To err is human, to forgive divine. – Alexander Pope
With all deference to the immortal words of Mr. Pope, which were written over three hundred years ago, erring in today’s world isn’t as forgiving. The fastest way to find a grammatical error in a paragraph is to post it on the Internet and wait for the comments. Trying to prove something? Just post the opposite as a fact and wait for someone to point out the exact opposite just to spite you.
Those are the simple human errors that get caught by other humans. What about the errors that don’t need another person to capitalize upon? These are the kinds of errors we see every day online. Someone types their password into the wrong window and it gets posted to Twitter. Someone posts a social security number publicly and scrambles to take it down. Worse yet are the programmers that do things like post an AWS API key to their GitHub repository and then figure out what happened and try to get it taken down quickly.

This last one is a huge issue because there are a ton of scripts and bot programs out there just scanning for the pattern of an SSN or an AWS key. Once they detect one, they copy it along with location and user for future exploitation. Even if you think you deleted your error fast enough, you probably didn’t. It takes less than five minutes for your code commit to be publicly available on GitHub through the API. As soon as that happens, you can bet someone is scanning for the things they can use to exploit you or stand up a bunch of AWS instances for some nefarious purpose on your dime.
Even worse is the GitHub policy for code removal. You need to file a DMCA takedown to have your code removed. And even that doesn’t get all the branches and forks of the project. Add in how often GitHub gets mirrored for redundancy and once you squeeze your API keys out of the tube, you’re not getting that toothpaste back in. You need some way to detect that you’ve published something on accident and a way to get notified quickly so you can remove it in that short window or even invalidate the key and start fresh so you don’t get exploited.
En Guardian
I had the opportunity to talk to a new company trying to solve this issue a few months ago. GitGuardian is a platform that is trying to detect and remediate the exposure of secrets on GitHub. I talked to the CEO, Jeremy Thomas, about what’s happening in the space.
Jeremy told me that one of the biggest issues that they’ve been seeing lately is the number of developers that are cloning branches of corporate code to a personal repository to work on it from home or outside of work hours. These code branches will eventually be merged back into the main project but they represent an expansion of the threat surface. Your company may have invested in a very comprehensive code checking and remediation system. It may protect your developer teams from making the kinds of mistakes that cost big dollars. But does that system also protect your outside contractors? Or your users working from home? Does that expensive corporate platform give you the flexibility to assign licenses to anyone that could be working on your codebase?
GitGuardian is taking a different approach. They’re offering free detection and remediation for individual developers. Just sign up for an account and point GitGuardian at your personal repository. As you commit code, the platform will scan for things like database credentials and hard-coded passwords. If it sees some secret being leaked online, it will alert you and give you suggested remediation steps, up to and including invalidating the credential to ensure it can’t be misused.
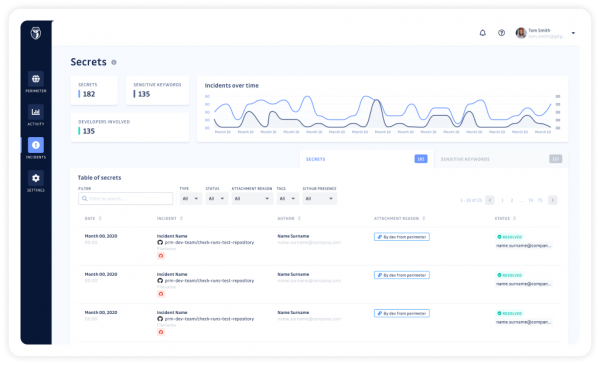
People are going to make mistakes. That’s their nature. We can build a certain amount of protection inside the walls of a corporate office. But we are also asking our developers to do more and more away from their desks every day. These inventive folks are using more and more tools to work longer and harder. Why not give them the opportunity to add a bit more protection into the mix? Corporate users can also purchase GitGuardian subscriptions that let them monitor individual alerts for teams and consolidate the data to ensure that no one is accidentally publishing things they shouldn’t be. It’s a small price to pay for peace of mind.
Bringing It All Together
No system is completely foolproof. Mistakes often have a life well beyond their initial impact, especially when that mistake leads to exposure of sensitive data or costs the company a significant amount of money in higher bills or stolen resources. Something free and easy to set up is a great first step to helping you ensure you’re not doing something you’re going to regret later when you hit that Publish button. You may not be able to stop making those kinds of careless mistakes, but at least with GitGuardian, you’ll know about them before the rest of the world has a chance to capitalize on them.
For more information about GitGuardian and their secret detection platform, make sure you check out their website at http://GitGuardian.com