When Gartner coined the term Secure Access Service Edge, or SASE (pronounced Sassy) in 2019, little did anyone understand how quickly the enterprise landscape would change. COVID-19, acting as a catalyst, forced many businesses to change how and where their employees worked and accessed resources. Whole call centers were displaced, employees relegated to apartments and homes around the world, all with different ISPs, vendor hardware, and security postures. The high-speed bandwidth at the corporate office and traditional defenses surrounding the data center perimeter could no longer be relied upon to protect the employees, assets, or data.
What is SASE?
Enter, SASE solutions: Some were built by bolting on new software to existing ideas or products, and others built from the ground up with a cloud-native approach. This is an approach that builds and runs applications and exploits the advantages of the cloud computing delivery model. Removing the legacy data center-centric approach— where all users are homed back to the data center’s network, security, and firewall stack— means that local app traffic would be routed in the data center while pushing SaaS or public cloud data back out to the internet. Removing this hair pinning of traffic and moving of data twice no longer caused it to take longer or travel further to reach the resource. Even those mitigating or accepting the risks of split tunneling know that security policy compliance on those endpoints is not always absolute.
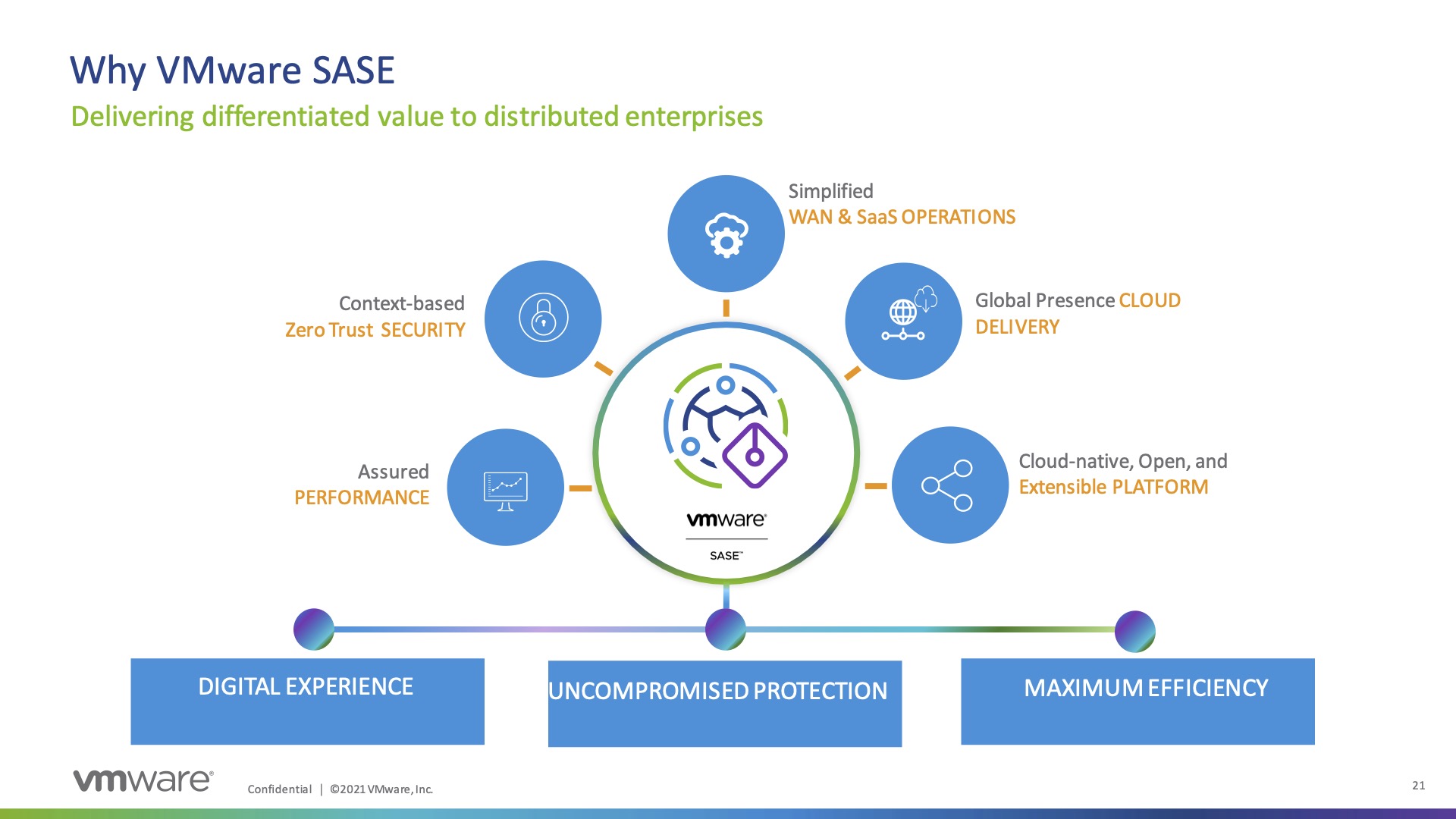
Using VMware’s SASE solution and moving the network and security stack to the cloud leverages the VMware Partner Points of Presence (PoP) worldwide, which provide a latency under 10ms from the majority of the population, and under 5ms from all major cloud service providers. Moving the stack closer to the user also abstracts out the network link management and QoS of applications by leveraging VMware’s SD-WAN backbone and better connectivity to cloud partners.
Why is SASE Important?
Cloud Web Security provides the ability to orchestrate the control of your service’s edge from one interface and use the same security policies. This allows any user, from any device, to connect into VMware’s SASE using context-based, zero-trust security to know where the user is from, what device is connecting, and what they are trying to do. SASE then feeds that into policies that determine what network and security services should be received for that application flow.
The decryption of SSL/TLS traffic for inspection allows implementing URL filtering to protect users against websites spreading malware, information stealing, or inappropriate content. While anti-malware sandboxing protects against known and zero-day threats, remote browser isolation protects the users against browser-based attacks and protects web applications from malicious users. The data loss prevention protects against loss from sharing of restricted data, whether accidental or intentional.
For data needing to be directed to a SaaS provider or cloud resource, the traffic is routed over the best possible connection to that provider, and if the data is present in your onsite data center, then it is routed to that resource. Both of which adhere to the policies you set.
Utilizing the Cloud Access Security Broker’s (CASB) features provides visibility and control into users’ actions while accessing SaaS applications. If a device doesn’t meet the security posture you require, a policy can be set so it can only access the resources required to remediate it. If a policy states that a user from a particular department can’t post pictures to a social media site, that can be defined, even if the social media application doesn’t provide that capability natively.
What About You?
The move to SASE is a journey, not a lift and replace overnight solution, which is why it is important to understand that VMware’s SASE solution supports a multi-vendor ecosystem enabling customers the flexibility to build the best of breed solution that meets their networking and security objectives. Customers can add and consume services quickly without reinventing or redesigning their entire infrastructure. Where are you on the journey?