Have you ever gone into a building that gives you an “Escort Required” ID badge? It’s fairly common for businesses that have secured areas on top of the front door check-in. The kinds of places where wandering aimlessly could get you in trouble or where all kinds of people that do various single-focus tasks need to be kept on target.
“Escort Required” is the kind of security that admits that even the most capable security needs some form of monitoring to be effective. You can’t just put a control in place without measuring what it’s doing and how effective it is. Monitoring and security are something that goes hand-in-hand.

Let’s take containers as an example. With the rise of cloud and DevOps, the unit of work that is done by the infrastructure has shrunk from server to virtual machine (VM) to container. A container is the ultimate form of work reduction. Instead of a purpose-built operating system running a full application, you now have a purpose-built system to run a service or aspect of a full application platform. When you need it, it’s available. You need more you can create them on the fly. And when you’re done, you can destroy them and conserve resources. It’s just-in-time service delivery.
However, for the security team, tracking things like containers can be a nightmare. How long do you think the average container lives in a DevOps organization? I found out that more than 50% of containers have a lifetime of fewer than five minutes. That means that over half the containers in existence won’t be around before you finish reading this blog post. Think about how much time five minutes really is, especially with regards to technology. While users today have a penchant for being rather picky and impatient about how their technology works, many of them can wait over five minutes to be sure they actually have a problem before reporting it.
Imagine how difficult it can be to track that down and fix an issue or resolve a security concern. Worse yet, imagine if you’re using a platform that does an inventory of your containers every few minutes and starts missing short-lived systems. Is your compliance department going to accept that something might have maybe happened in the three minutes between your last inventory sweep and this one?
Digging Into the Details
Back at RSA Conference this year, I had a chance to hop over to the Sysdig offices and talk to their team about how they’re solving these issues. As luck would have it, they’ve been thinking about security in much the same way as outlined above. Instead of putting security controls in place and hoping that things are going to be okay, they realize that you need to monitor those policies to make sure they’re working. Likewise, they also know that if monitoring turns up some issues with the applications or systems they’re monitoring, there needs to be something working at that level to make it gets taken care of before it spirals out of control.
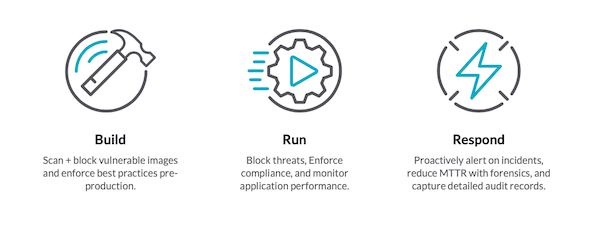
Sysdig gets a lot of interest in their DevOps platform from both sides of house. Monitoring teams and security teams both see the value from their perspective as well as what Sysdig can bring to the rest of the organization. The platform includes Sysdig Secure and Sysdig Monitor. They both contribute to the importance of the development lifecycle as they see it. To Sysdig, the cloud-native lifecycle includes three big pieces that need to be addressed at different times:
- Build – Sysdig can help at the beginning of the process by ensuring that the building blocks of the system are working correctly from the start. You can use Sysdig to enforce image polices and block bad components from being used. Find out that there is a vulnerability in a specific release of a service? You can block the bad version from being instantiated and enforce a policy that only the fixed version is able to be started. You can also use the monitoring side of things to ensure you’re not running any vulnerable versions in your organization.
- Run – Once your application is built it’s time to make it work, right? But you still have to make sure it’s being used safely. Sysdig helps enforce security policies about which containers can be started and how they are allowed to interact with each other. Does your organization have a policy about a minimum or maximum number of container pods that can be running at any one time? Sysdig helps you enforce that. Need to start more pods because someone wants to buy your new widget after it was featured on a national morning show? Sysdig can tell you when you need to step up your game.
- Respond – Having analytics means nothing if you can act on them. The easy examples come from needing to create more resources to handle things. But the ability to use a platform like Sysdig goes deeper. Sometimes it’s not enough that you responded to an incident. You need to prove how quickly you did the due diligence to get in front of a problem. Think about all the news stories of incidents where the organization didn’t respond for months. That’s the kind of thing you don’t want to have to tell the media or regulators asking tough questions. Sysdig even gives you the capability to automatically remediate issues to reduce the mean time to respond (MTTR) to ensure you can say that you’ve done everything you could to resolve issues.
Bringing It All Together
Security means nothing without monitoring. Ensuring that your policies are being enacted and verified is critical to not only doing things correctly but informing regulatory agencies that you’re doing it right as well. You need the kind of platform that will walk with you every step of the way to help you confirm that things are working the way you expect. Sysdig has the right perspective to help you make the correct decisions when it comes to DevOps security and monitoring. They’ll escort you through the tough stuff to get you to where you need to be.