Gartner predicts that by 2025, 60% of organizations will have adopted Zero Trust as their opening security move. As companies calibrate and recalibrate their security strategies in a bid to thrive in a hostile digital environment, embracing principles like Zero Trust has become increasingly pivotal to managing cyber risk.
Experts say that a change in mindset in the way companies treat these risks is afoot across organizations. But they need to avoid falling into old and unhealthy habits, and instead let their thinking evolve. On that point, experts believe that a good start for organizations looking to embed Zero Trust and similar principles is to look at security not as an isolated thing, but a piece of the bigger pie.
No matter the model they have in mind, organizations cannot afford to implement security in all corners of the business without the use of supporting technologies. Among those, automation plays a star role.
Security through Automation
Security and automation in the age of edge computing are not two separate, but one discussion. It’s something CTOs have emphasized over and over. At the recent Edge Field Day event in San Francisco, this topic was at the forefront, as companies presented their automation-powered edge solutions to an audience with varied backgrounds in IT, aka the real users.
Backstage, we hosted a roundtable discussion with two of the attending delegates, Carl Fugate and Josh Warcop, and presenters, Raghu Vatte, VP of Product Management at ZEDEDA, and Ramtin Rampour, Technical Marketing Engineer at Opengear to dive into the subject of automation’s growing role in edge security.
Host and publisher of Gestalt IT, Stephen Foskett got the discussion going by asking Mr. Rampour what his take is on this, as an insider.
Mr Rampour replied, “I think (security and automation) definitely go hand in hand, especially with the scale at the edge, and how many nodes and units are deployed. You want something that you can securely deploy, but you can make something very very secure, but not as automated. So, you have to find the fine balance of quickly deployable solutions that are also done in a secure fashion.”
Mr. Rampour cited the example of warehouses where there is usually a fleet of devices, and the security of those devices is paramount. Replicating security flawlessly for each of the devices is where the real power of automation is.

Through a Different Lens
Security is often perceived as physical and logical, but even with an integrated approach, enterprises end up short if it is not enforced evenly at all levels.
Mr. Vatte said, “Security is about putting on the layers of hardware, operations, and applications, and people who handle it. Security is only as strong as the weakest link in the system, and when you are dealing with distributed assets, and people who are going to be interacting with the solution, you need to be able to enforce security.”
Automation is likely to shape how we think and implement security at various levels. The road to sound and sturdy security begins and ends in automation, not the manual methods of people doing it.
“It’s great to be able to define these layers, but if you are not able to enforce security, then things crumble. And the way to enforce security is making sure that you automate it right from the beginning, all the way to the end. That’s not just making sure that you install it and set it up properly, but also monitor it and make sure that if there is a problem, you know how to fix it,” Mr. Vatte added.
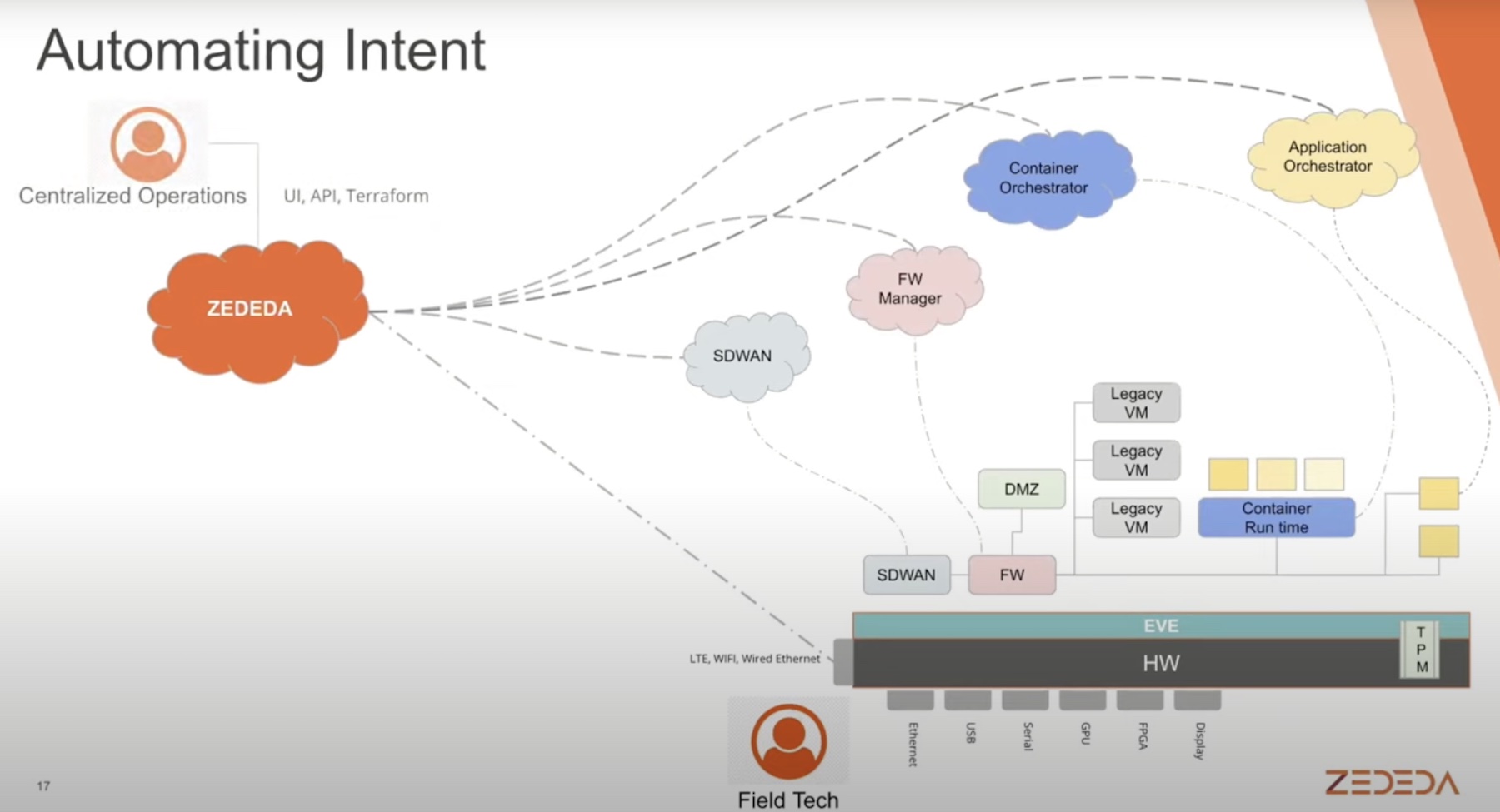
ZEDEDA’s Edge Management and Orchestration solution leverages automation to deliver total visibility, and remote management of hardware and applications across edge locations.
Old Ways and New
Mr. Warcop raised the question whether automation is a way to finally get away from the legacy way of operating in security.
Automation, in effect, Mr. Vatte explained, is less about doing things differently, and more about doing things right. Its purpose in the context of security is consistent and streamlined execution of all intents.
But, by no means, is it designed to replace the people who manually enforced security up until automation entered the scene, but to empower them and execute the repeat tasks on their behalf where possible, thus offloading some of the burden, Mr. Vatte explained.
At the root, edge security is a derivative of datacenter security. Carl Fugate joined the dots by pointing out that security for decentralized resources is akin to what it was at the datacenters which is the birthplace of Zero Trust. Now as the assets have moved out of the protective confines of the datacenter and fanned out across numerous physical locations, the enforcement of it has changed.
Whereas enforcing physical security in datacenters is uncomplicated, assets in edge locations are typically much harder to safeguard. Automation provides a much simpler way to enforce that physical security.

A Back Channel
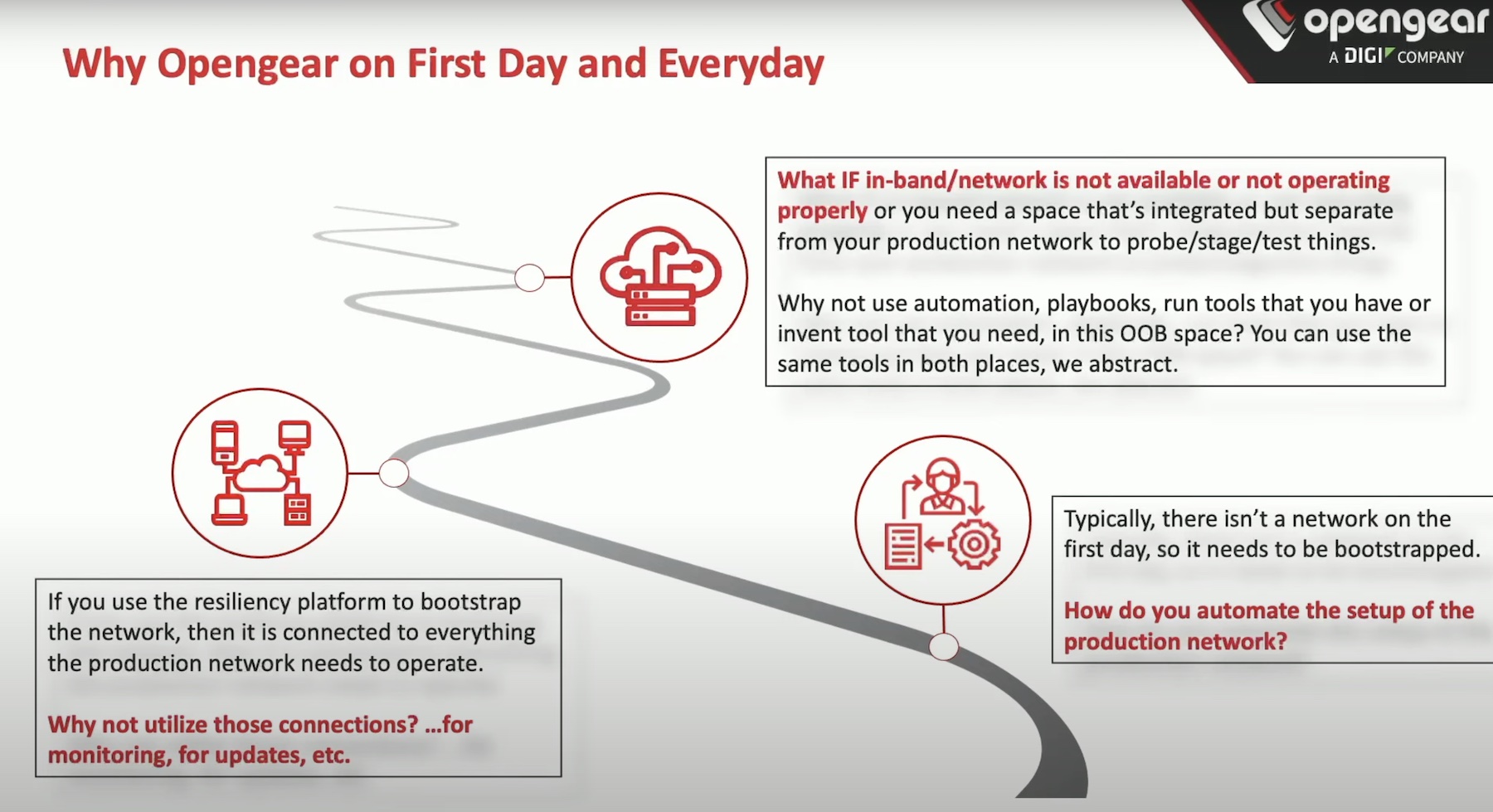
At some point, the discussion pivoted toward network security, which is equally important to attaining holistic security. But when the primary network goes down, and operators lose connection with field equipment, the risks shoot up. For those times, an out-of-band network is organizations’ best bet.
“Having a resilient platform, a solution that gives you the visibility even when your primary path is cut is an important factor in making sure that your environment, even at the distributed edge, even in New Zealand or on top of a windmill, is secured properly,” said Mr. Rampour.
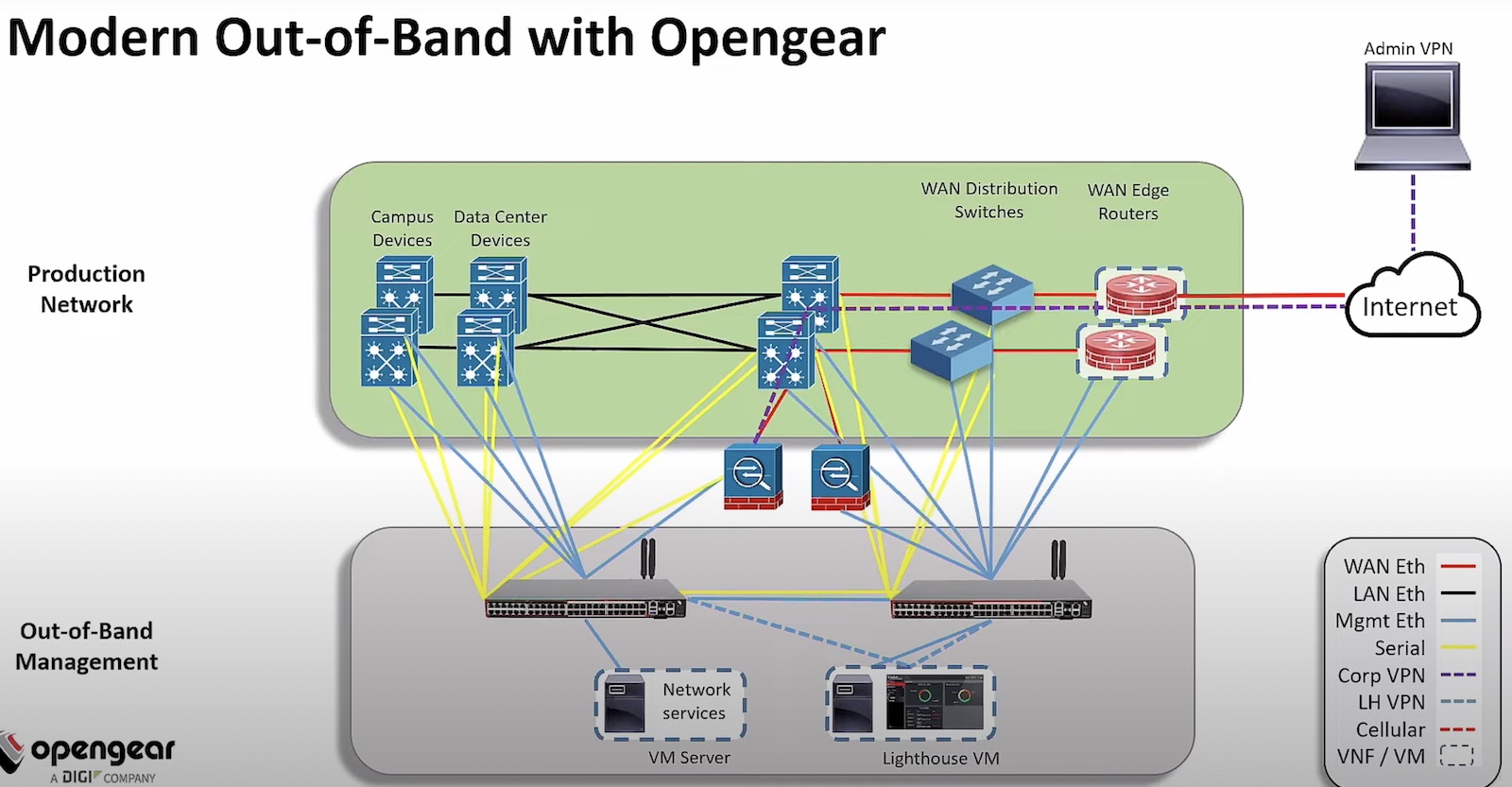
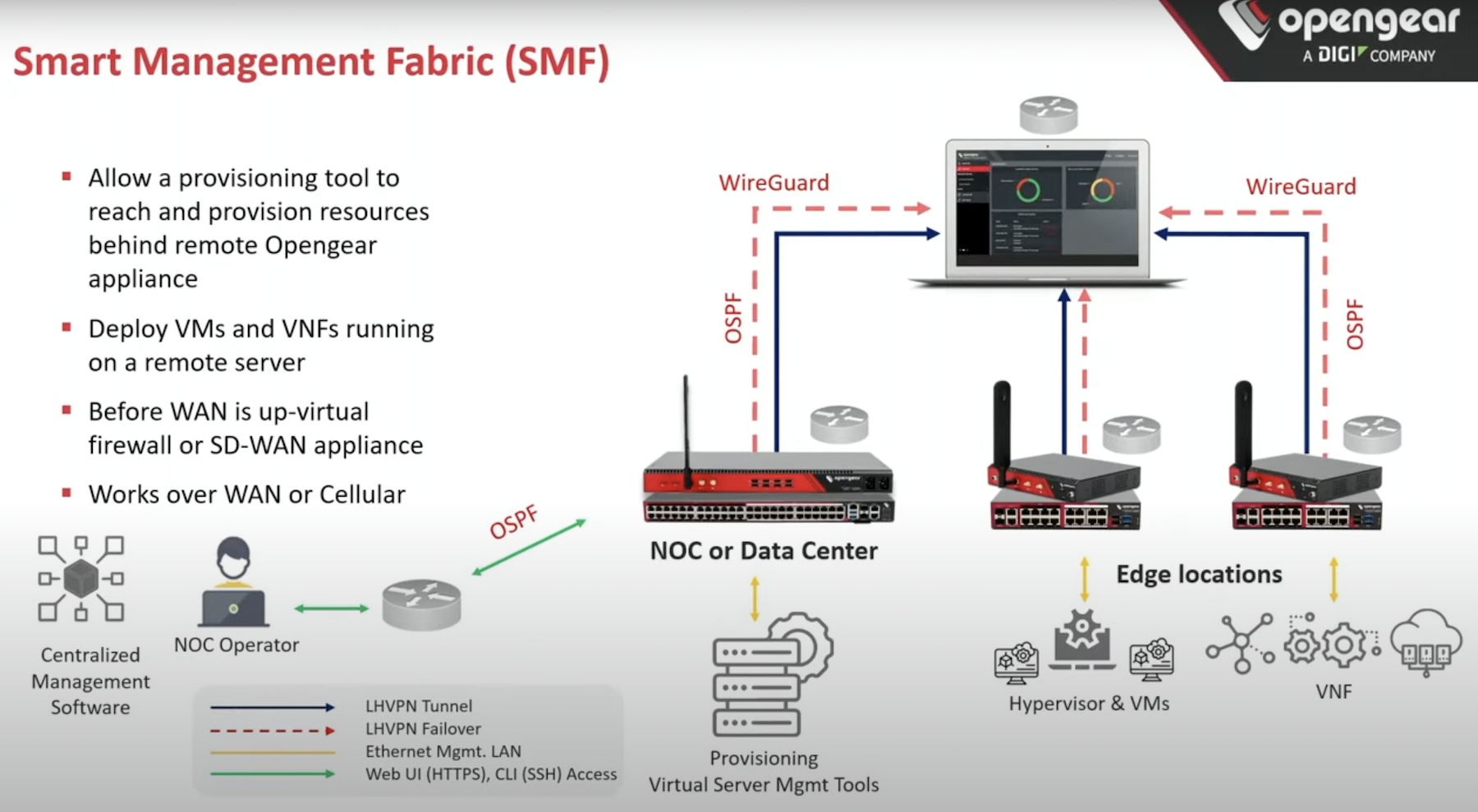
Opengear offers a Smart Out-of-Band Platform that provides secure access to physical devices for emergencies as well as every day. Separate from the in-band network, the solution provides a secure path of communication for deployment and lifecycle management of all devices installed in edge locations.
The Good and the Bad
Security too can be a two-edged sword if you don’t have complete control over it. A device that is fully locked down to prevent any tampering, is not a very intelligent solution if it does not offer itself up for manipulation to the users.
Mr. Vatte explained that security is complete only and only when it can be dynamically locked down and manipulated, depending on who’s trying to access and with what intent.
According to the panel, the edge requires systems to be secure by default, and to achieve that, security has to be top of the mind right from designing. Automation will make implementation of this at scale, but there should always be room for control so that the polices can be defined and redefined along the way.
The perfect security would be something that draws on the lessons of the past, includes the best practices the industry has come up with, and relies on models that provide a rock-solid starting point to a strong security posture. Thanks to automation, now there is a way to guarantee security for decentralized resources, even in the most disadvantageous locations. When that can be brought over to the edge, the edge will have the security it needs, and organizations will have a shot at living at the edge without worries.
Wrapping Up
The takeaway here as Mr. Warcop noted, is that companies can no longer afford to have security as an afterthought. With nonstop attack campaigns targeting businesses far and wide at the edge, the edge locations need extra fortification for which a solid foundation like Zero Trust can be vital. And thanks to automation, now there is a way to guarantee security for decentralized resources, even in the most disadvantageous locations. So, using automation to enforce that security across the board is simply good business sense.
Watch the Gestalt IT Roundtable Discussion with Opengear and ZEDEDA to learn more about this. Also check out the presentations by Opengear and ZEDEDA at the recent Edge Field Day event to know how they’re implementing automation in their solutions.
Today’s Roundtable Panel:
Panelists
Carl Fugate
Josh Warcop
ZEDEDA Panelist
Raghu Vatte, VP, Product Management and Customer Success at ZEDEDA. Connect with Raghu on LinkedIn, learn more about ZEDEDA on their website, and watch their presentations from Edge Field Day 1.
Opengear Panelist
Ramtin Rampour, Technical Marketing Engineer at Opengear. Connect with Ramtin on LinkedIn, learn more about Opengear on their website, and watch their presentations from Edge Field Day 1.
Moderator
Stephen Foskett