As companies move to secure their digital estates from ransomware attacks leveraging zero trust architectures and defense-in-depth strategies, one asset looms larger than most – data. But in the fight against ransomware, focusing solely on data recovery is a losing game. The question one should be asking is whether to use an identity-centric solution, or a data-centric one?
With RackTop BrickStor, we can confidently say both.
Indentity-Centric or Data-Centric Security?
The move to cloud-native applications, distributed teams, and unmanaged user devices has created a world of deperimeterization where IT estates span networks, devices, applications, data, and users across multiple platforms. These platforms are often built on infrastructures that companies neither own nor completely control.
If, perchance, they do control the infrastructure, they don’t always control the access that employees, partners, and customers have to resources over the internet.
The facts of deperimeterization have led to widespread acceptance of the need for zero trust architectures, such as described in NIST SP 800-207. Zero trust is a concept that moves us from providing implicit trust based on network boundaries (a secure perimeter) to a least-privilege model focused on explicit authentication and authorization of both subject and resource. This need for discrete authentication and authorization brings an obvious focus on identity.
Identity-centric security is a popular response to the demands of a zero trust architecture. It includes not only the identity of human users, but also that of data, devices, networks, workloads, and the interactions between all of them. Identity-centric security typically expands the traditional “triple-A” of authentication, authorization, and accounting, to include access policies and auditing capabilities.
But what is it actually trying to protect? In many cases, the most valuable assets being secured are various types of data. This has led to the emergence of data-centric security.
According to Wikipedia, data-centric security is “an approach to security that emphasizes the dependability of the data itself rather than the security of networks, servers, or applications.” Users/accounts also belong to that list. And it typically adds encryption and digital rights management to the conversation around zero trust architectures.
Why Not Choose Both?
What if companies could have both identity and data-centric security? Enter RackTop Systems, and their active security platform.
RackTop Systems is a leader in the emerging “cyberstorage” market. Founded in 2010, they have a team of U.S. Intelligence Community veterans and engineers that are the brains behind their signature product, BrickStor SP.
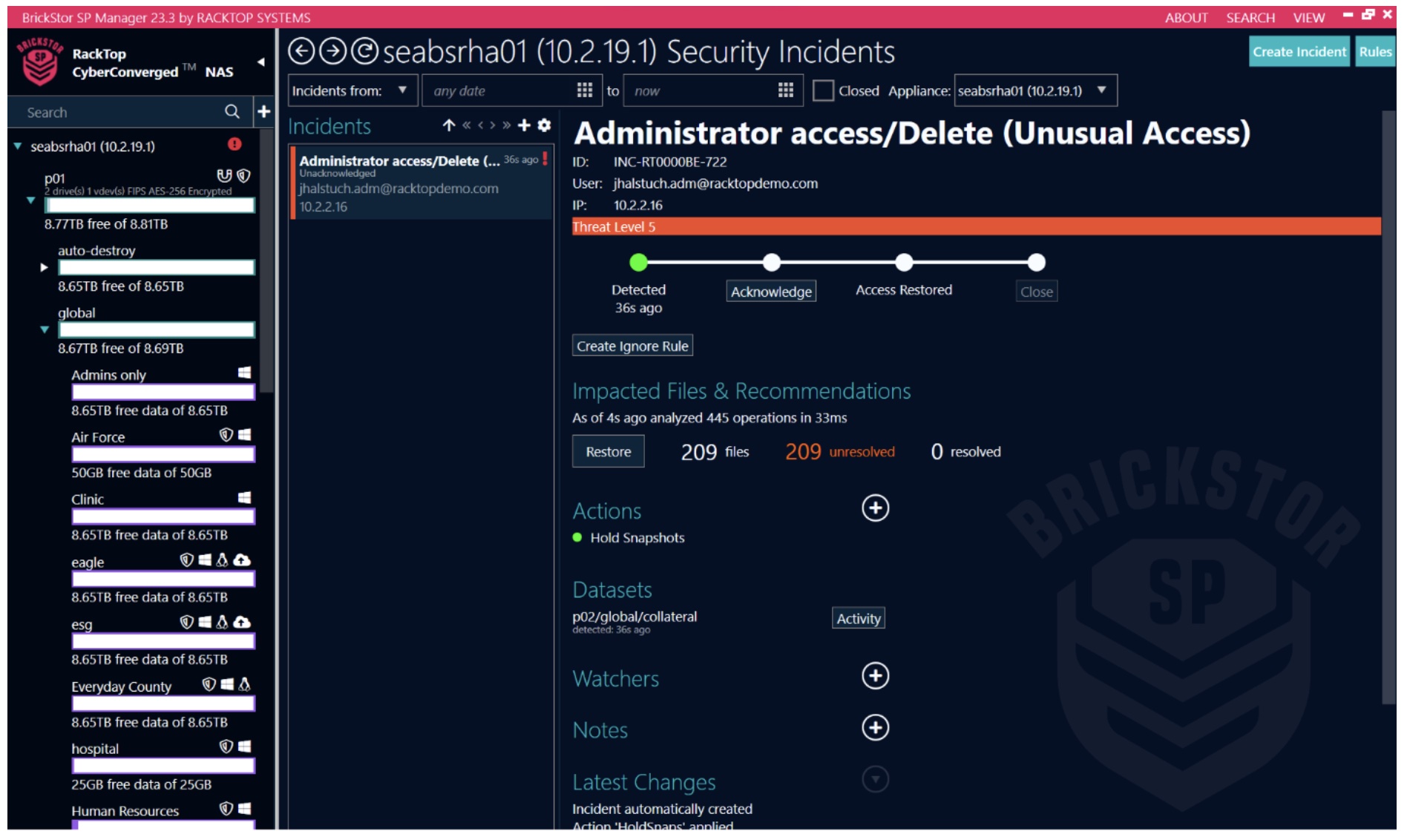
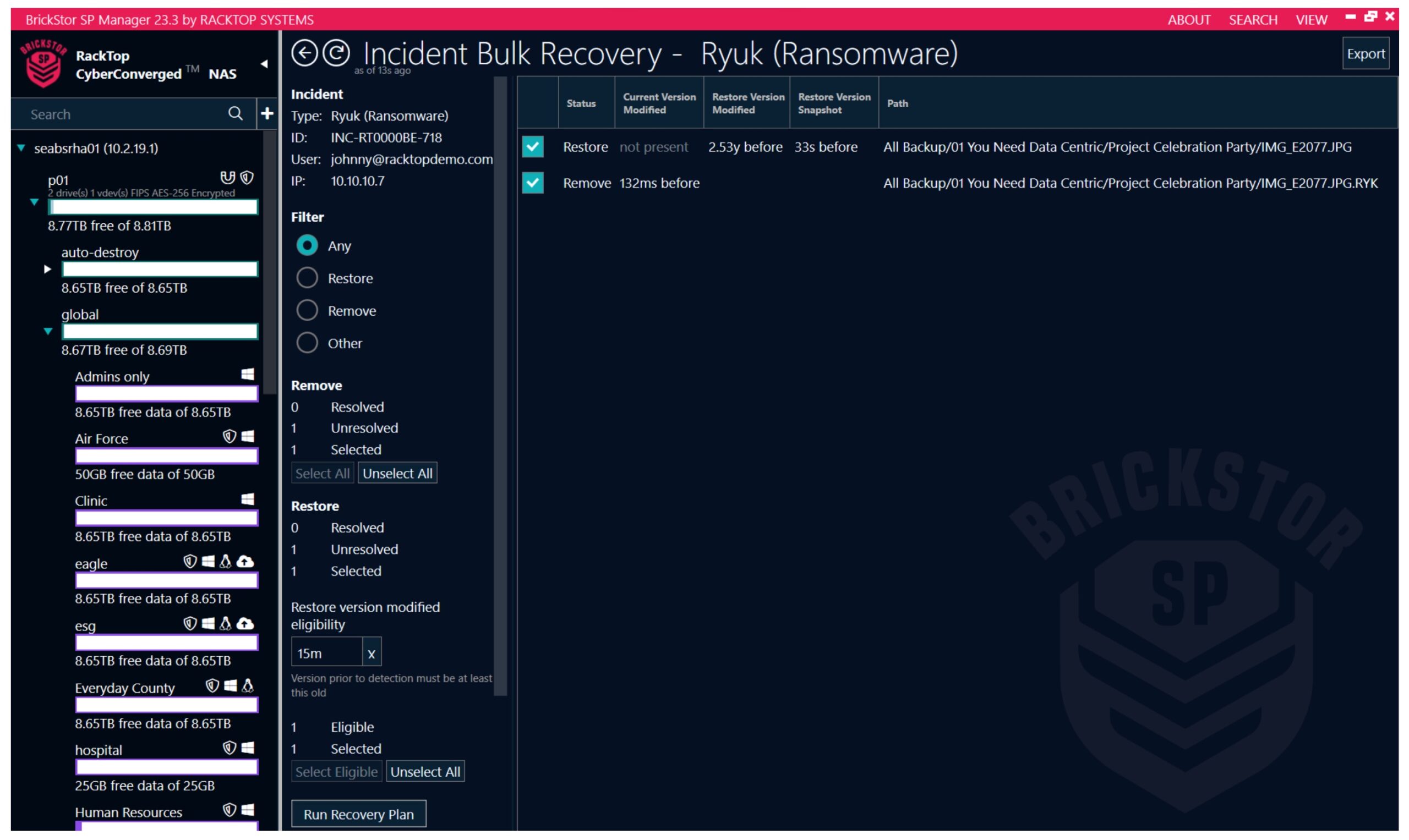
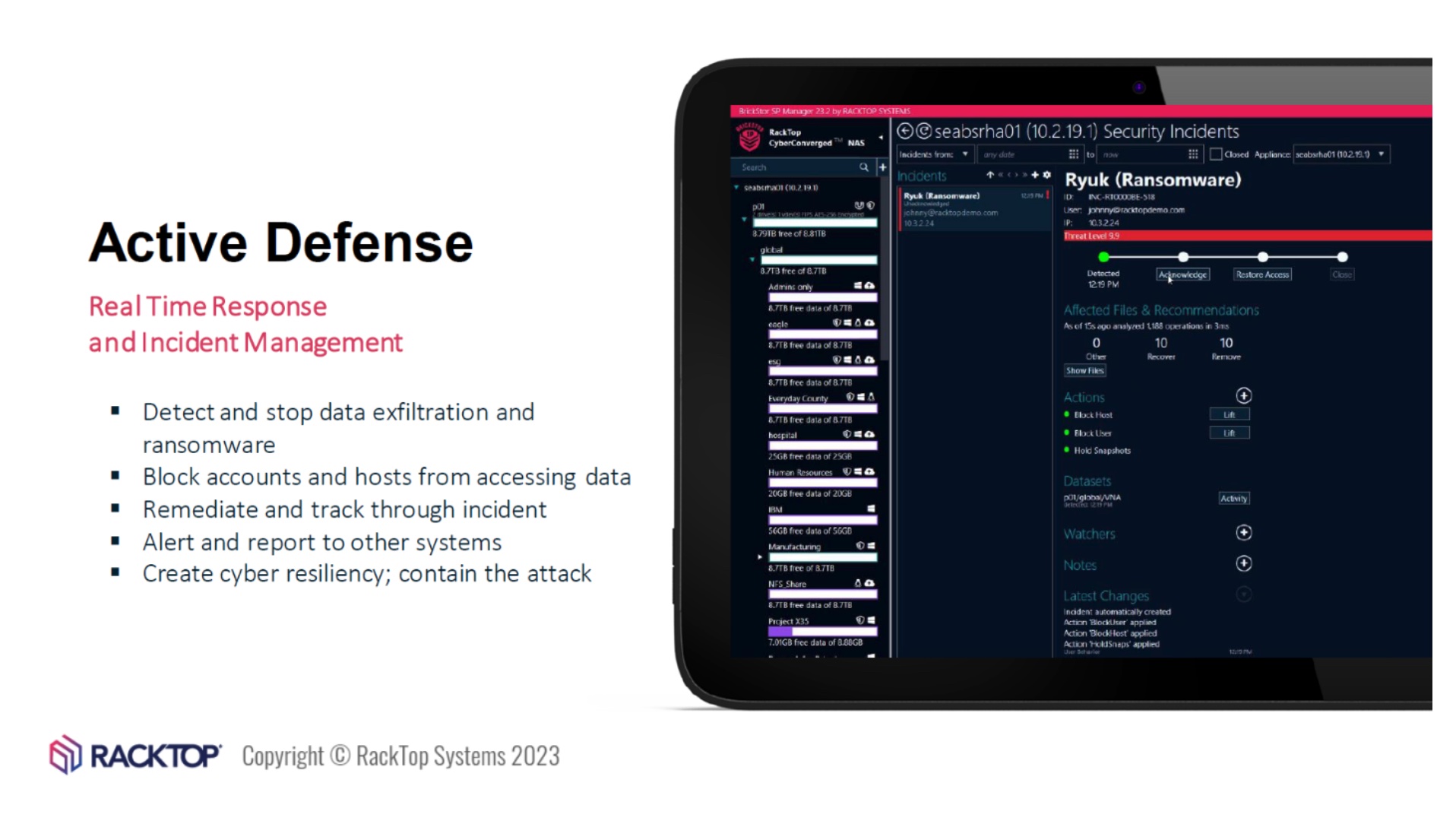
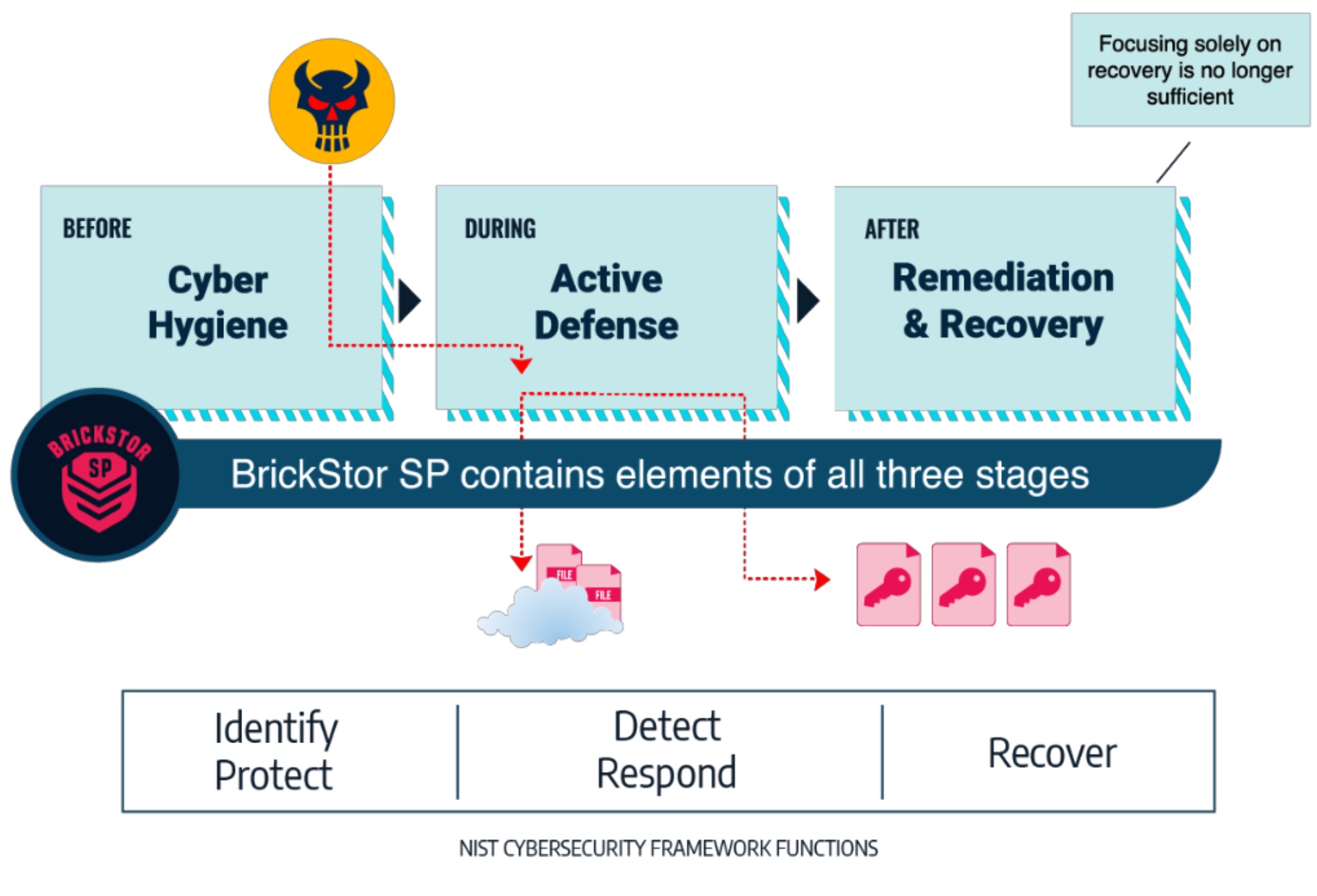
RackTop describes BrickStor as an “active security platform for unstructured data” and claims it to be the only cyberstorage solution that addresses all five functional areas of the NIST Cybersecurity Framework, namely, identify, protect, detect, respond, and recover.
Cyberstorage is in many ways a direct response by the IT community to the seemingly overwhelming threat of ransomware and more recently, extortionware. Cyberstorage techniques also guard against the age-old “insider” threats of data exfiltration and destruction.
How does RackTop do cyberstorage? I recently joined a Tech Field Day Showcase to find out.
BrickStor Cyberstorage
BrickStor provides an excellent combination of data-centric and identity-centric security technologies to implement a zero trust architecture for defending unstructured data. It leverages encryption – FIPS AES-256 to be exact – and does not require any additional products to manage keys including policy-based key rotation and auditing.
A recently published technical validation paper from Enterprise Strategy Group says that “the RackTop software-defined data storage solution demonstrates robust proactive data security capabilities in an all-in-one Cyberstorage package that is easy to use.”
Even more exciting is the combination of UEBA (user and entity behavior analysis) and SOAR (security orchestration automation and response) capabilities that are purpose-built around the realities of securing data.
With its well-tuned, out-of-the-box policies, BrickStor can start protecting the most valuable data right from day 1. To see this in action, check out this live demo.
The Bottom Line
In order to secure organizations against the complex and evolving threats, a zero trust architecture that is both identity-centric and data-centric is critical. Luckily, RackTop Systems has done all the heavy-lifting by embedding these techniques and technologies into their BrickStor cyberstorage platform, bringing to customers a ready-to-use solution.
Watch the video from the RackTop Showcase on the Tech Field Day website for more information.