Evolving business processes and technologies are inherently risky, and organizations tend to be risk-averse in the current climate. But the hazards of hasty transformation are thwarting their intentions.
We met with Laura Wilber, industry analyst at Enea, a company that has broken through new barriers in cybersecurity with the launch of a new threat detection (TD) software development kit (SDK), the Qosmos TD SDK, to dig deeper into this.
Dissolving of the Known Perimeter
As tectonic shifts in computing and work took place over the past couple years, it changed the network beyond recognition. On one hand, remote work format caused users and devices to migrate outside the confines of offices, exposing the network to new perils outside the usual boundaries. On the other hand, applications and data are becoming more distributed with multi-cloud unlocking tidal transformations. These reorientations have left organizations strained to keep their resources unharmed from eyeing cybercriminal gangs. The risk factors have risen manifold, and as a result, cases of scandalous attacks are heard more and more.
Wilber pointed that attackers have come up with increasingly clever techniques to breach the network. Spoofing is a popular one among them. It is a tactic employed by cybercriminals to impersonate as a legit user or device. Spoofing has two advantages. First, it creates a convincing disguise making it difficult to trace the origin of a traffic, and second, it stops the targeted devices from sending out signals. Attackers have used spoofing as a springboard to launch distributed denial of service (DDoS) and man-in-the-middle (MITM) attacks countless times in the past.
A Limiting Solution
Detouring around the storm, companies have sought refuge in old-fashioned intrusion detection systems (IDS). But increasingly, even the best-of-breed IDS solutions have failed to provide the expected level of protection, pointing to them as limiting.
Suricata is a good example of that, she said. Suricata has been an industry favorite for a whole decade, a mainstay in the enterprise cybersecurity toolbox. An otherwise efficient threat detection system, it has one thing that precludes it from being all-rounder – it is not natively designed to meet the tremendous performance demands of cloud, nor to recognize the growing number of applications and protocols of today.
“A challenge we’ve all had is, Suricata, although absolutely fantastic, wasn’t born for the cloud age, or for some of these extreme requirements that everybody has in terms of performance. And also, just everything is changing in terms of the type of devices that are connecting, IoT and OT devices. It’s a lot for Suricata,” says Wilber.
She points out the two chief areas in which users are stuck are its protocol coverage and performance. Today, Suricata recognizes about a couple dozen protocols, but there are over thousands of them out there. It can’t see cryptographic or basic traffic, and tends to get overwhelmed often, leaving certain traffic unmonitored. To combat the risks of a distributed computing world, it alone is not sufficient.
Tripping up Attackers with the New Enea Qosmos Threat Detection SDK
The new Qosmos SDK addresses Suricata’s two shortfalls precisely. With a fixed focus on encrypted traffic analysis, Enea designed the Qosmos Threat Detection SDK by embedding the top features of Suricata into the Qosmos ixEngine, a Deep Packet Inspection (DPI) tool. By doing this, it bypassed double packet processing and replaced it with deep packet inspection for more efficient analysis and deeper AI-powered traffic intelligence.
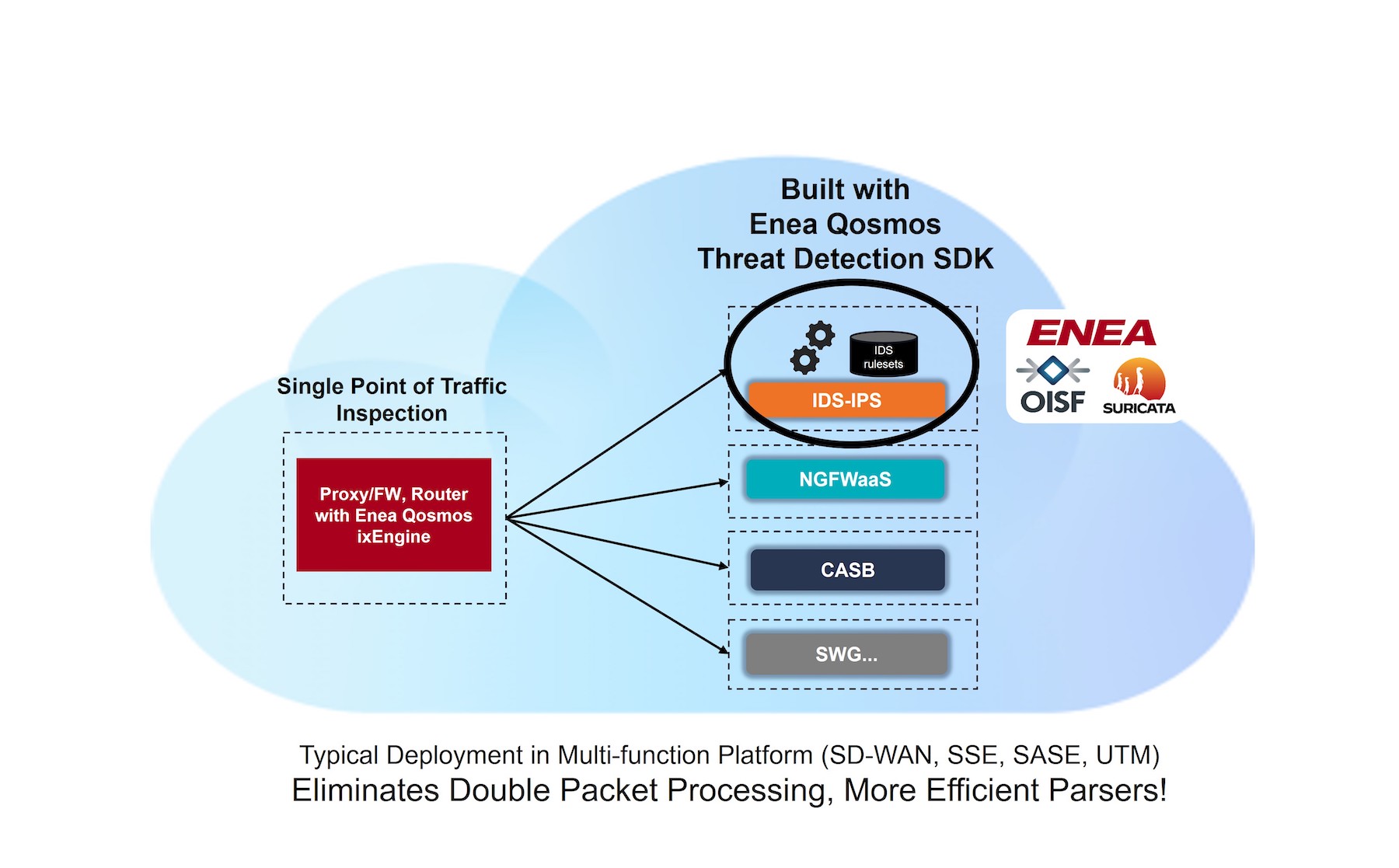
“We’re sitting out there on the network, and watching everything that goes by, like a truth test, especially with AI, whether somebody’s getting really clever with sleuthing,” said Wilber.
Enea’s deep packet inspection reaches the roots of the traffic and spots indicators of anomaly. But unlike a conventional solution whose search ends at indicators of compromise, aka the direct threats, Qosmos can identify anomalous traffic, making it easier to suss out spoofing attacks and rogue devices and apps.
Enea employs something called First Packet Advantage for enhanced accuracy and detection performance. First Packet Processing, on which it is based, identifies applications and services by looking at only the first packet of the flow. However, this process results in poor accuracy and low granularity. By contrast, Enea’s First Packet Advantage has two embedded capabilities – Cascading Cache Structure and Internet Protocol Database – that taper off the amount of traffic going through DPI processing, delivering substantial time savings and higher accuracy.
With AI in action, inspection gets next-level. “It’s not just trying to detect the service, the category of traffic – which some people are doing – but going on further than that, and recognizing applications and fully-encrypted traffic,” said Wilber. This lends a clear visibility into encrypted and evasive traffic that spoofing and MITM attacks fall under, something that is still outside the scope of conventional IDS solutions.
Parallel to that, Enea Qosmos Threat Detection SDK delivers a much-improved parsing speed, thanks to the high performance of the Qosmos ixEngine, making it fitting to handle the high traffic volume, typical of cloud.
As for protocols, Enea Qosmos SDK covers a whopping 4,300 protocols and 5,900 kinds of metadata. As impressive as those numbers are, Enea does not plan on stopping there. It discovers new applications and protocols round the clock, and updates them on the go.
“It’s a 24-hour shop to be looking for protocols, updating and getting them out to customers.” With Enea doing that automatically, there is no need to hire a team to just do updates.
Enea Qosmos SDK is extensible, and integrates tightly with third-party cybersecurity solutions.
In Conclusion
Hackers are increasingly resorting to cracking techniques that can replicate the look and feel of permissible traffics and sneak into high-value resources. This is made easier by shadow IT, and the risks of the technological transformation. In their effort to defend networks against spoofing and like threats, organizations need full and complete knowledge of the traffic in the environment. With its deep packet inspection capabilities, Enea Qosmos Threat Detection SDK heralds a new breed of IDS solutions that are made to order for the complex and vulnerable cloud networks of today.
For more info, head over to Enea’s website. For more such stories, keep reading here at Gestaltit.com.