For far too long, organizations have grappled with a flat network architecture which CISOs are realizing is the root of their security problems.
New World, Old Ways
In most cases, enterprises have been relying on a set of proven network security methodologies that were put in place decades ago. But the world has changed dramatically in the interim years. Traditional infrastructures have given way to cloud-powered ones, a crop of modern applications have entered the market, hybrid work has become the new normal, and clever and evolving cyber threats cast a long shadow on enterprises.
The rise and maturation of IoT and OT, and the sweeping adoption of sustainability practices across the industry make matters a tad more complex.
“It is becoming a huge mesh, and that creates a mess for network connectivity,” said Darrin Miller, Distinguished Technical Marketing Engineer, Cisco, at the recent Tech Field Day Extra at Cisco Live US 2023 event.
Although technology has changed root and branch across the board, the processes supporting these new set of solutions are still largely the same.
The flat network architecture is one such example. The flat architecture has many shortcomings. Besides being inherently problematic, it is a hindrance to modern security practices like zero trust network access (ZTNA). The flat model allows open communication between network assets, which the modern policy of restricting user access to certain parts of the network opposes.
But a shift is underway. “Because of ZTNA, a lot of our customers want to move their open network to a default deny one, where you cannot pass a packet or manage the network unless it has a specific policy allowing it. That’s for any number of reasons – ransomware, jump host attacks, etc. People have enough reason to push for it,” said Miller.
The rising cases of cyberattack spell trouble for enterprises relying on outdated and ad hoc security measures, and they know it. As a result, they’re pushing for a segmented architecture that calls for dividing the network into business-based groups like campus, corporate, datacenter, and so on. This partitioning enables greater control over network traffic and the way it flows, allowing operators to limit traffic in one part of the network from reaching other critical parts. The practice eliminates vulnerabilities, and helps limit the scope of damage in cyber incidents.
Joining Policy Islands
One of the fallouts of the broad change in tech is policy complexity. There are more use cases and dynamic environments than ever now. With different policy models and enforcement points for each of these, it’s a sea of siloed and fragmented policy controls. The outcome is an extremely high OpEx, and a slow burning complexity crisis resulting from lack of consistent policy.
Cisco has a way to connect these individual policy islands so that even when network paths are different, there is one common, end-to-end access policy across use cases.
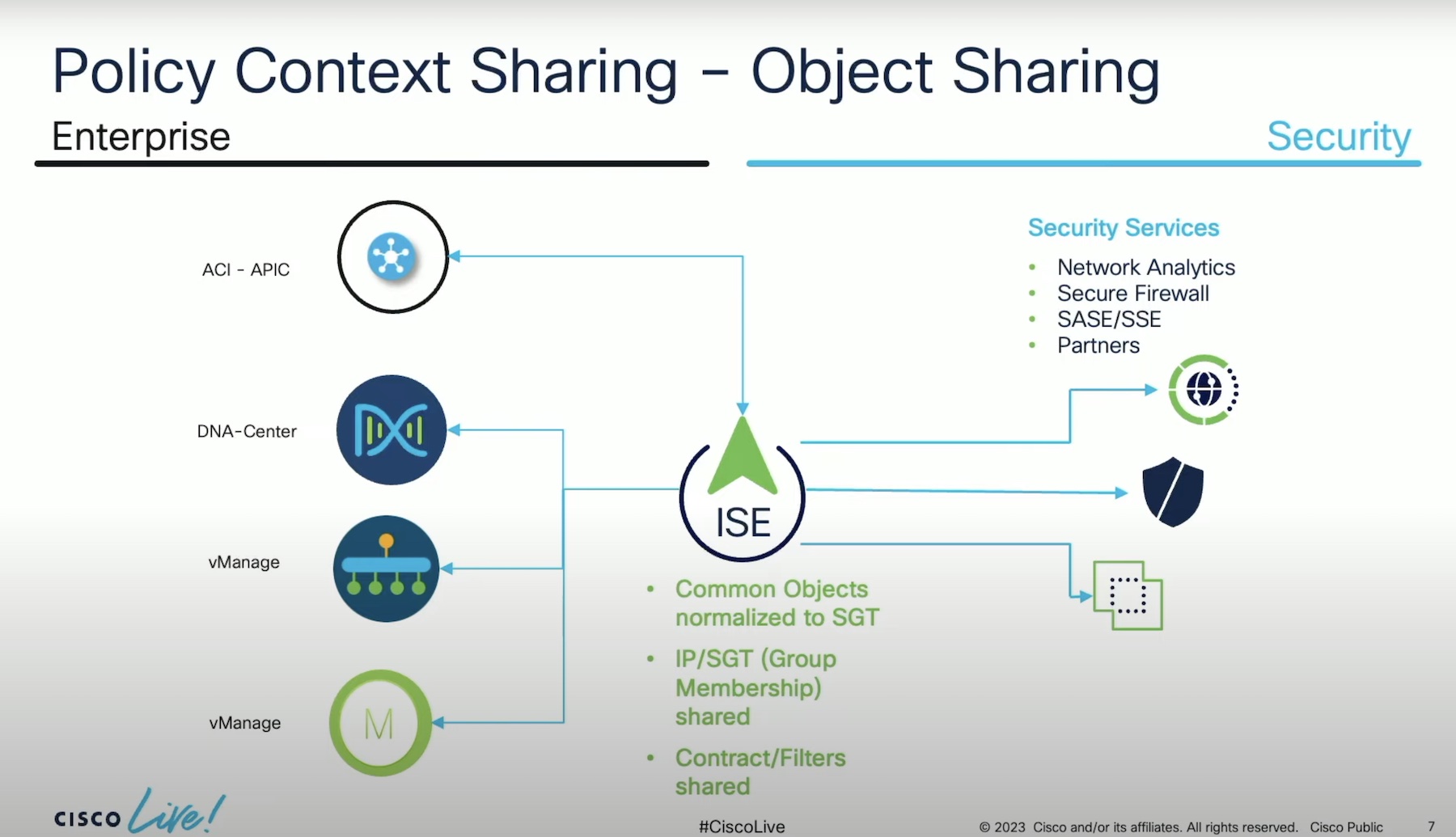
The cornerstone of bridging these islands is policy context sharing. Every product has its own set of policy objects, identity objects and policy models. “The core of what we want to do in a context, is try to take objects out of all those different islands, whether they be a classification of a workload, or classification of an OT device user, and the policy function, the permit, the deny, the ports and protocols, whatever that may be, and share them amongst the different components, so that they can have a common expression of an object,” said Miller.
The benefit of doing that is, first, it enables a centralized policy control that bypasses the management complexity that is plaguing IT teams. Second, studied by industry analysts and consulting firms have shown that context sharing yields vast cost benefits. Depending on the methodology, the OpEx can drop between 50 and a 100%.
But to leverage the full advantage of this, sharing has to happen across the ecosystem. Context sharing benefits from wide and open interoperability which is why Cisco has built an open ecosystem with its direct competitors, leading vendors and third-party SD-WAN companies. This enables users to share context freely within the Cisco networking environment, as well as with a pool of security products from other providers.
In order to enable context sharing between Cisco and third-party products, Cisco leverages the Security Group Tag (SGT). Disparate policies are normalized on SGT, enabling users to have common roles and consistent policy and access, irrespective of the network topology.
Across locations and networks, the security group tag remains the same, and stays the same with users, devices and workloads.
This creates a trust-based policy workflow that enables consistent monitoring, verification and enforcement of policies. Teams can view traffic flows, create groups and identify policies, prior to establishing group-based segmentation policies and applying them. Continuous trust monitoring enables verification of policy effectiveness so that all violations are identified, new policy update requirements are understood, and shadow policies are eliminated.
Wrapping Up
Having a standard security policy is infinitely more efficient than a siloed, multi-vendor situation that only adds to the complexity and cost. The road to better security is not through adding more or fewer products, but putting in place a standard model of enforcement like Cisco’s that spans the enterprise, so that the policy follows the software wherever they go, and not the other way around.
For more, watch Cisco’s full presentation from the recent Tech Field Day Extra at Cisco Live US 2023 event.