Edge computing architectures are increasingly mirroring the paradigms that became popular in the era of cloud computing. This is good news for application builders.
While similar in many ways, edge environments are also very different from their cloud counterparts. They often face far more constraints, such as the lack of on-site technical staff, challenging environmental factors like hot temperatures or poor physical security, and unreliable network connections.
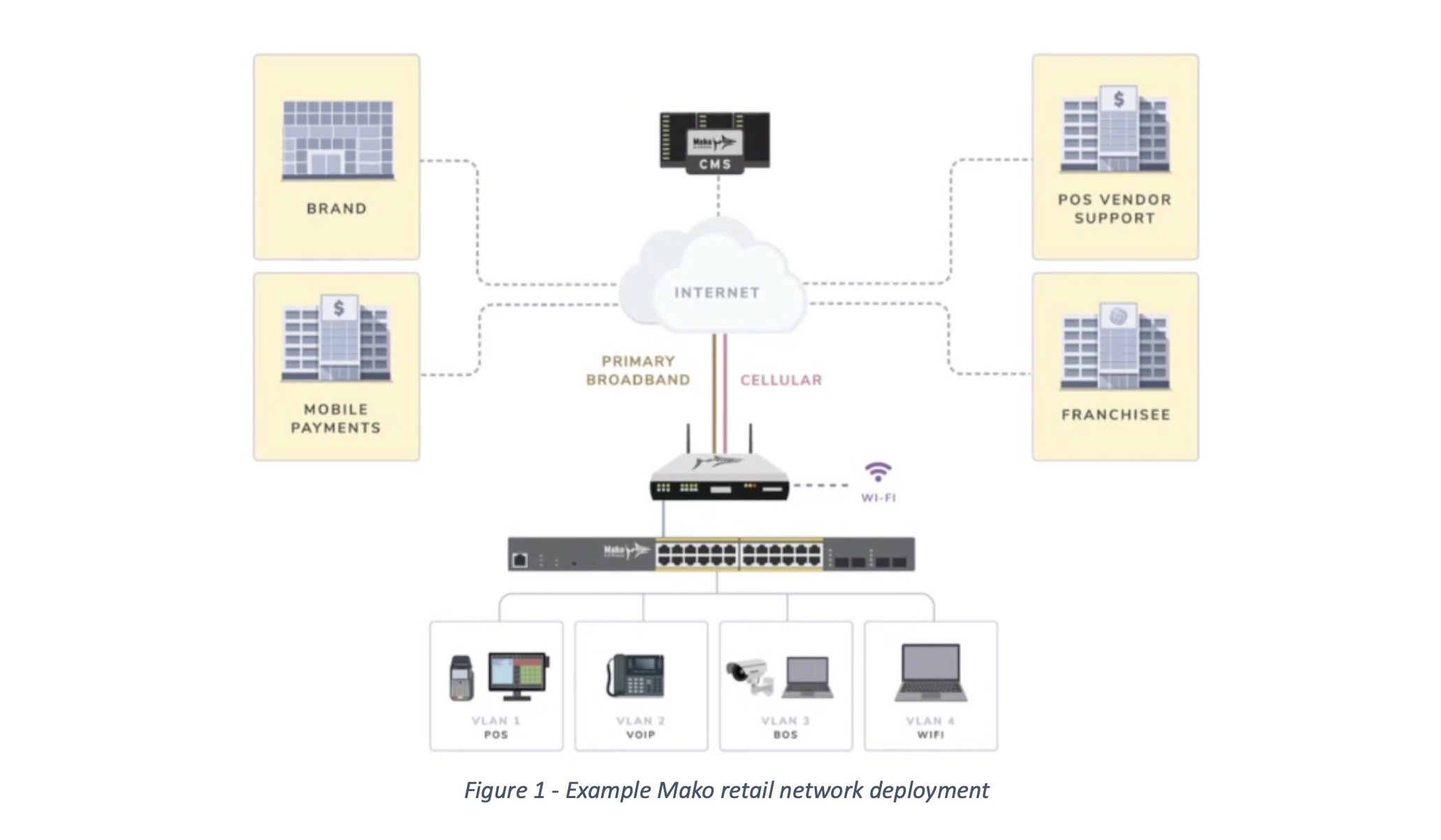
Discussions on edge tend to focus only on applications, their scheduling and orchestration, and the underlying compute infrastructures that enable them. Seldom do they talk about the local network that enables this infrastructure. Truth is most organizations doing edge solutions, including my own at Chick-fil-A, are investing heavily in the resiliency of their Local Area Network (LAN). This holds true in other industries such as, oil and gas and manufacturing.
In a recent episode of the Utilizing Edge Podcast with Simon Gamble, President and Co-Founder of Mako Networks, we explored this dynamic.
Simon pointed out that one of the key elements of successful edge network deployment is segmentation. Network segmentation is a network design practice that involves dividing a computer network into multiple smaller network zones with appropriate levels of security for each zone. These network segments can be categorized and managed separately, leading to numerous benefits including improved performance, enhanced security, and better network traffic management. This is their bread and butter at Mako Networks.
Edge in Retail
Retail is a great context within which to explore the importance of network segmentation. In edge retail scenarios, the LAN is critical. If it is compromised or has poor availability, the potential benefits of edge computing architectures can evaporate rapidly.
To mitigate these risks, companies running edge architectures must design their network stacks for high availability, and consider implementing a robust segmentation strategy. Consider a restaurant chain that leverages a franchise business model: they have critical operational dependencies on their network for items such as point-of-sale (POS) or credit card processing that require high degrees of management and potentially regulatory certifications such as PCI.
These same businesses may also have lower trust environments that are still managed but need to be carved off from the operationally critical subnet. An example of where this may apply is with lower trust but operationally useful clients, such as internet of things (IOT) devices.
Retail franchisees likely also offer customer Wi-Fi which has no business being anywhere close to an operationally critical network segment.
The concept of segmentation can also be carried beyond a local network to edge compute workloads where isolation is important as well. Segmentation plays a critical role in eliminating lateral move attack vectors in a multi-tenant compute environment. Constructs like namespaces in Kubernetes, Web Assembly (WASM) runtimes, or network subnets and their associated rules and policies can create barriers to these moves.
All these concerns are amplified when a service provider – perhaps a corporate franchisor – provides services to a franchisee that has a degree of control over the technology they deploy in their retail locations. Consider the grocery store that provides technology services both for themselves and to a pharmacy tenant. These two separate businesses need traffic and workload isolation and cannot be muddled together.
Finally, segmentation can be an engine of innovation by carving off safe places for a franchisee to innovate, bring their own devices, and explore new solutions that may benefit their businesses. In all these cases, reliable segmentation of network and compute workloads is essential.
Conclusion
Segmentation is key to operating edge environments at scale. While all these constructs are simple to understand and easy to implement in a cloud-native environment, they are far more challenging to do at a scale of thousands to tens of thousands of discreet edge footprints. Segmentation, done well, is transparent to its beneficiaries, and reduces the security risks and attack vectors a business may face. By segmenting workloads effectively, both at a network and compute layer, edge deployments have a much higher likelihood of successful launch and long-term management, and can become engines of innovation and simplification, instead of management burdens and drivers of complexity. Finding a capable partner that can effectively provide these services is critical to successful implementation of an edge computing solution.
To find out more about Mako Networks, you can visit their website or watch their presentations from Edge Field Day 1. You can also watch or listen to Utilizing Edge in which President and Co-Founder of Mako Networks Simon Gamble appeared on as a guest.