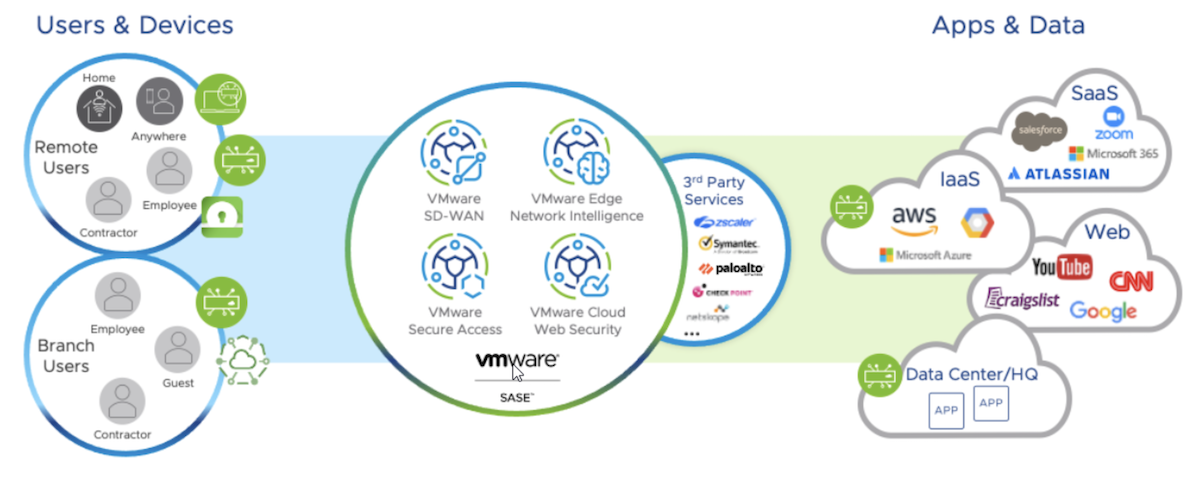
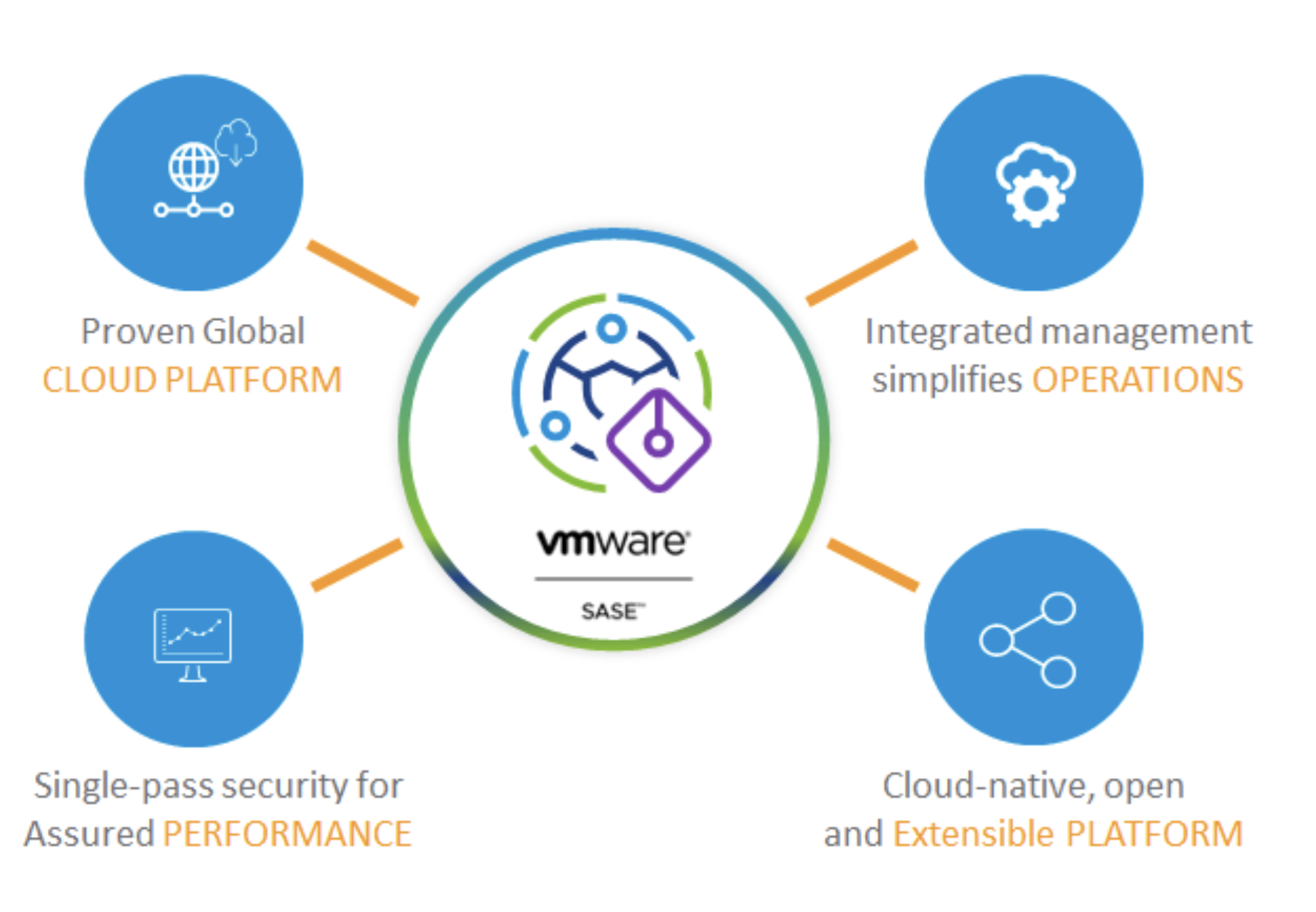
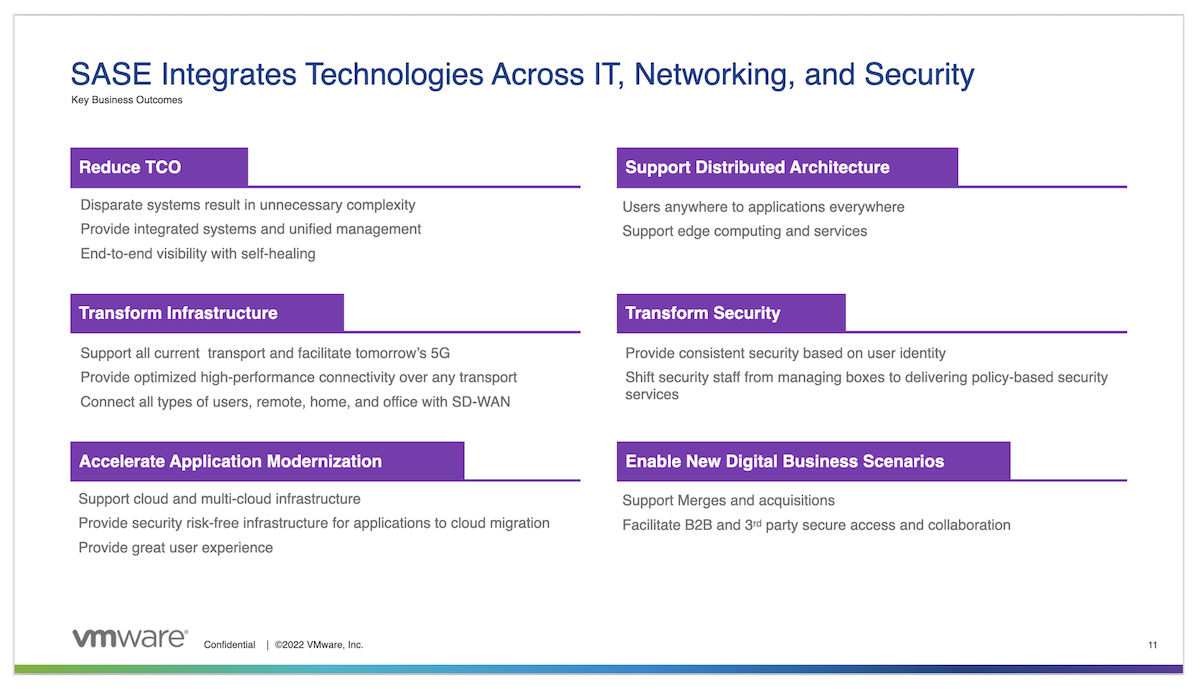
Secure Access Service Edge (SASE) has rapidly taken the networking and security markets by storm. It was only a couple of years ago that the term was even coined, but you wouldn’t know it by how pervasive it has become in such a short span of time. In fact, the only new tech in the networking and security space that has emerged as rapidly was SD-WAN, but that said, SASE seems to be making waves even more quickly. Like many nascent technologies with quick adoption, the reason for the rapid uptake is overwhelming market demand for the functionality it brings. The COVID-19 pandemic catalyzed the need for much of what SASE has to offer to the world of connectivity. Let’s explore why that’s true and what we get with SASE.
Secure Remote User Access
The biggest challenge for IT teams in the past couple of years has been the difficult adaptation of connectivity within a new majority work from home (WFH) or work from anywhere (WFA) context. Instead of managing most users in the office and just a few outside of the office, things flipped during the pandemic to suit the majority of users outside of the office. With this shift comes a need to secure user access to applications without the luxury of some type of “middle box” security network appliance approach that organizations took for granted.
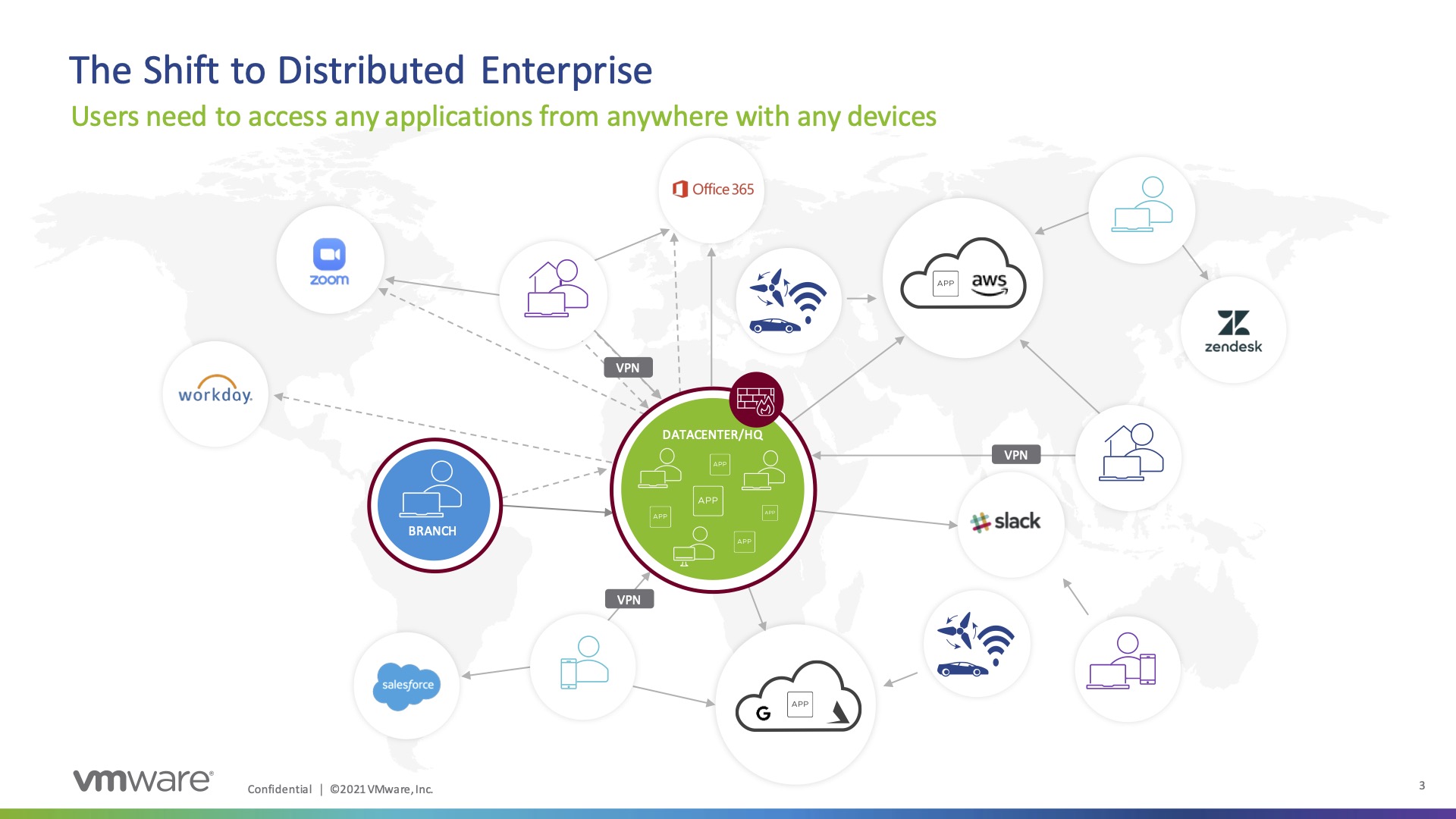
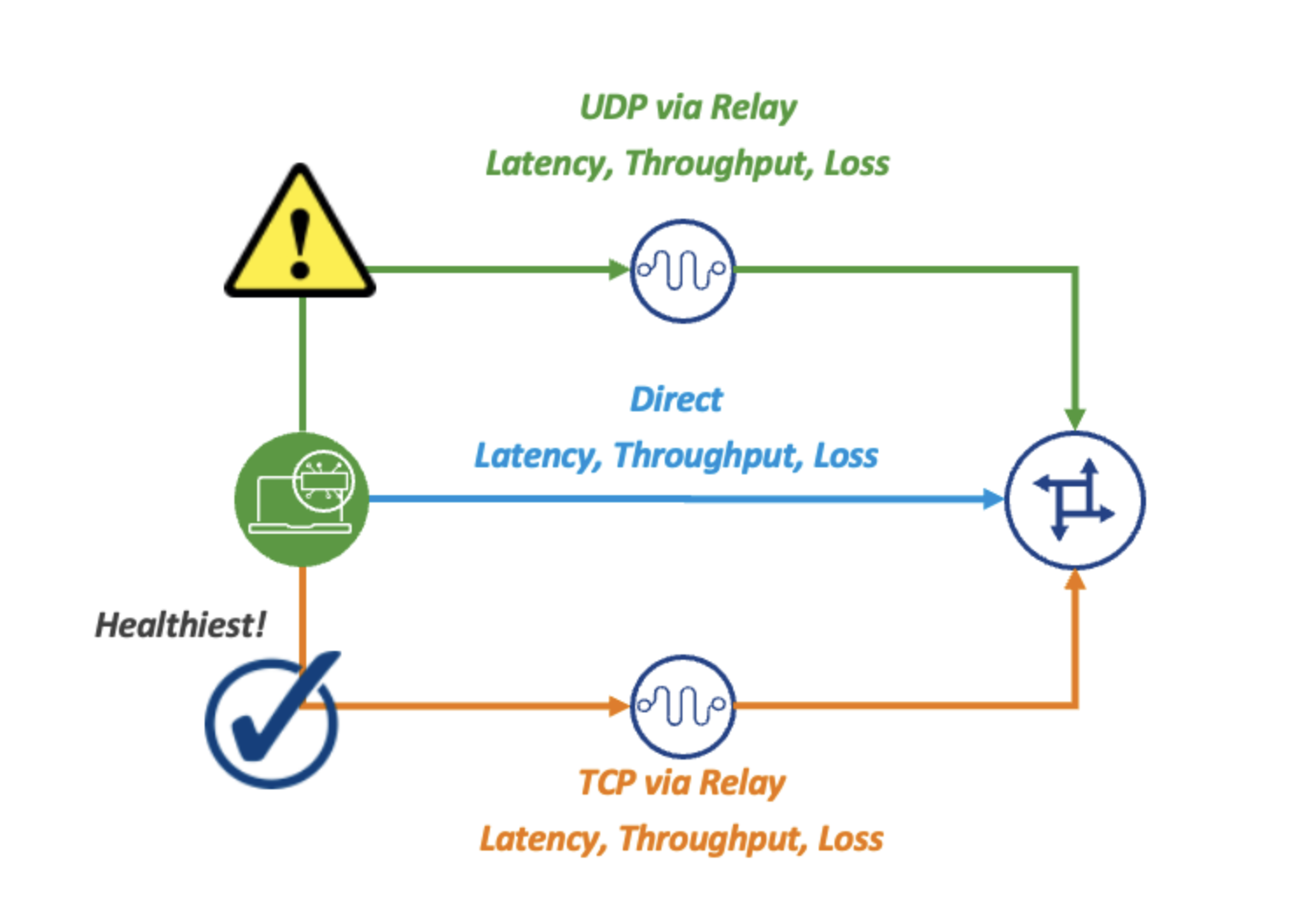
SASE accounts for this by leveraging VPN backhaul to securely access application resources via cloud security infrastructure which can inspect, block, and log threats in the cloud instead of through a network appliance in the branch or datacenter. This affords a similar secure connectivity experience that users might enjoy in the branch, but instead is accessed via globally distributed gateways, leveraging the closest one to the user. This approach also allows the user to access resources in the most efficient way possible and reduces latency as it improves security.
Zero Trust Everywhere
Another key component to SASE is how it leverages Zero-Trust Network Access (ZTNA) models. Traditionally, network access was secured for most organizations at the perimeter firewall in headquarters or within the datacenter. Now with services and applications existing across the hybrid cloud, not to mention users working from the office and from home, the new network perimeter is everywhere. The security boundary now needs to be extended as close to the user as possible, no matter where they are. Context-based security is the new norm and it is typically based on factors such as user identity, group, and device to allow appropriate access for users to applications and services they are authorized to use. Consistency of user experience and corporate security policy, no matter how the user connects, is very important.
Extensibility is Key
An often-overlooked facet to the SASE story is extensibility. It’s important to embrace a truly modular architecture with the ability to build custom policy and snap-in additional security attributes which fit the needs of the business. The most robust platforms are built from the ground up, acknowledging that every organization is in a different stage of its security journey and will have changing needs over time. Another part of this is strong partner relationships to allow for flexible integration with other vendors’ platforms. This allows one to get the most out of previous investments and be able to use functionality not built into the native solution.
The SASE Crystal Ball
There is no doubt that SASE is the future of secure enterprise connectivity. The hybrid nature of applications strewn across datacenter, IaaS & SaaS requires a fresh look at how users connect. Though the COVID-19 pandemic ushered the rapid change and shrunk the time horizon from 5 or 6 years to 1 or 2 years, the distributed workforce, and therefore, the SASE model to secure that workforce, is here to stay. The need to adopt SASE in some way, shape, or form is inevitable for nearly every organization from here on out.
Learn more about what SASE has to offer by checking out this Gestalt IT Showcase, brought to you by VMware: