Enterprises face a swirl of headwinds as they head into the second half of 2023. Aside from the recessionary economy and inflating costs, one problem that looms large is growing cases of ransomware attack.
With vicious attacks happening across the globe, there is added pressure within organizations to adopt stronger, more resilient cybersecurity capabilities to fight off threats.
In May, Zerto launched Zerto 10, the newest iteration of their two-in-one solution for ransomware protection and multi-cloud mobility. At last week’s Cloud Field Day event in Boston, Zerto demoed the solution’s newly added capabilities to the audience.
Zerto has a catchy tagline for Zerto 10 – “Real-time detection meets real-time protection”.
While the release has generated sufficient excitement in the crowd, at the event, Zerto laid out the key enhancements which make Zerto 10 a timely solution for organizations’ deepening ransomware needs.
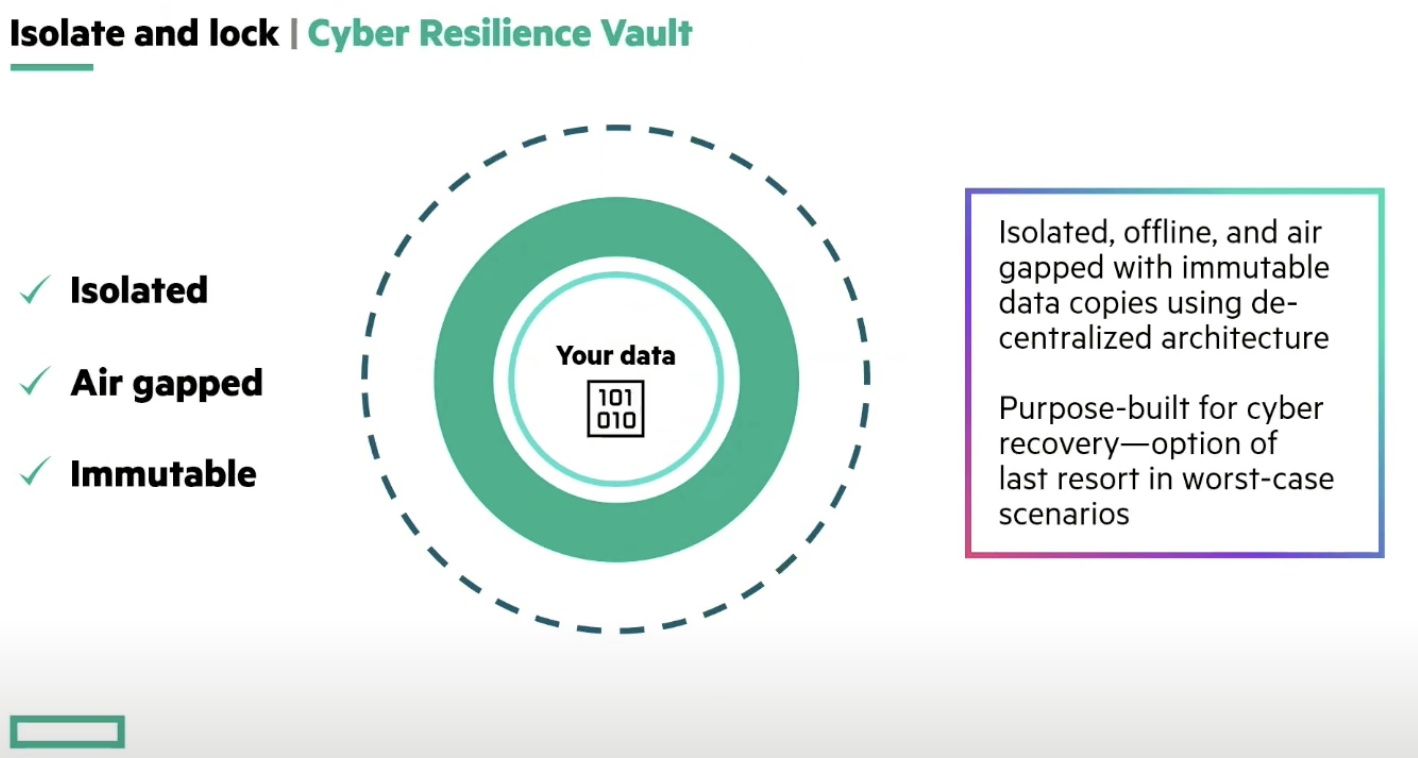
The ongoing wave of attacks and indiscriminate targeting of organizations prompt calls for aggressive response, and Zerto delivers. Zerto 10 reinforces the platform’s capabilities with four key additions – real-time encryption detection, cyber resilience vault, secure appliance and protection for Azure at scale.
Zerto 10 aims to push real-time protection into all corners of business, and the cornerstone for that is real-time detection.
At the presentation, Senior Technology Evangelist, Chris Rogers, described what the new real-time encryption ransomware detection comprises. With real-time detection, Zerto 10 continuously scans and searches for signs of encryption, enabling swift discovery and speedy action.
For Zerto, the steps to achieve real-time encryption detection are replication and detection, isolation and locking, and testing and recovery.
“When we look at the pillars, this is what helps us achieve ransomware resilience, and that’s hopefully going to enable our customers, prospects, partners, and everyone else to provide continuous protection for any app or any cloud, for any threat,” said Mr. Rogers.
Anatomy of a Ransomware Attack
Ransomware attacks have evolved alarmingly from the days of simple malware infections, to becoming a systematic extortion of ransom.
On a high level, this is what an attack chain looks like currently: The offenders gain initial access into the network through phishing, social engineering or whatever means available to them. Once inside the network, they move around seizing command and control of vulnerable systems.
As they move deeper into the network, they attempt to gain access of more assets, launching the infamous lateral movement attack which causes maximum damage. The extent to which lateral movement is successful beyond the entry point depends on a diversity of factors such as, the environment itself, the amount of staffing at that hour, the organization’s security posture, etc.
If they are able to successfully traverse the network, in the next phase, they disable security systems to elude detection. They will move up to the backup segment and turn off the backup agents taking away the only course of remediation. This entire period, security experts call, the dwell time.
“The interesting stat is that the median dwell time is only 5 to 9 days, according to Mandiant report this year. You’d think it’s much longer but actually 5 to 9 days makes sense because the longer they’re in there, the longer they risk being caught and not getting a payday out of it,” said Mr. Rogers.
In the next step, the inevitable happens. The attackers encrypt files demanding ransom from the victims, who, up to this point, are clueless of the attack. If caught early, they deploy a breach-kill-chain disconnecting the rest of the network from the infected parts and then work towards recovering the assets. Caught off-guard, the only way out is to pay off the attacker and redeem the data.
But between the stages of encryption and recovery, there is a time gap during which the organization does not know that encryption has happened. This window can be as short as a few hours to as long as several weeks. The longer it is, the wider the blast radius.
Rogers explained, “It can take time, and it also can take a lot of needless figuring out what actually the problem is – is it a network problem, an application error, a database coming down? The first port call isn’t we’ve been hit by ransomware attack. Probably it’s all the other things first, and then looking at what the possibilities are.”
Injecting Resilience in Ransomware Protection
This is the gap that Zerto’s real-time encryption detection seeks to close. Instead of keeping teams waiting to find out, or for the monitoring systems to pick up, Zerto 10 preemptively discovers the anomaly in real-time.
The other problem that Zerto addresses with the new capability is the inherent loophole in old-fashioned backup-based detection. The reason backup-based detection is no longer adequate for the level of sophistication of threat actors today is because it is slow, and causes unacceptably long repair times.
Backup software create periodic snapshots at an infrequent rate. “Most organizations are going to back up maybe once or twice, if they’re really keen, maybe four times a day, because that’s the nature of backup,” said Mr. Rogers.
Backup windows are typically lengthy and they impact the production. Compounded with the added problem of scanning old and large datasets, it becomes a costly process that does nothing to limit the ransomware impact in time.
“We’re recovering large amounts of data with software that’re designed for backup and not to recover mass at scale. Essentially what that leads us to is a longer RTO, a larger ransomware impact, and therefore higher costs,” Mr. Rogers said.
It racks up costs, not just in terms of dollars, but reduced brand value, damage to reputation, and loss of trust of the stakeholders and customers.
The Power of Real-Time Detection
Zerto’s real-time detection and alerting aims to provide early warnings that organizations need to contain the blast radius. Where traditional backup-based services back up blocks and files, scanning and restoring in a loop, Zerto upends the approach with streaming inline detection.
As the blocks flow through Zerto, it detects encryption in real-time, and sends alerts upstream to the Zerto virtual manager or a third-party API. Administrators can go into the platform and examine the forensics from checkpoints. This lets them run tests in isolated recovery environments to study and understand the encryption.
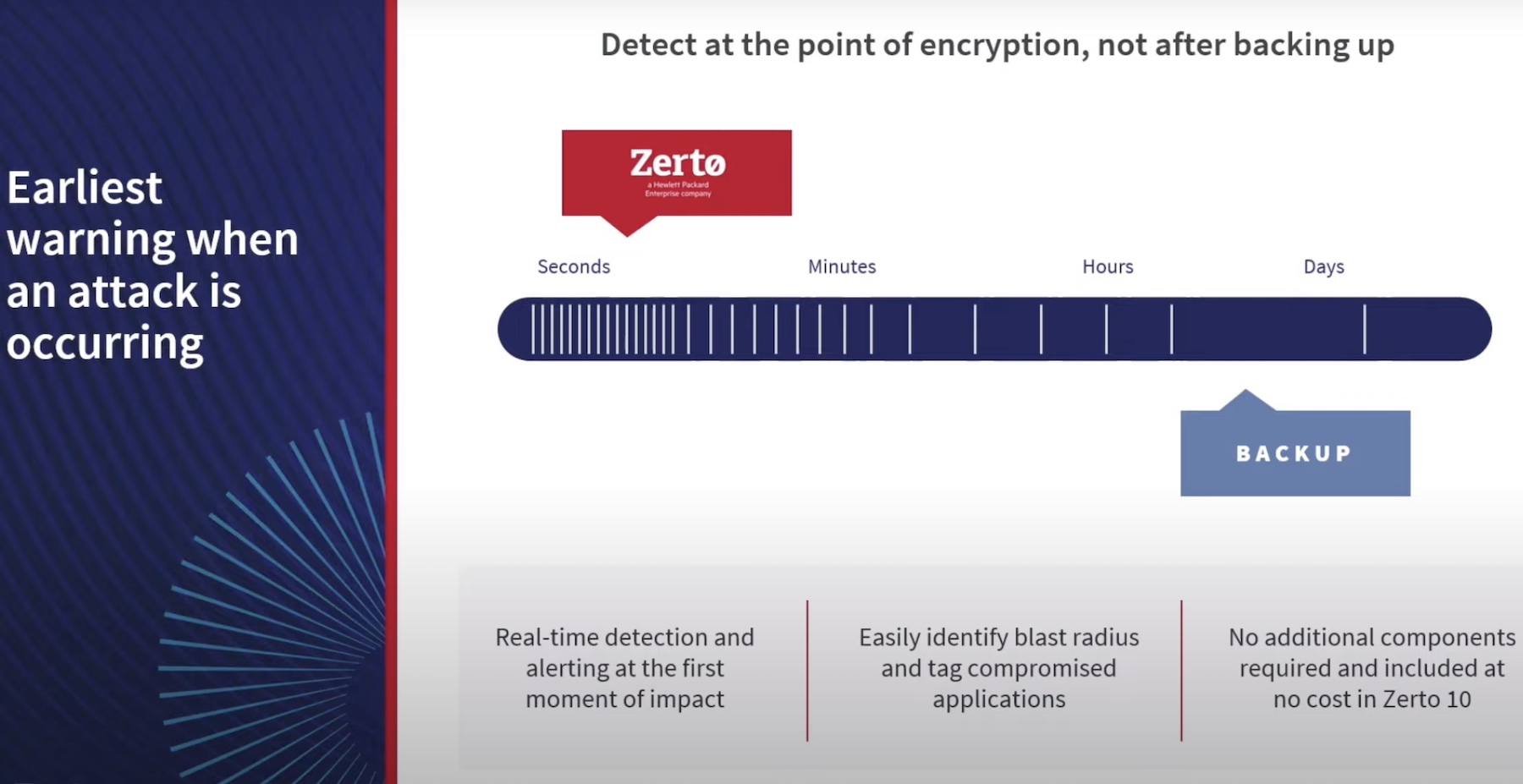
Zerto 10 enables users to easily identify the blast radius and tag compromised assets so that they can be inspected without wasting any time. Inside the UI, Zerto saves all changes and logs as recovery checkpoints which are replicated every 5 to 15 seconds. A journal stores the log of those checkpoints on an hourly basis and classifies all suspicious and clean elements, allowing users to easily dig in and study the blast radius.
Rogers said, “The idea of this is that it gives organizations the earliest warning sign that something is wrong. We still need the proactive tool to capture the threat before it gets in or as it gets in, and those signature scanning and everything else that we need in the environment, but we need to know as quickly as possible when something is wrong because speed is of the essence in this time. That’s the first point of impact that we’re going to see the first warning sign pop up.”
Zerto allows users to recover data directly on to production-grade storage and compute. The recovery process is swift and takes anywhere between seconds to hours compared to hours to days that traditional solutions take.
Set to go into availability this month, Zerto 10 comes at no additional cost to users. Zerto has added the inline encryption detection and alerting feature into the Zerto virtual machines that manage replication of VMs, to avoid additional use of hardware. As soon as the version is available, customers can upgrade and enable this feature at their end.
Wrapping Up
Ransomware attack is an organized crime run by the most notorious syndicates out there. Companies must understand that their fight is not against a lone attacker, but appointees of these entities. To fight that fight, they need a weapon like Zerto 10 that strikes at the heart of the ransomware scourge with advanced and real-time capabilities.
Watch the demo of Zerto 10 from the recent Cloud Field Day event at the Tech Field Day website.