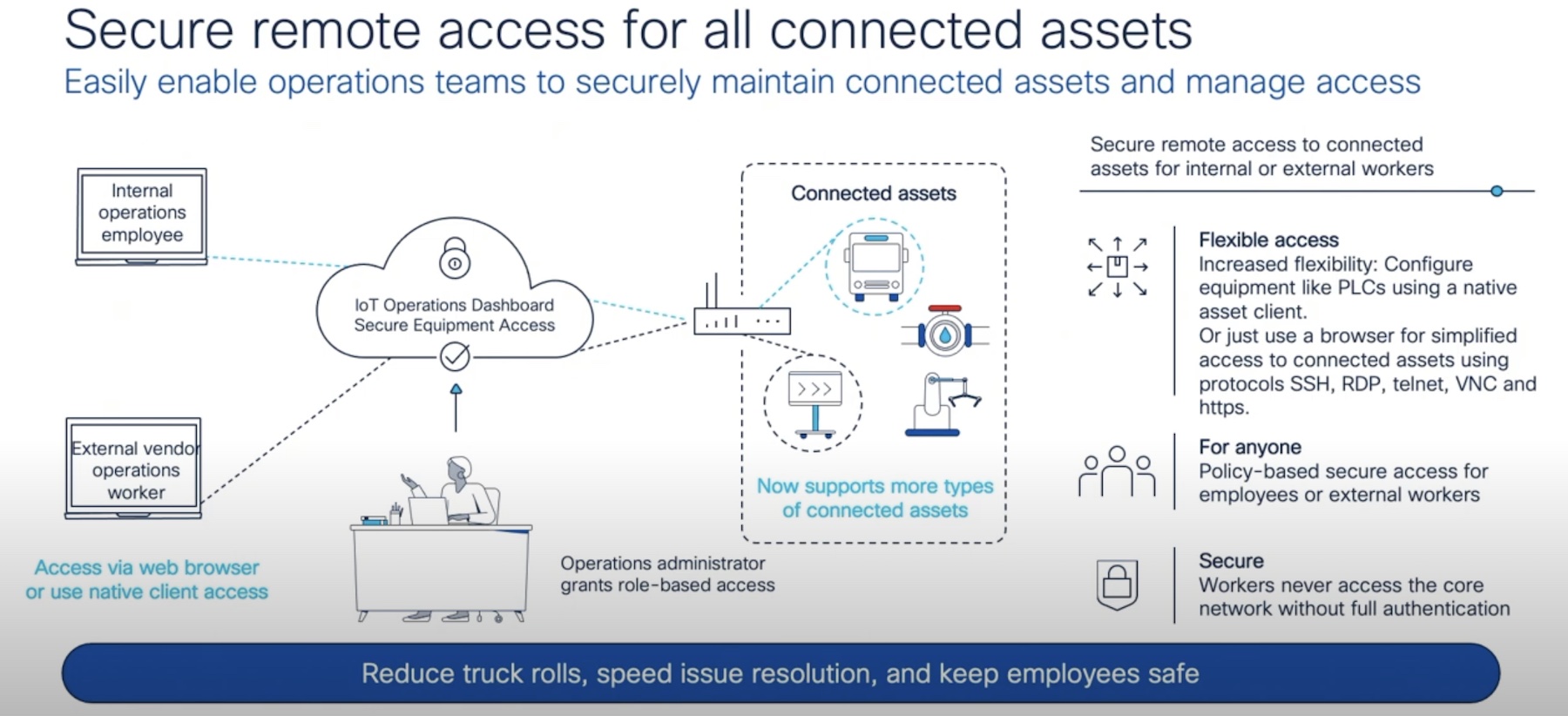
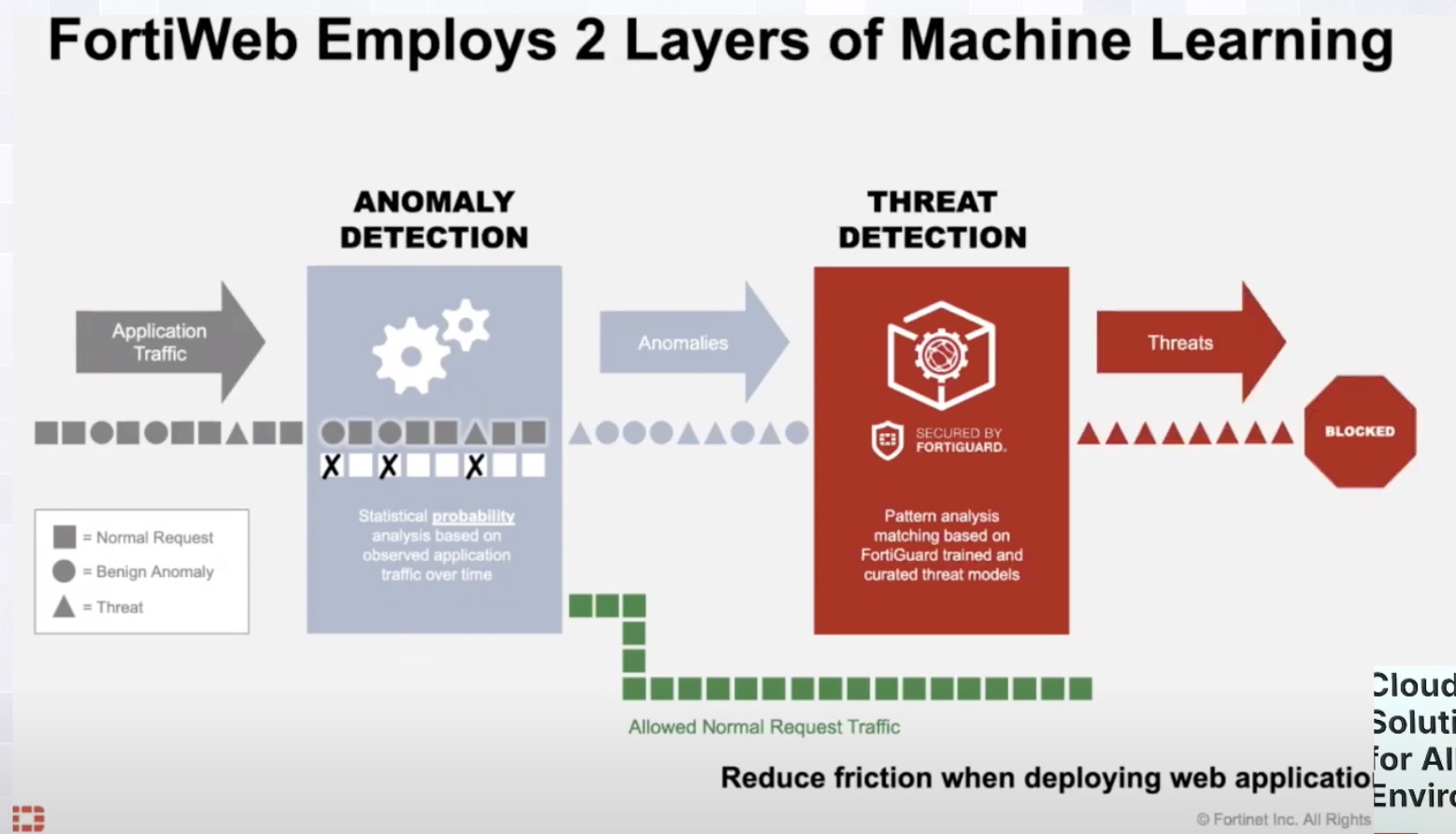
Internet of Things (IoT) devices need to be just as secure as every other device in your network. They’re just as much of an entry point into your secrets as a computer or a mobile phone. But the huge difference between a big, beefy laptop and a smart lightbulb can be legion when it comes to CPU and memory resources. And what’s one thing that takes a lot of CPU power? Creating encryption keys.

Ray Lucchesi has been taking a look at the challenges of securing IoT devices as of late, especially with the revelation that factoring RSA keys improperly can cause them to be easier to exploit. Some of this challenge comes down to figuring out how to provide the right amount of entropy when randomizing the keys. That’s a task best left to a CPU that doesn’t run on the lowest amount of power possible. I talked a bit about the challenges of good randomness and entropy in cryptography last year with Crypto4A.
Ray has some good thoughts about how to farm out the creation of RSA keys to help provide enough diversity to ensure that no attacker can use similarity to attack your infrastructure:
I remember in times past when tasked to create a public key-private key pair I had to type some random characters. The Public key encryption algorithm used the inter-character time interval of my typing to generate a random seed that was then used to generate the key pair used in the public key. I believe the two keys also need to be prime numbers.
Perhaps a better approach would be to assign them keys from a centralized key distributor. That way the randomness could be controlled by the (key) distributor.
Ray has a lot of other great ideas around security IoT here: Breaking IoT security