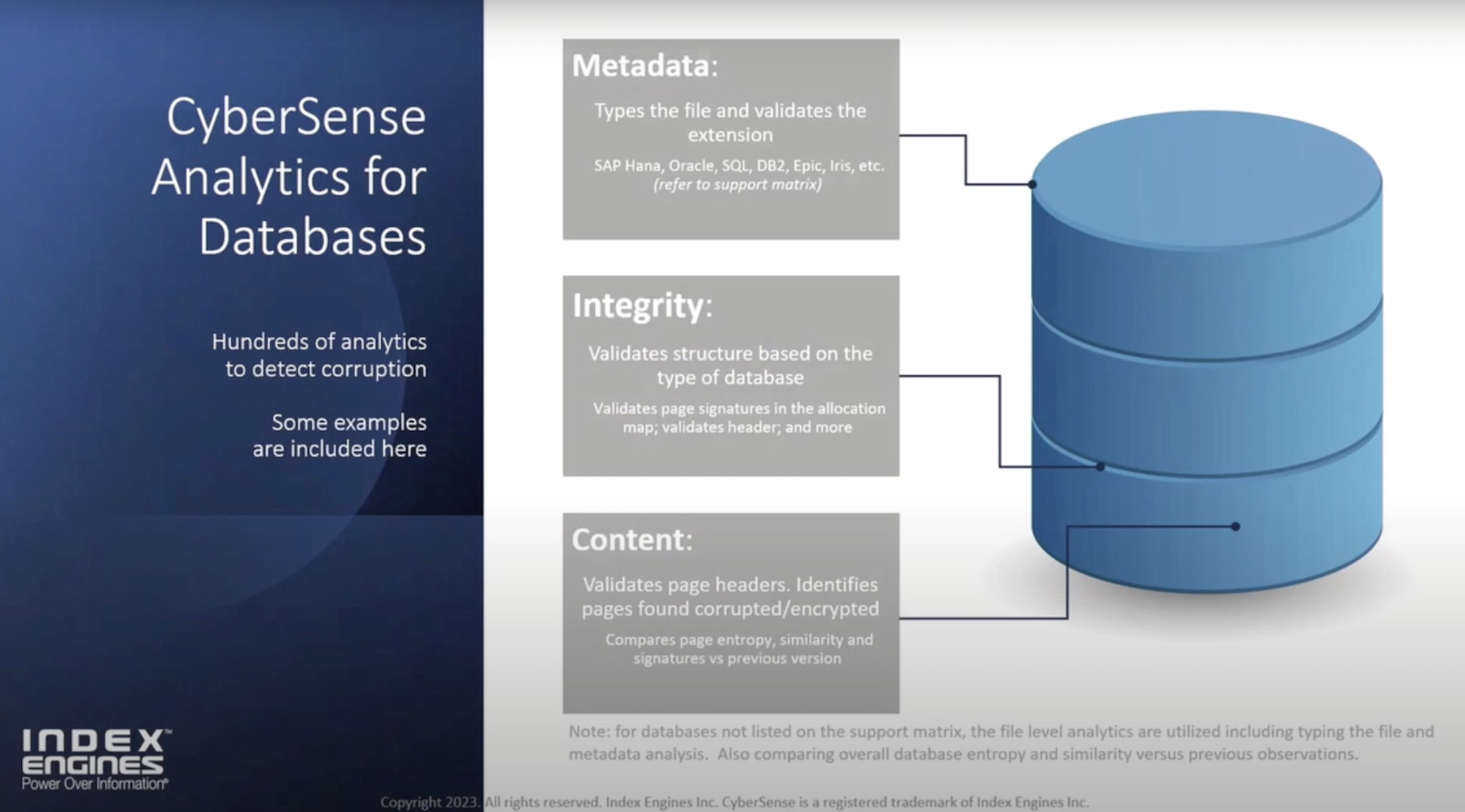
CyberSense is different from other security tools by its sheer depth and width of coverage. The only product to inspect files, core infrastructure as well as databases for signs of infection, it combs through all blind spots, and tracks down the most sophisticated threats.
The Who, What, Where and When of What Happened
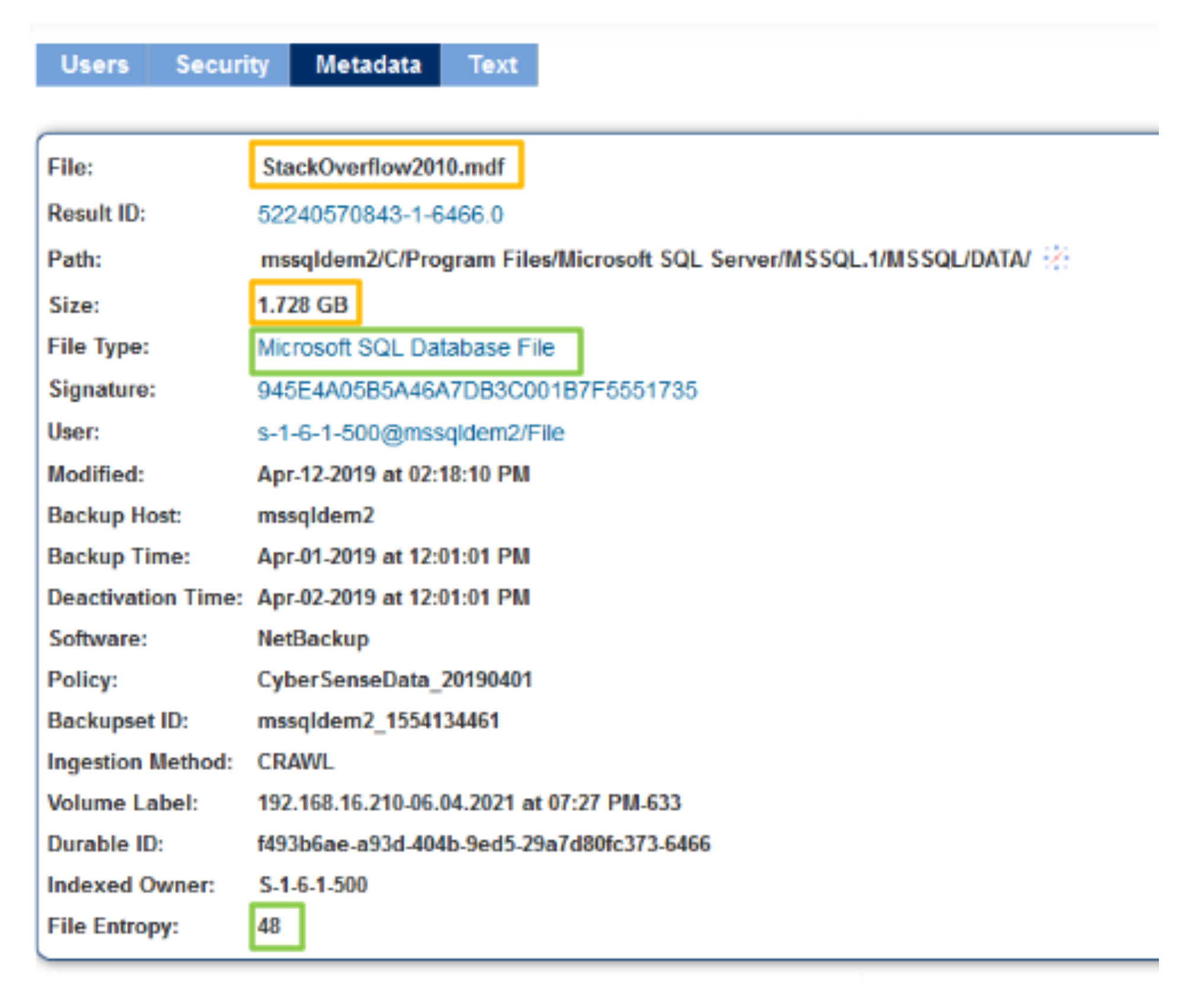
CyberSense relies on deep inspection of data to detect threats hiding inside them. But instead of relying on thresholds to guess malicious changes over time, it studies every replication of data by comparing snapshots hourly to weekly to understand the changes. It constantly validates metadata properties to confirm reliability.
Deep analytics is performed through full-content analytics. Stealth threats are detected with over 200 content-based analytics that examine contents of the data and skim out hidden abnormalities.
CyberSense has advanced machine learning models built into it that provide 99.5% confidence in detecting corruption. The algorithms are trained in all common and many rare variants of trojan and ransomware, and can process analytics rapidly to discover any tampering or modification done to the core infrastructure, backups, databases or user files.
CyberSense has the unique ability to minimize false positives and negatives down to one in every 50, 000 backups. Administrators are alerted only on confirmed suspicious behaviors and threats.
Mr. McGann informed that CyberSense has enabled clients to recover in a heartbeat without any data loss. The CyberSense post-attack dashboard displays the last clean version of files. The post-attack forensics report provides insights on the details of the attack, and information on the files that enable quick and effective restoration.
Wrapping Up
When living in a fast-changing, perilous digital landscape, the usual rules of staying safe do not always work. Besides being very wary of the threats out there, organizations also need to adopt new ways to fight them. With a tool like CyberSense, they can be absolutely certain of the threats dwelling inside their environments, and eliminate them early in the chain. By weeding out cloaked payloads from deep within the data, it gives teams a chance to trust their tools. High accuracy ensures that common alerts that can be dismissed without a thought do not become a distraction for the important jobs.
To catch a demo, and for deep-dives on CyberSense, check out Index Engines’ other presentations from the recent Storage Field Day event.