Enterprise networks are rapidly evolving. The networks I design today are very different from the networks I built just a few short years ago. I recently had the pleasure of discussing the convergence of networking and security with Nirav Shah, Vice President of Products and Solutions at Fortinet. Fortinet has a unique approach to converging networking and security, so I was excited to hear Nirav’s take.
Moving Beyond the Legacy Network Edge
As Nirav describes, the attack surface is expanding. Cyberattacks, including ransomware, are at an all-time high. Trends such digital transformation initiatives, remote work, and BYOD have been blurring the network edge for many years, and these trends were rapidly accelerated by the COVID-19 pandemic.
To support the growing needs of remote users, distributed apps, and an amorphous network edge, next generation network architectures are converging with network security solutions. However, navigating the landscape of these new solutions can seem like a game of buzz-word bingo with terms such as SD-WAN, SD-Branch, ZTNA, and SASE. In our discussion, Nirav explained in simple terms how Fortinet securely connects users to applications, regardless of location.
Securing Modern On-Premises Networks – FortiGate
Most readers have likely heard of FortiGate, Fortinet’s flagship security appliance. FortiGate is a next-gen firewall that supports all the security capabilities one would expect from a network firewall: IPS, AV, URL Filtering, and SSL inspection – as well as features unique to FortiGate, like in-line sandbox, HTTP3, and in-line CASB. FortiGate appliances also include built-in SD-WAN functionality and an LTE/5G WAN controller, modernizing the WAN edge without the need for additional network appliances.
Another feature that sets FortiGate apart is its ability to extend security policy to the LAN edge through deep integrations with Fortinet’s FortiSwitch and FortiAP product lines. Using a proprietary protocol called FortiLink, FortiGate acts as a controller to manage FortiSwitch and FortiAP devices. This creates a secure fabric that provides unparalleled security, intelligence, and visibility. FortiGate also provides basic network access control functionality through FortiLink NAC, which is included in FortiOS at no additional charge. NAC is an important part of any Zero Trust strategy, allowing organizations to dynamically assign security policy to endpoints based on identity and other criteria. FortiGate is available as hardware appliance as well as virtual machine, providing the flexibility to secure both on-premises applications as well as cloud apps.
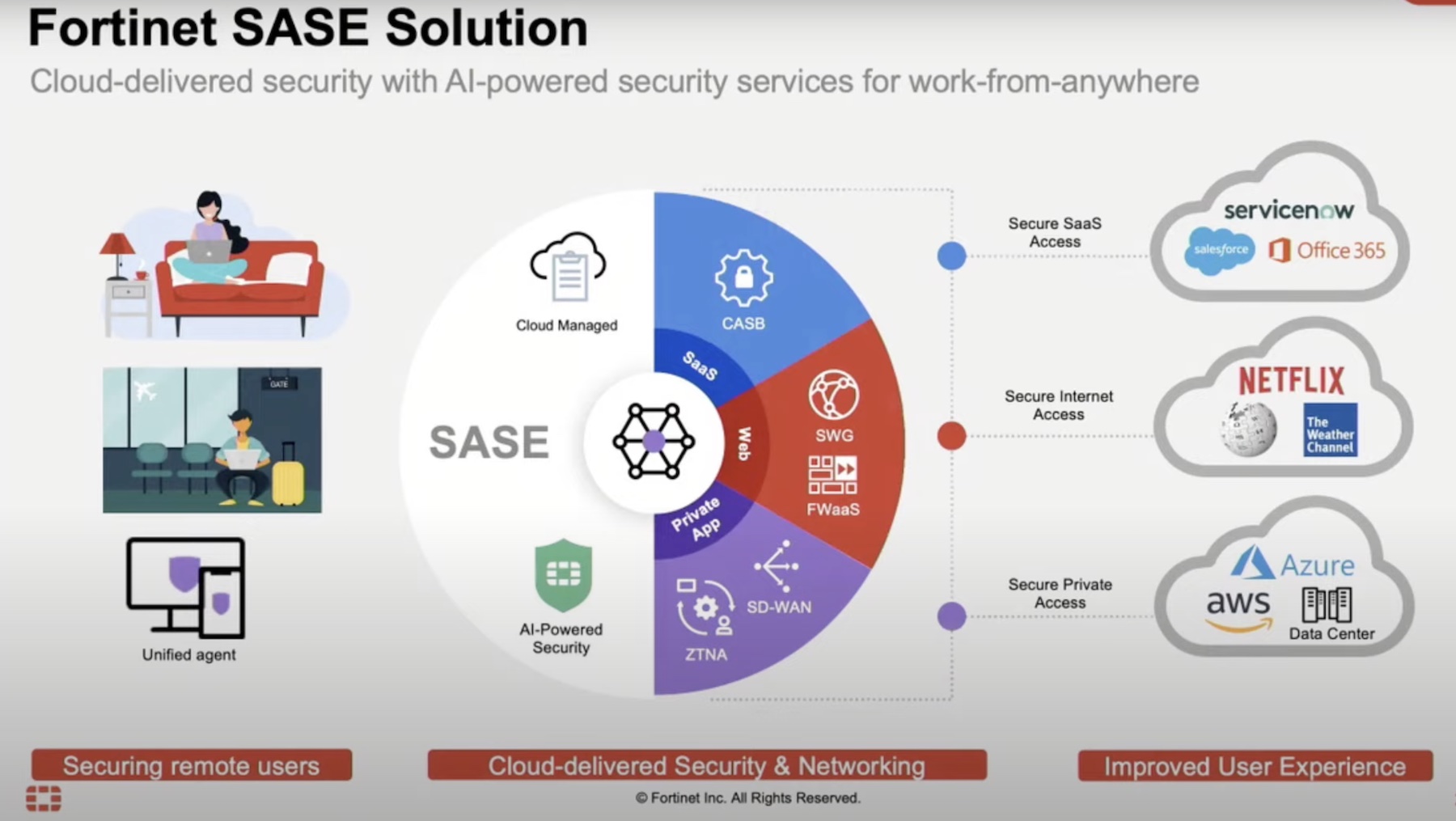
Securing Distributed Remote Users – FortiSASE
However, how do we secure remote users? In a traditional network design, remote users connect to an on-premises remote access VPN device or SWG appliance to access applications. This is a logical design for a regional workforce accessing apps in a local data center, but today’s networks often look very different – distributed teams access a variety of apps that may reside in a number of locations: on-premises data centers, SaaS, PaaS, IaaS, etc. Scaling traditional remote access infrastructure to support distributed users and applications necessitates regional POPs and network hubs, which few organizations have the resources to maintain.
This is the problem FortiSASE was designed to solve – securely connecting remote users to the Internet as well as private applications. FortiSASE, built on the same FortiOS and FortiGuard security services used by FortiGate appliances, provides network security capabilities in a cloud-delivered SaaS platform. Using the FortiClient Agent or going agentless with Explicit Proxy, remote users connect directly to their application through FortiSASE, without the need to route traffic through an on-premises FortiGate appliance. Instead, FortiClient automatically selects the closest FortiSASE POP, minimizing application latency. From there, security policy can be applied directly in the cloud – FWaaS, DNS security, IPS, DLP, SWG, ZTNA/VPN, as well as sandboxing.
Final Thoughts
Modern network security can be complex. While a multi-vendor security strategy is still valid, piecing together a network with SD-WAN, SD-Branch, ZTNA, and SASE solutions from multiple vendors may be ill-advised. Fortinet offers a deeply integrated network security solution that secures the network from edge to access, converging networking and security both on-premises and in the cloud. In today’s interconnected world, it is critical to secure the network; Fortinet should be on the shortlist for any organization looking to modernize their network security architecture.
Guest
Nirav Shah, Vice President of Products at Fortinet
Moderator
Matt Haedo
Follow us on Twitter and SUBSCRIBE to our newsletter for more great coverage right in your inbox.