I would like to take you on a journey through the transitions we’ve gone through in the realm of security over the years. This journey will also highlight how microsegmentation has truly changed, while largely staying the same.

Microsegmentation is not something new. This is something that enterprises and large businesses have been leveraging to great success for decades. The problem is, it all started before virtualization was the new kid on the block (yes, I mean x86 virtualization).
It began in the days of physical servers, often isolated and physical switches and numerous physical firewall devices.
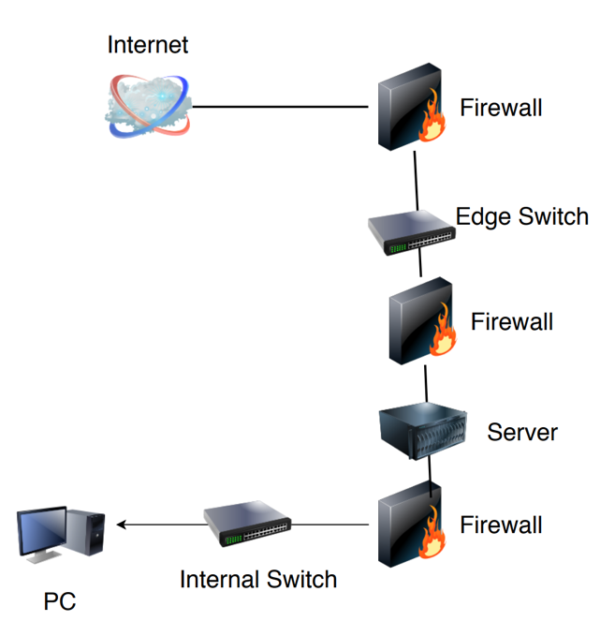
As you can see in the example, there are a few devices in this network. Often, each of the firewalls was from a different vendor. VLANs are in play, but the key principle in use is each device has a port, and each port is distinct and unique.
The limitations were multi-fold, such that we were bound by the constraints of the number of ports available. The sheer volume of devices often used to protect a single workload was immense. More devices were thrown between the bottom two firewalls into the Server stack area, while still segmenting this portion from the network, effectively DMZ’ing things. Adjacent server devices would then be able to communicate with each other when they’re on the same VLAN. This was usually done to increase performance or save money on hardware but often turned into a bigger threat in the long run.
At times, firewall policies were established, such as “192.168.1.2 cannot talk to 192.168.1.3 without passing through this firewall rule.” Their heart was in the right place, but the technology didn’t back it up. That’s because adjacent devices on the same VLAN need not pass through their gateway (firewall) to communicate. This was security theater in action!
So, at this point, I know what you’re thinking: With the advent of virtualization, things became better and we were able to better protect workloads, right?!
No. Not exactly.
For the better part of a decade, virtualization actually made things worse.
Why?
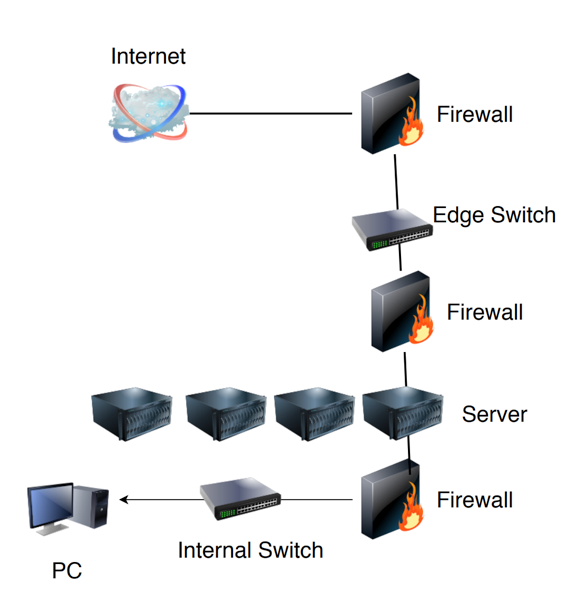
Because people were implementing virtualization in fundamentally the same way as it is seen in the second image, or even worse, where there are no firewalls in play aside from an edge firewall facing the Internet. This lack of segmentation from the Campus, from the Core, from the machines themselves, introduced the perfect storm of threats which have gone on to plague us for the past few decades. Ransomware, Active Malware, Adaptive Persistent Threats (APTs), the list sadly goes on. Due to some confusion in the marketplace and conflicts between Ops and Security teams as to enforcement mechanisms surrounding using things like Windows Firewall and iptables for Linux.
What this gave us was years of unprecedented breaches, compromises of information, personally identifiable information (PII) and IP theft, that for operational reasons “couldn’t” be resolved. This helped the creation of what would come to be known as modern-day VMware NSX!
In 2012, when VMware acquired Nicira to turn it into NSX, it was one of the more exciting days in my life because I knew the future would be bright and protected. At least we would get there, once Software Defined Networking and protection would be embraced in the datacenter. I had been preaching it and now it seemed many were embracing it.
Finally, VMs went from adjacent neighbors with full access to being segmented from each other even when they’re in the same Virtual Server, in the same VLANs, and the same Virtual Switches. Finally, we could black box our virtual machines while still allowing them to interact with each other and the business, but also protecting them from themselves effectively.
It was not perfect at first. You still needed gateways to interact with other parts of the networks, physical devices, and clouds and so on, but it was the start of the missing piece of the puzzle which could bring about our success, safety, and protection.

Fast forward a few years and the present is quite bright indeed. Now NSX has expanded its footprint to include public clouds, bare metal, partners, users, and even containers!
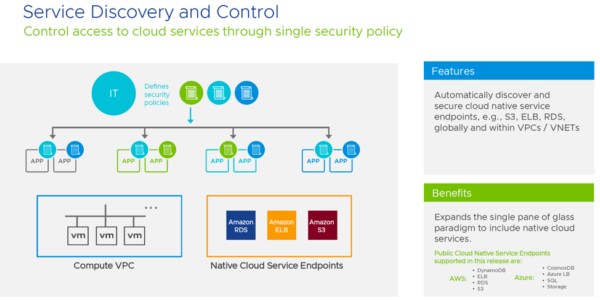
Service discovery and control, which will be an integral piece of cloud and native security postures, entered the scene and provided visibility for network and security controls. If you consider how many adjacent or service endpoint compromises you have seen in the last year alone, this improvement will provide significant value to the enterprise as a whole.
As Kubernetes is starting to make major waves into the datacenter, having a multiple namespace or tenant approach adds as a huge differentiator to how security in Kubernetes is being done today. (Spoiler alert: It’s not being done.)
Model 1 provides for a Dedicated Tenant Router per Kubernetes Namespace.
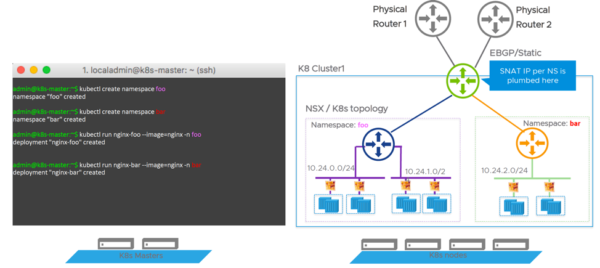
While Model 2 provides for a Shared T1 Router for all Namespaces in a Kubernetes Cluster.
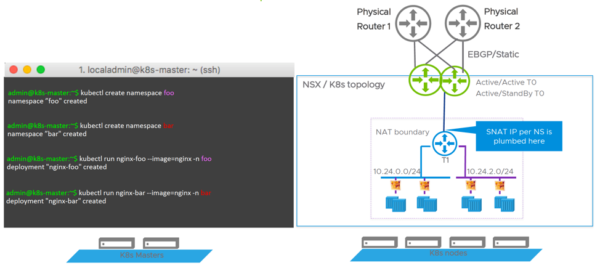
Now in all of this excitement you might be thinking, this completely eliminates the need to use firewalls in your Virtual Datacenter environment! And you would be right… almost.
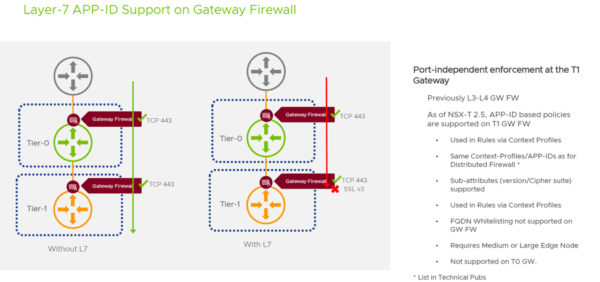
Firewalls may no longer be used, and instead, you’ll find yourself adopting Internal Firewalls and Software-Defined Firewalls as a natural part of your intrinsic security story. I’m happy to report that NSX and NSX-T continue to grow in their functioning, protection, and security mechanisms. They operate as a decent firewall service, with some growing and mature advanced security concepts – things like FQDN filtering, blacklisting, contextual rules, FIPS 140-2 compliance status reports and even Layer 7 APP-ID support.
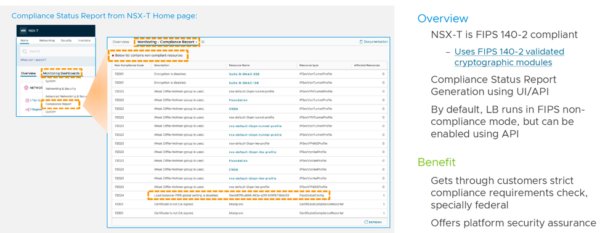
But what this doesn’t replace and fortunately supports and integrates with, is the diverse and dedicated Alliance and Partner ecosystem for service inspection, insertion, analysis, off-loading and more. Many of the partners you leverage to protect your business today like Trend Micro, Palo Alto, Checkpoint and Fortinet continue to invest in and develop amazing security products and security intelligence they continue to roll into the capabilities of their products.

This introspection and insertion isn’t attempted to be replicated or even duplicated but instead leverage the existing investments so they can focus on what they do best while partners can focus on what they do best — which is provide comprehensive and intrinsic security that expands beyond just the packet, and into the content of the packet, the intent of the packet, and so on.
What this means is not only can we isolate and micro-segment virtual machines within the hosts, and isolate what ports devices can talk to each other on, but through these partnerships, we can protect what kind of communication can occur to the ports within the devices. Because allowing traffic to SSL Port 443 is a lot different than allowing traffic to that port but while also blocking known bad requests over that Port and Protocol.
Hopefully, you enjoyed this journey into VMware NSX, microsegmentation and you see the approach and modernization that is being adopted to make the future of security and our datacenters as one that is paired together versus isolated into silos as in the past few decades. The future is a bright, secure one we can all embrace.