Security operators are burning the candle at both ends to keep trespassers out of enterprise networks. But despite leveraging the sharpest tools and the smartest technologies available in the market, speedy discovery and rapid response remain out of their grasp.
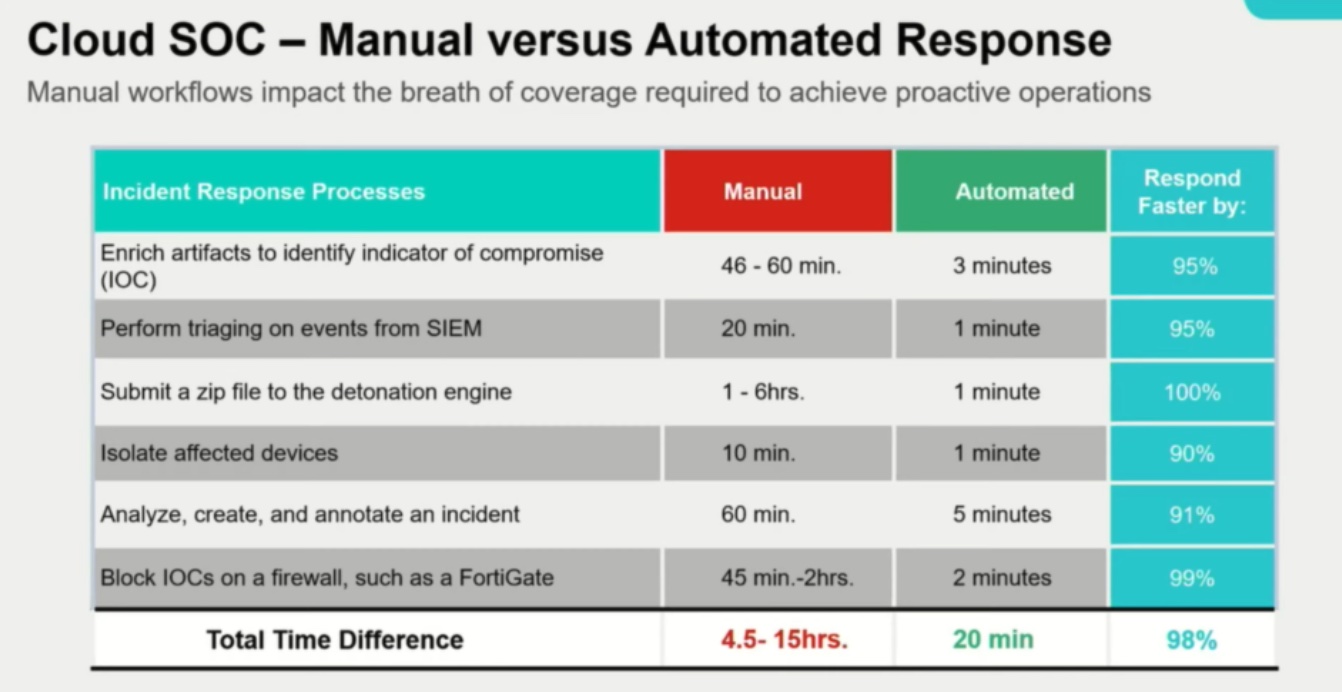
Case studies show that with manual workflows, it takes Security Operation Centers (SOCs) an average of one hour to identify an indicator of compromise, another 20 minutes to perform triage with SIEM solutions, and anywhere between 1 to 6 hours to isolate the affected devices.
Engineers have developed a way to perform these time-intensive steps under 20 minutes. It involves strategic implementation of automation and AI. At the recent Cloud Field Day event in California, Fortinet presented FortiWeb, an AI-powered security solution that reinvents application lifecycle security.
A Three-Pronged Approach
For Fortinet, app lifecycle security is about having maximum coverage. “When we say full app lifecycle security, we’re really talking about the inception of the application, the personas involved in delivery – the developers, the cloud SOCs – and come full circle and involve all of those personas and some ownership of the security, so we can provide the best protection in pre-production through production,” said Aidan Walden, Global Director of Public Cloud Engineering & Architecture at Fortinet.
Walden breaks down app lifecycle security into three core building blocks – visibility of the ecosystem, automation of administrative works, and AI-based analysis.
“Visibility, SOC automation and using of AI as a force multiplier are going to be pegged against API security because it is one of the two major challenges.” The other being phishing, which is still a number one problem in the cloud, but if you just take cloud in and of itself, Walden says, API security is top priority.
With cloud adoption at its peak, enterprises are going through rigorous phases of migration. They’re deeply invested in understanding the people, the processes, the tools, and the data that needs securing for the process to be a success.
“We always start with understanding the organization, the personas involved, who we’re working with, and who needs to be involved in the security workflows, and then helping customers to really overcome the hurdle of not having enough resources to deal with the signal velocity and volume,” he noted.
But tools rarely show up in the first five things on the agenda. With so much signal coming out of cloud from the breadth of solutions deployed, and security features turned on across multiple cloud environments, it’s getting increasingly problematic for monitoring tools to extract contextual intelligence.
“Something our customers are after is to have an accurate view of the assets, the data in those cloud enclaves, and policy consistency,” told Walden.
As customers move more of their workloads to the cloud, they face a series of security implications. Key among those are insufficient and inconsistent security coverage, and a tool sprawl that gets worse with time. “What we are hearing is integration across different best-in-class toolsets creates problems and technology debt,” said Walden.
With approximately 50 security solutions generating over hundreds of alerts daily, it’s hard to keep a steady eye on every last warning. Eventually operators tune them out as alert fatigue sets in. In an average enterprise, the SOC prioritizes alerts manually which further delays the response time. In short, the labor-intensive nature of the work strays them away from the path of ensuring “maximum risk reduction at the lowest cost basis”.
The Enormous Scale of Cloud
At today’s scale where half the organizations have over 100 applications in their environment, and on average, they push out 25 software updates monthly, usual security methods are redundant. “The number of application iterations and updates is a multiplier against the number of applications you have. So the change management and keeping up with it from a policy perspective is very difficult.”
It takes a different perspective to approach this. “The traditional web application firewall (WAF) approach is cumbersome and not very useful from a practical implementation perspective. So it has to evolve.”
AI can help alleviate a lot of these problems. The fast and clever attacks prompt proactive security, that only automation can deliver. The time savings achievable can be as high as 98%.
“We believe that good tooling and good integration across the ecosystem is paramount to app security effort.” To leverage that, Fortinet melds automation and DevOps into security practice.
When our customers want to improve their SOC practices, we try to understand what the overall level of effort is, how long it is taking them to identify a threat, and remediate it,” said Walden.
In most cases, it’s an hour-long process. “But when we implement integrations across the vendor ecosystem, different cloud capabilities and toolsets, automate the touchpoints and decision-making points, and provide context for the operators, we can literally take hours and turn that into minutes, even seconds.”
Web Application Protection with FortiWeb
FortiWeb delivers broad protection with five core features – web application security, bot defense, regulatory compliance, API security and SOC operations. Each of the features is boosted and optimized with ML and automation.
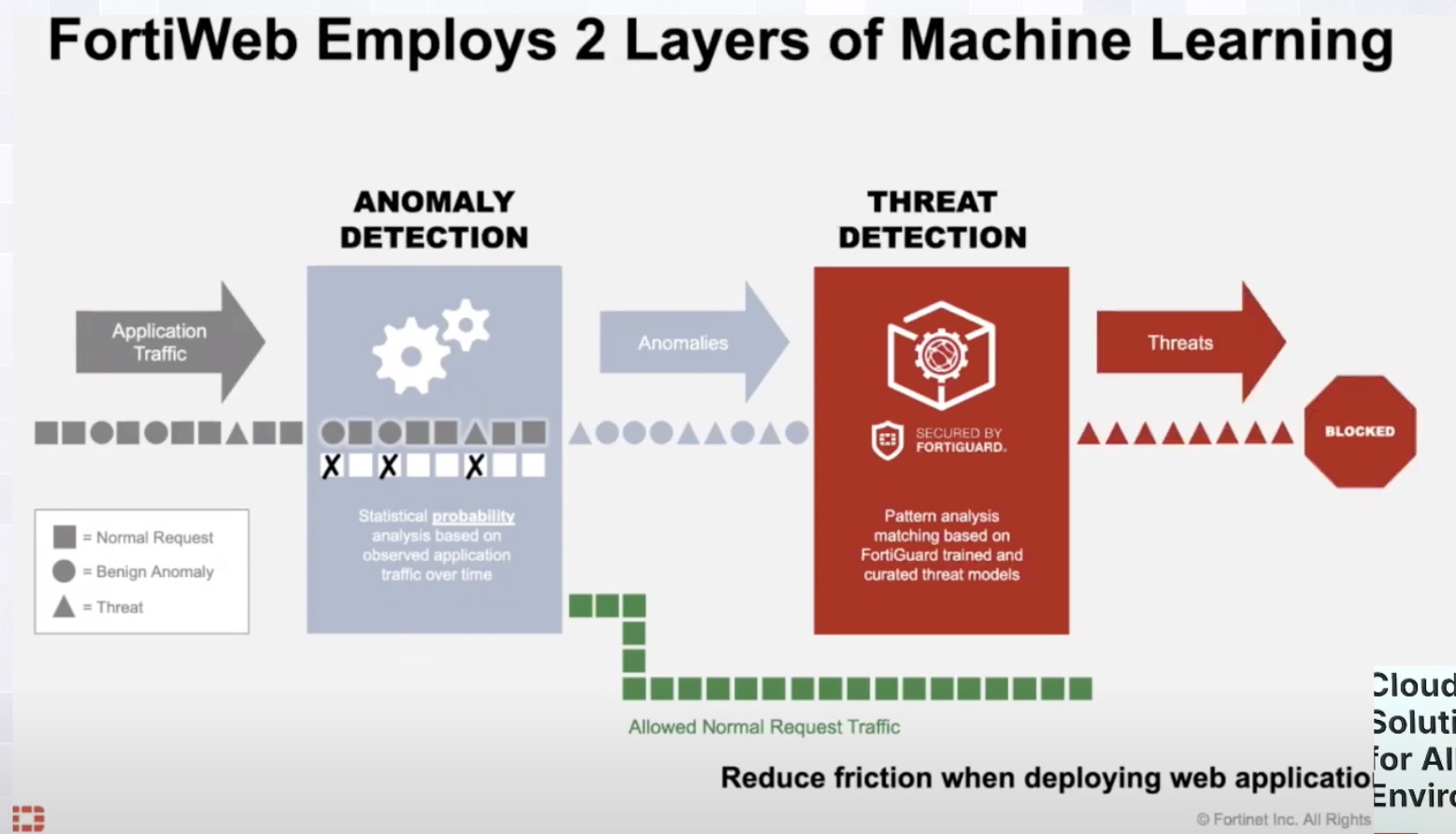
FortiWeb uses a two-module machine learning. It works by studying the interactions between users and applications, and learning the schema from it. As the model learns, it is able to identify benign deviations from malicious anomalies with increasing accuracy.
“Historically, in order to build a security policy that’s very specific to an API endpoint, somebody had to document it. Typically, the application developer took cycles away from developing to document. That’s very labor-intensive and took hours or longer potentially.” By contrast, automation does it in minutes.
FortiWeb feds the data into the modules within the ML engine that is being trained for the API in question. “As that scheme and the parameters are being understood, policy becomes very bespoke and specific to that particular endpoint so we can tighten security to that API without interrupting, creating false positives or blocking users inadvertently.”
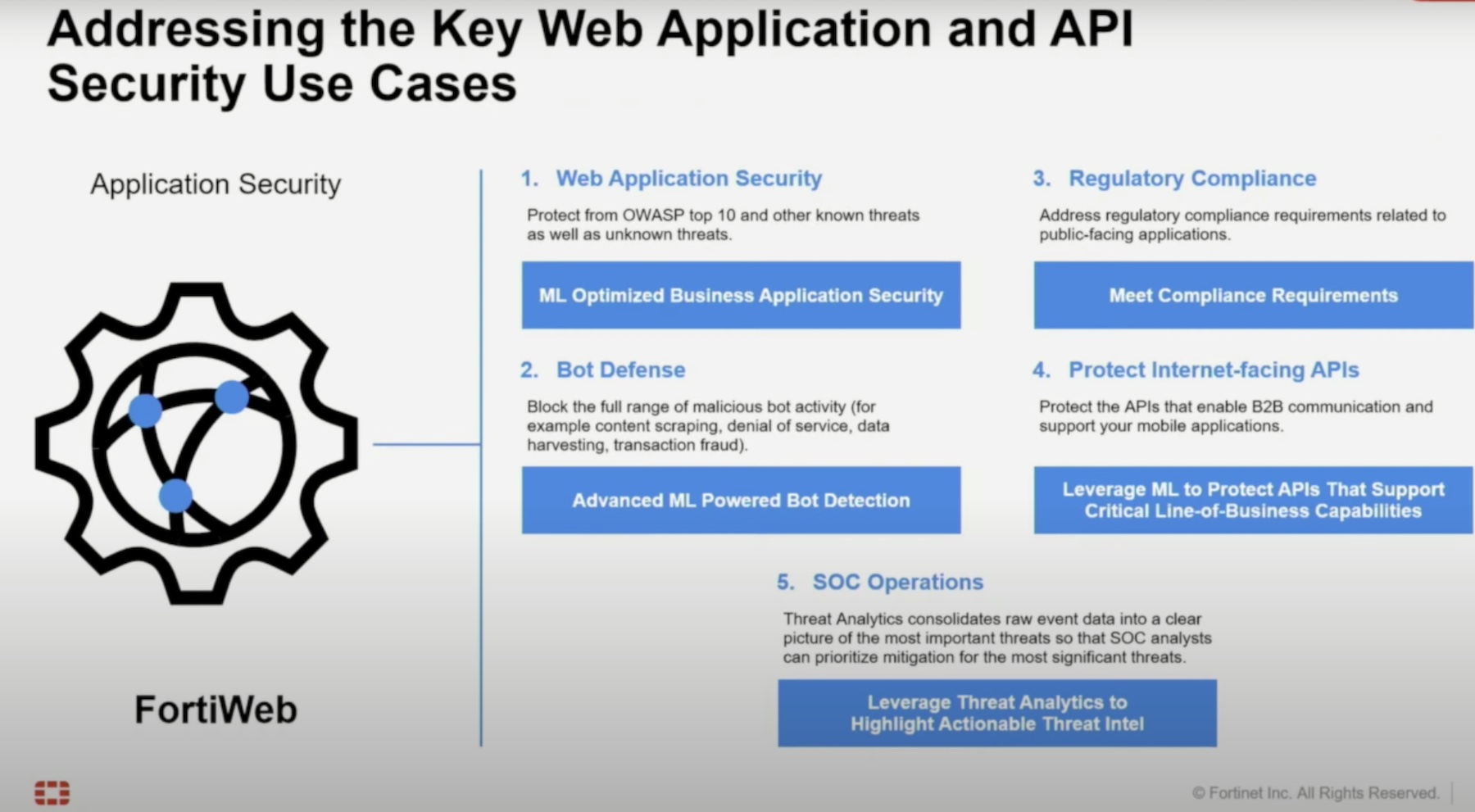
Fortinet provides advanced API protection by enabling a single access point to APIs. To prevent potential exposures, it masks the internal structure of the APIs from the outer web. Advanced API gateway features like key verification, rate limit control, API user management, and API call rewriting fortify the security further.
Walden emphasizes, “Whatever the application form factor is, whether it is a service-oriented architecture or microservice, we have protections for those.”
Fortinet likes to automate SOC operations at scale to offload the administrative burden as much as possible. The solution consolidates security events to zero down on threats quicker, and point to threats that require immediate attention or a policy change, in the process reducing manual analysis work.
“What we are doing is creating locally significant threat intelligence that enriches the security of the application for the SOC operator,” said Walden.
These automation playbooks generate contextual advisories, and take actions on behalf of the operators, enabling them to better understand baseline and anomalous behaviors, and dispatch responses instantly.
For more information, be sure to check out the demo session on FortiWeb and FortiSOAR from the recent Cloud Field Day event.