Security is the new imperative in tech. The ongoing attacks on business organizations and public institutes have revealed a shaky state of security, setting off a panic in the masses. With digital dangers mounting every day, a question that’s in everyone’s mind is how do average organizations prepare for cyberthreats?
A Chink in the Armor
As cyberattacks proliferated over the past two years, enterprises have rushed to embrace a profusion of tools, each guarding a different frontier. Presented with a bigger market and mission, security companies are reaping the rewards by selling point solutions to a frenzied customer that is operating under the belief that more tools equal stronger defense.
Never before has the belief that tools can preserve establishments run so deep. And yet news headlines are flooding with reports of hacking incidents. Increasingly, organizations are getting jittery that more dollars will be lost in accelerating their defensive efforts.
We met with Josh Fu, Global Head of Competitive Intelligence at Tanium, a leading provider of cybersecurity solutions based out of Washington, to ask what would be the ideal approach to re-establish safeguards of enterprises.
The good-faith efforts, we learned, are helpful, but has proved to be insufficient in the face of increasingly clever attacks. Fu, who has a deep and nuanced understanding of modern distributed environments from his extensive career in cloud computing, said that silos in security tooling infrastructures have started to be the chink in the armor.
“The point tools were not actually meant to talk to each other. Yes, everything can theoretically be API-connected, and automated in some cases, but they were not meant to do that. Not to mention, someone has to set it up and maintain that API integration, and there’s always going to be a limited amount of data that goes from one tool to another,” said Fu.
Attackers that are smart know how to get around these solutions. Instances of hackers exploiting solutions’ blind spots and shutting them down at random force us to think – what do those tools actually offer?
“Most of these tools just provide visibility. They’re really good at saying, here’s all the things that you have going on, but you have to send it to another tool to actually do anything about it,” Fu said.
With the hype and headlines around observability, it is little wonder that vendors are obsessing over observability, many times overlooking the real objective – remediation.
Hopping between solutions on an hourly basis is more than just inconvenient. There’s growing evidence that using more solutions weakens control, delays remediation and even hurts visibility in unexpected ways.
Instead, cyber gurus advise companies to embrace a more unified approach and work on consistently meeting security standards than periodically acquiring new tools.
This is where Tanium shines. “What’s really powerful about Tanium is that it is looking to replace or at least enhance a lot of these tools,” said Fu.
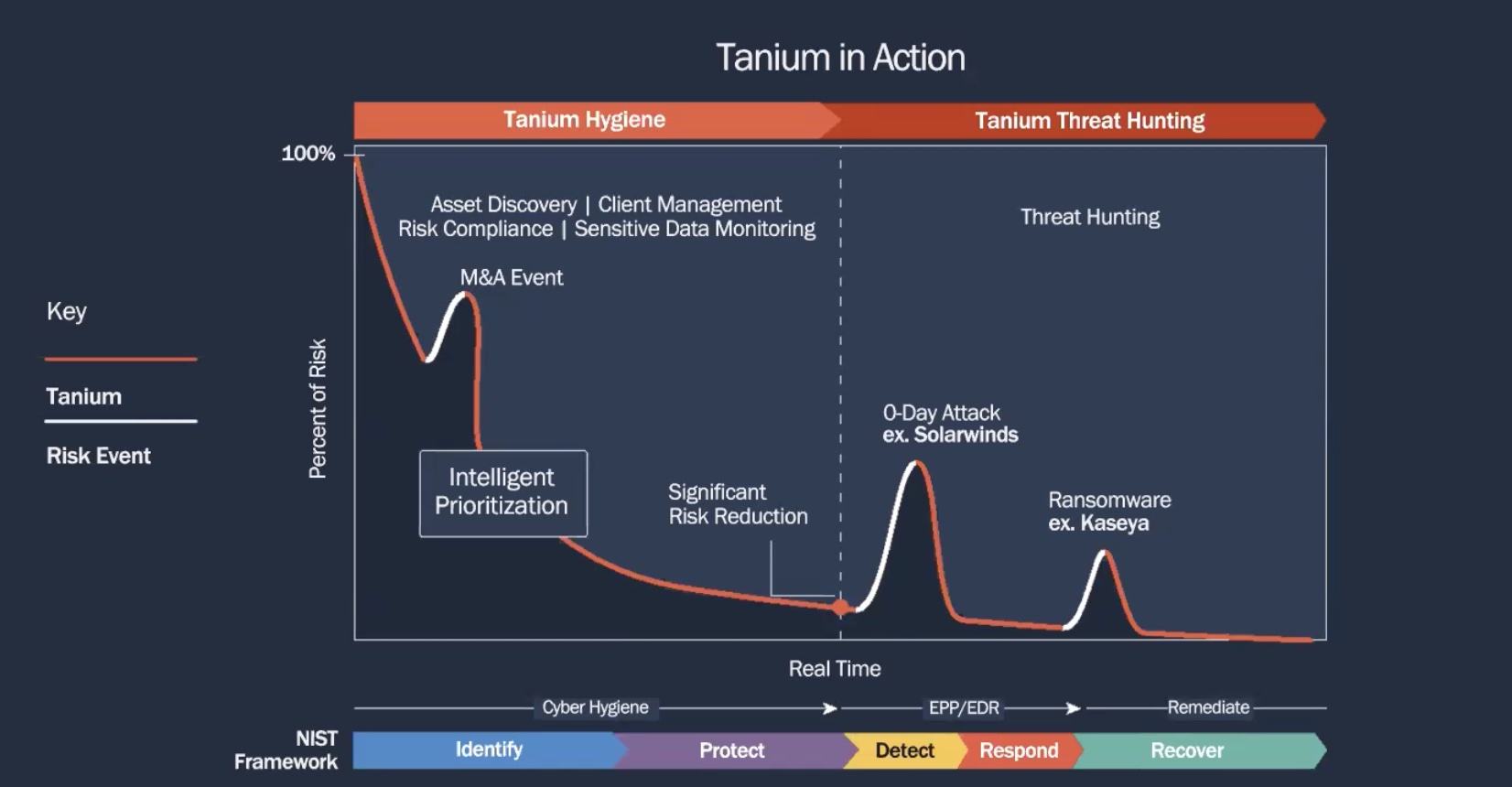
Scoping the Attack Surface
Tanium XEM is a one-agent solution that provides visibility, control and remediation all on one platform. XEM stands for “converged endpoint management”, meaning whatever endpoints a network has, Tanium offers management and security operations for all of them in a single solution.
Tanium’s chief differentiator from other security tools is that where other solutions solve select use cases, Tanium empowers operators to make rapid decisions which is the cornerstone of a sturdy cyber defense. This it does by supplying them information in real-time.
Fu argues, “In many ways, other tools are solving symptoms and doing less about solving the root causes of an organization.”
Typically, operators would grab data from disparate tools, glue them together, make sense of the problem and actuate an action. But since last year, companies started reporting attacks that are maddeningly fast, prompting need for a speedier response.
Tanium does the work of assimilation for the operators in real-time. “You don’t have to cobble together different sources of data from these different tools spanning your IT operations that then gets sent to your risk team or security team,” Fu said. “Tanium as a platform is using one agent to provide real-time visibility, real-time control and real-time remediation, regardless of how many endpoints you have,” he said.
How does it do that? There are a few different ways. Tanium offers Indicators of Compromise (IOC) Detect. Within security-specific use cases, it lets users search for threats in the environment. The UI lets operators look up malicious components by names. Tanium can scan millions of endpoints and bring back results within seconds.
But Tanium’s capabilities go well beyond fielding search requests in English. Its real superpower is first-hand investigation. “Security starts with understanding what endpoints you have because you can’t protect what you can’t see,” reminded Fu.
Tanium can connect directly to endpoints, where the problem resides. This gives Tanium a supervision which is impossible to have when sourcing data second-hand.
“We don’t start by looking at what other tools tell us. We actually go and discover those on our own using our own discovery capabilities, and we often find about 20% more endpoints than other tools,” he said.
This is followed by asset inventory, a step to catalogue assets in the environment. Tanium boasts a fast and robust asset inventory system that big partners like ServiceNow relies on.
With all ducks in a row, it is now time to probe into endpoint configurations and anything else that may be impacting performance, and harden them.
With every anomaly that it finds, Tanium provides insights on the nature of the element, where else in the environment it exists and actuate a remediation faster than the attacker.
“If they’ve left a ransomware, we can go and find it and remove it from everywhere before they have a chance to detonate it,” said Fu.
Based on the Common Vulnerability Score (CVS) and a host of objective metrics, the system determines the risk level of an environment. This allows organizations to see their risk score based on the endpoints as well as industry peers.
The Last Mile
A key feature is vulnerability scanning. Tanium scans continually for sensitive information – Personally Identifiable Information (PII), HIPAA , classified data, secrets – that maybe residing on endpoints.
But where other solutions leave it at discovery, Tanium takes a step forward and closes the gaps it finds with new software and configuration patches. Fu told us that Tanium’s vulnerability scans are extremely lightweight and most times, customers aren’t even aware of them running.
Remediation is a big part of what Tanium does. Functions like threat response and remediation are built into the console as modules so that operators can find everything in one place, instead of having to toggle between interfaces.
The same Tanium agent performs the remediation actions – no need to deploy a new agent. The agent requires installing on every endpoint to actuate remediation, but Fu assures that it does not take longer than a few minutes at even the biggest scale.
Remediation includes network quarantine, threat hunting, incident response and containment.
When measured against the NIST framework, Tanium shows great potential. It’s recovery capability stands out as exceptionally powerful being able to remediate not one but all endpoints at once, regardless of the scale. Fu informed that some of Tanium’s clients use up to a million endpoints. Tanium can rapidly search and troubleshoot them all in one fell swoop.
The Tanium XEM Platform is cloud-delivered and not dependent on on-prem hardware. The solution primarily focuses on client endpoints – laptops, desktops and servers – and supports OSs like Windows, Mac and a host of Linux distributions. Tanium v2.0, which has even more features than the current version, is on the way.
Wrapping Up
The irony of modern technology is that it has the ability to both enable and encumber. Using too many tools can easily undo the benefits users might be getting from a single solution. Instead, multi-purpose tools provide infinitely more value for money, and muscle power to fight off threats than an armory of point solutions combined.
For more information, be sure to check out Tanium’s website. To stay updated with everything happening in the cybersecurity space, check out the presentations from the recent Security Field Day event. For more stories like this one, keep reading here at Gestalt IT.




